1. Introduction
In this tutorial, we’ll define spoofed packets and explain the most common form of spoofing, which is Internet Protocol (IP) spoofing. Then, we’ll give different methods to detect them and present potential limitations.
2. What Are Spoofed Packets?
Spoofing attacks come in various forms, ranging from simple tactics such as email, website, and phone call spoofing to more advanced techniques involving IP addresses, Address Resolution Protocol (ARP), and Domain Name System (DNS) servers.
First, we have IP spoofing, the most known form of packet spoofing. It’s the generation of Internet Protocol (IP) packets in which the source IP address is forged. The attackers manipulate the packet header to impersonate a reliable entity or conceal their true identity.
Then, there’s ARP spoofing that occurs when an attacker sends falsified ARP packets across a local area network. The attacker associates their MAC address with the IP address of a legitimate network device or service. Their goal is to intercept, modify, or even block any data intended for that IP address.
Last but not least, DNS spoofing occurs when the attacker modifies the IP addresses stored in the DNS server with the desired IP addresses. They use it to divert internet traffic to a fraudulent website that closely resembles the genuine destination.
2.1. Spoofing Purposes
The objective of spoofing is to initiate attacks against network hosts, violate data, distribute malware, or evade security controls. Attackers manipulate packet headers and cause their network traffic to appear as if it originates from a different source. This manipulation creates difficulties in determining the true origin of the traffic.
Spoofed packets can serve various malicious purposes, including:
- Distributed Denial-of-Service (DDoS) Attacks: Attackers can flood a target system with a high volume of spoofed packets. This overwhelms the system’s resources and makes it inaccessible to legitimate users
- Session Hijacking: The attacker identifies an active session between a client and a server. Then, they impersonate one of the communicating parties by forging source IP addresses in packets and sending them into the ongoing communication. Hence, they trick the other device into believing they’re the legitimate endpoint of the session
- Man-in-the-middle (MITM) Attacks: An attacker can intercept and modify network traffic between two parties. By spoofing the IP addresses in the packets, they redirect traffic, eavesdrop on communications, or inject malicious content into the communication stream
- Phishing and Social Engineering: Phishing and social engineering attacks can exploit spoofed packets. By forging the source IP address, attackers send packets that mimic legitimate communication from trusted entities, such as banks or service providers. And so, they trick users into revealing sensitive information or performing actions that compromise their security
3. How Does IP Spoofing Work?
Let’s provide some background to clearly understand the problem and then explain the IP spoofing attack.
3.1. Background
IP (Internet Protocol) is a fundamental protocol for transmitting data over the Internet, which is the global network connecting devices worldwide, and enabling communication and data exchange.
So, an IP packet is a unit of data that carries information across the internet. It consists of a header and a payload. The header is the packet part that contains essential information, such as the source and destination IP addresses, protocol information, and the packet length. The payload, on the other hand, contains the actual data content to transmit.
The following figure represents the fields in an IPv4 packet:
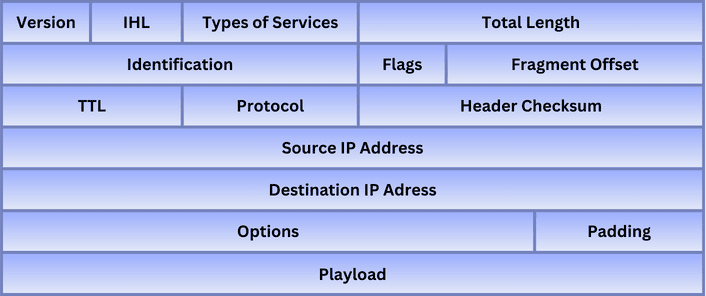
When data is transmitted over the internet, it’s encapsulated into multiple IP packets. These packets travel separately through routers and switches. Then, they’re reassembled at the intended destination. The routers on the internet are the ones that use the IP addresses to correctly route the packets from one network to another until they arrive at the destination network.
3.2. IP Spoofing Attack
In this type of attack, the malicious party creates an IP packet and sends it to the targeted server. To mask their true identity, the attacker replaces the source IP address in the packet with the IP address of another computer. When receiving the packet, the server directs the response towards the forged IP address.
The attacker intercepts this response and then acknowledges it to establish a connection with the server. As a result, they deceive the receiving computer system into believing that the packet originates from a trusted source and within a legitimate network:
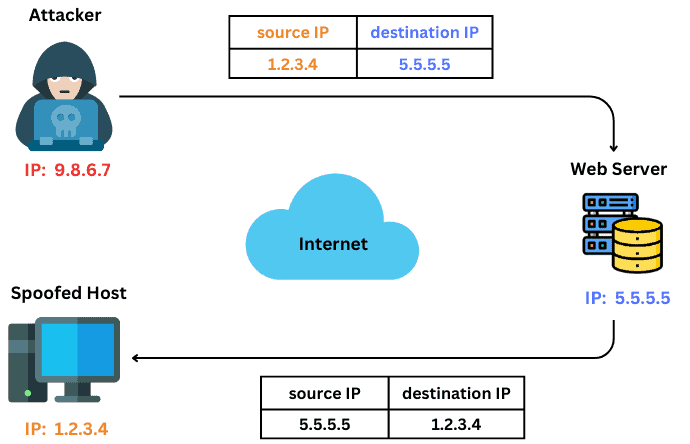
Usually, attackers pay no attention to the response. They only aim to gain unauthorized access to machines and acquire personal information. However, in certain instances, attackers exploit individuals’ internet identities to engage in criminal activities, blackmailing the victims, or directing large-scale distributed denial of service (DDoS) attacks.
4. Techniques to Detect Spoofed Packets
Let’s explain the different techniques to detect spoofed packets in a network:
4.1. Ingress Filtering
Ingress filtering is a packet filtering technique that verifies the authenticity of source IP addresses. It examines incoming packets and compares their source IP addresses with a list of allocated IP address ranges specified for the network. If the packets aren’t valid, they’re automatically dropped. In addition to packet validation, ingress filtering ensures the conformity of the packets to the established routing policies.
4.2. Reverse Path Forwarding (RPF)
Reverse Path Forwarding (RPF) is a common technique used by routers to ensure the integrity of a packet’s source address. It examines the interface through which the packet is received and checks if it arrived on the expected path. If the packet deviates from the anticipated path, it raises an alarm and indicates the the possible occurrence of a malicious spoofing attempt.
4.3. TTL Analysis
Legitimate packet has a Time-to-live (TTL) value that decreases each time it passes through a network device. It indicates the maximum number of hops a packet can traverse in a routing path before the system discards it. When the receiving system identifies a TTL value that’s inconsistent with the expected pattern, it suggests the source IP address has been spoofed.
4.4. Cryptographic Authentication
With cryptographic authentication, the sender digitally signs each packet using a private key. The receiver can then verify the signature using the corresponding public key. If the signature is valid, it provides strong evidence that the claimed sender sent the packet and that its contents haven’t been forged. Otherwise, if a packet is received with an invalid or missing signature, it can reveal a suspicion of an IP spoofing attack.
We can use a variety of cryptographic protocols, such as Internet Protocol Security (IPsec) and Transport Layer Security (TLS).
4.5. Network Flow Analysis
We can use network flow analysis to identify potential spoofed packets by examining flow data, such as source and destination IP addresses, packet sizes, traffic volumes and durations, and protocol usage. For example, an excessive number of connections from a single IP address, shorter flow durations, or unexpected changes in packet size can indicate spoofed packets.
4.6. Network Segmentation
Network segmentation refers to dividing a computer network into smaller and isolated subnetworks. It’s a strategic division that separates critical systems into distinct segments and imposes restrictions on communication between them.
By doing so, we can prevent unauthorized access between different segments and limit the ability of attackers to move laterally within the network. Hence, we may limit the occurrence of spoofing attacks.
4.7. Machine Learning
We can train machine learning algorithms to identify anomalies in network behaviour. Learning the typical communication patterns and behaviours of network devices helps establish baseline behaviour for network traffic. If there are deviations from the established norms, it may indicate spoofed packets.
For example, Intrusion Detection Systems (IDS) can adapt to machine learning techniques to provide insights into potential spoofing attacks.
5. Limitations
We should mention that detecting spoofed packets remains a challenging problem due to the limitations and complexities of network infrastructure. The dynamic nature of Internet routing makes it difficult to filter packets from other transit providers. We can only prevent spoofing where a packet originates.
Moreover, Internet routing is subject to frequent changes as routers dynamically update their routing tables, and packets change their paths. There’s no single entity that has complete visibility or control over the entire routing infrastructure. That’s why, we can’t track spoofed packets consistently.
Also, communication occurring at the network level generally doesn’t leave explicit signs of tampering, and inconsistencies can pass unnoticed.
6. Conclusion
In this article, we defined spoofing attacks and represented the possible detection techniques. To summarize, IP address spoofing attack is among the commonly used methods by attackers. While various measures like packet filtering and cryptographic protocols can mitigate spoofing, detecting spoofed packets remains a challenging problem.
The main reasons are the network infrastructure and routing nature, as well as the evolving spoofing techniques.
