Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’re going to review one of the most common and destructive threats, phishing attacks. Phishing is a term that actually was named after the fishing term due to the way it works. A bait is sent to the user in order to trick him into doing something that he absolutely should not want to do.
A phishing attack uses deceptive messages (e-mails, websites, social media, SMS, voice calls) to trick users into giving up information or installing malware. Phishing uses social engineering techniques to make the user believe that he has received a legit message containing something that may be of their interest. Upon clicking on message links or attachments or opening the message itself, the user might disclose some information. The most common phishing is still through email spam. When they don’t target any specific individual or company we use the term ‘bulk phishing’. However, if the email targets an individual or a specific organization, we call it ‘spear phishing’. The message may contain links to fake websites to trick the user into giving up login credentials, bank accounts details, or even pointing to a man-in-the-middle setup. To track which users fell into the trap, phishing attacks can use HTML image tags with codes embedded in the URLs. That way, the attackers can track whether the emails were opened, identifying active emails, their IP addresses, and client user agents. To make it worse, many email clients, or email reading sites, do not even ask before automatically downloading embedded images. Also, they may try to exploit client vulnerabilities, such as forcing unattended downloads, or code execution. The target vulnerabilities may be from the email client or other software, by attaching or linking to word documents, malicious pdf files, or other media.
The fact is that the most security-aware users may be tricked by good phishing emails. For instance, let’s see some very effective sample fake emails that can be easily crafted: 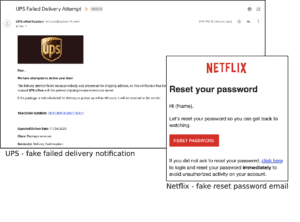 As the SMTP protocol used to send internet emails is quite insecure, it’s very easy to change the sender header “From”. So the attacker may choose any arbitrary mock email as the sender, pretending to be from the alleged origin. However, the inner links most likely will point to fake websites that may even have URL names resembling legitimate ones to help trick the unwary user.
As the SMTP protocol used to send internet emails is quite insecure, it’s very easy to change the sender header “From”. So the attacker may choose any arbitrary mock email as the sender, pretending to be from the alleged origin. However, the inner links most likely will point to fake websites that may even have URL names resembling legitimate ones to help trick the unwary user.
Between 2013 and 2015, both Facebook and Google paid fake bills received through email phishing impersonating a common business partner. According to the disclosed information, the losses may amount to more than 100 million dollars. Since phishing attacks require very little effort and resources, they are one of the first compromise attempts hackers use against organizations. Once they manage to acquire a user’s login credential, they can use it to attain access to extranet systems and corporate VPNs. If they succeed, they move further onto critical business data and resources. That was the case, for instance, of the DNC Hack, back in 2016, and the Linked Spear-Phishing, in 2021. Other famous attacks led to even higher damage. The Sony Pictures Leak, for instance, started with phishing emails with malicious attachments to top-level employees. Once some users fell into the trap, the hackers behind it could spend at least a couple of months downloading sensitive data. They claim to have stolen more than one hundred Terabytes of data, including emails, social security numbers, celebrity personal information, and communication with the company staff.
First of all, phishing has a lot to do with how your user’s behavior. So, the most prone organizations are those whose employees have less security awareness. That way, the first advice is, regardless of any technical measure or tool, to make sure that your users are well aware of how to protect themselves from phishing attempts. In any case, most of the time, even the best-crafted attacks show signs of ill-intentions. Some pointers:
Of course that there are some tools that help avoid phishing attacks or their successful exploitation:
In this tutorial, we’ve discussed dreadful phishing attacks. Phishing attacks require no sophisticated technical expertise or huge resources and can achieve enormous damage. As with almost anything related to information security, it targets the user’s lack of security awareness, taking advantage of their naivety. So, the more important thing to consider is how to train your users so that can be less susceptible to guiling and misleading messages.