Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Authentication vs Authorization
Last updated: May 2, 2023
1. Introduction
In this tutorial, we’ll explain the authentication and authorization concept, both are central to security design. While often used interchangeably, authentication and authorization represent fundamentally different functions. The objective of the tutorial is to explain the definition of authentication and authorization and mention their differences.
We’ll outline various authentication mechanisms commonly used such as Federated Identity, Multi-Factor Authentication, Access Keys, and Key Pairs. We’ll also study Identity and Access Management (IAM) and how IAM Users, Groups, Roles, and Policies tie into the authorization process.
Finally, we’ll study the benefits of user authentication and authorization and navigate towards real-world examples of the concepts.
2. Differences
Authentication and authorization might sound similar, but they are separate security processes in the IAM system. The first element is identity, verifying that a user is a person they claim to be (authentication). The second is access, which involves determining which users can access which resources inside a network (authorization). The major differences are:
| Authentication | Authorization |
|---|---|
| Find out whether users are who they claim to be | Based on predefined rule determines what users can and cannot access |
| Require the user to validate credentials using the established mechanism | Validates whether access is allowed through security policies and rules |
| Prerequisite process before authorization | Access after successful authentication |
| Transmit info through an ID Token | Send through an Access Token |
3. Authentication
Authentication is about having suitably secure mechanisms in place to be able to confirm whether an individual or online user is who they say they are. This defines rules about security information acceptance and decides whether a credential is forwardable to process further. Following are the commonly used mechanisms for authentication.
3.1. Single Factor Authentication (SFA)
SFA is the simplest form of authentication method where the application implements a simple username and password check. With SFA, an application matches one user credential such as a password for a given username as shown in the following diagram:

3.2. Federated Identity
In this authentication process, we look for an identity provider to authenticate a user to get access to an application.
Let’s look at an example for better understanding. Suppose we have the following diagram:
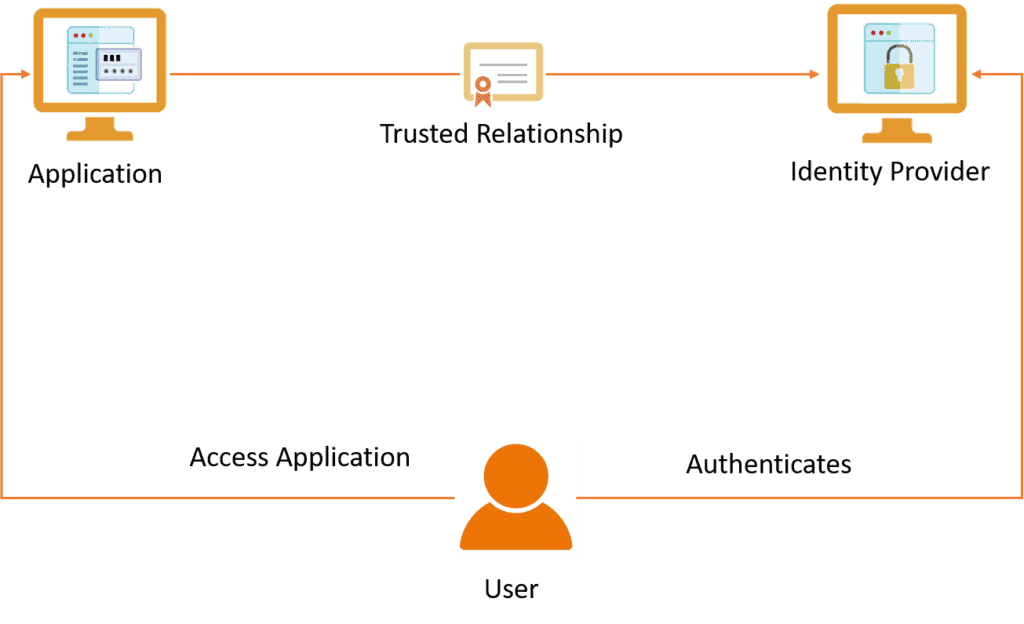
The identity provider can attest to an application requesting user authentication that it had successfully authenticated the user. The application accepts the attestation based on a mutual trust relationship previously established between the application and the identity provider. This identity provider’s authentication for a user eliminates the authentication process between the user and the application.
3.3. Multi-Factor Authentication (MFA)
MFA requires users to provide multiple proofs of their claimed identity. Let’s look at an example for better understanding using the following diagram:
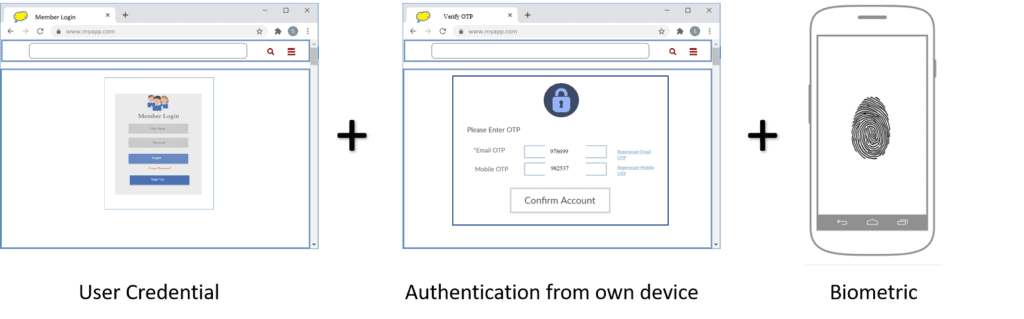
User can complete an authentication process through a combination of any two or all of the following methods:
- User Credential
- Authentication from own device
- Biometrics
The User Credential method consists of a username and a password. The user needs to enter them correctly at the login page of the application.
The Authentication from own device method leverages the fact that people are nearly always in arm’s reach of their mobile device and email. A one-time pin (OTP) is sent by the application for only one session or transaction to the user’s mobile as a short messaging service (SMS) and email. On the verify OTP page of the application, the user will enter the OTP for verification.
The Biometrics method refers to using a physiological characteristic such as finger scan, eye (retinal, iris) scan of the user to complete verification. This requires a specialized application on the user’s mobile.
3.4. Access Keys
Instead of manually entering the User Credential to an application, the asymmetric Access Keys method provides a secured way to send the same information to a remote application. We’ll explain how access keys work using the following diagram:
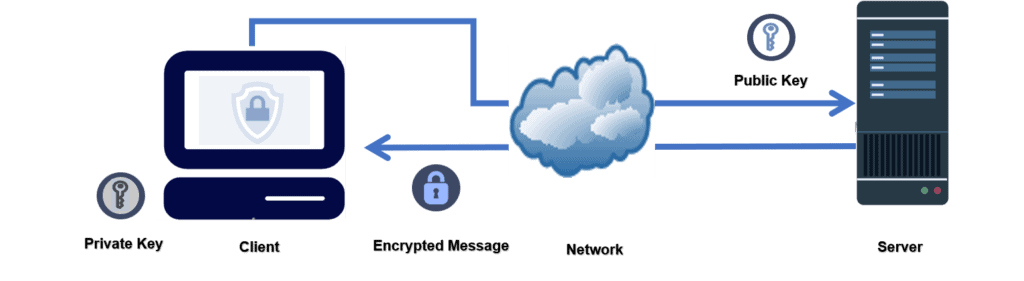
Asymmetric cryptography or public-key cryptography uses a pair of matched keys – a public key and a private key. The access key method uses a public key to encrypt (lock) a message. The encrypted message can only be decrypted (unlocked) by the corresponding private key. A private key (secret) is kept securely in possession of the key generator (client).
To set up a secured connection between a server and a client, generating an access key on the client, is the first step. When a client attempts to access the server using access keys, the server then sends an encrypted (locked) message to the client to decrypt (unlock) the server’s message. A secured connection between the server and the client starts when the client is able to decrypt the server’s message using the private key.
A private key is complex and remains in possession of the key generator only. The private key is difficult to copy, hence the asymmetric access key ensures the identity of the user.
There are several protocols that support this method. Transport Layer Security (TLS), Secure Socket Shell (SSH), and HTTPS are using asymmetric access keys to establish connections.
4. Authorization
Authorization involves the process of providing access to system resources based on a specific set of rules. At this stage, the user should already be identified and authenticated. IAM implementations are often complex and customized for every individual organization using them. Let’s look at the following diagram for a better understanding:
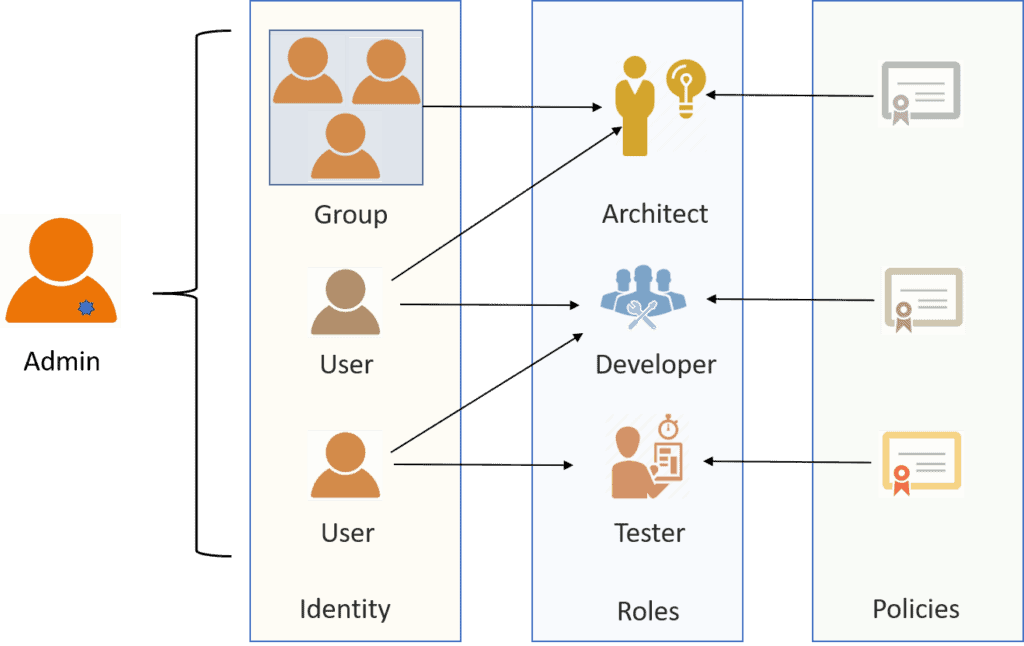
Authorization mechanism enables security system administrators (admin) to specify user (identity) access rights and privileges. The access right means what a user can access, and it is according to the roles. Roles are associated with a category or grouping of users that perform the same set of business functions. One user can have multiple roles.
For example, the same person can work as a developer and a tester. The user role has certain privileges for the actions they can perform. This is governed by a set of rules, called policies. Defining a set of rules (policies) for authorization is complex because sometimes the requirements are tied with business logic that affects performance.
Specifically, the admin controls authorization of user activity by:
- Providing access rights for system resources, services, data, or applications
- Creating logical partitioning of data to safeguard the privacy
- Defining privileges for users as per access-control list (ACL) defined by business logic
5. Benefits
The benefits of the implementation of authentication and authorization are improved security and information sharing. It also identifies and mitigates security risks. Authentication protects information from possible leaks, keeps an eye on accounts. It prevents cybercriminals from gaining access and makes it more difficult for hackers to crack user credentials. It also helps to catch unauthorized activity at an early stage.
Authorization provides centralized access control and lowers the chances of data breaches. Also controls what users can see and do. Further, ensures that a user only has access to what they need. It improves user experience, achieves regulatory compliance, and reduces IT costs.
Besides the above, implementation of the IAM system provides a common platform with ease of use and productivity gains.
6. Conclusion
In this article, we studied two security concepts: authentication, and authorization.
The selection of the type of the correct authentication and authorization method depends on the task we’re performing. It’s appropriate when we’re working on a new system deployment to test some alternative mechanisms and see which one leads to better protection from malicious attacks.
We can refer to a simple SSH application code in Node.js or how to make programmatic calls to AWS to get an idea of authentication and authorization implementation. An article on the Java Authentication and Authorization Service (JAAS) provides a detailed example of both concepts.
Finally, the selection of a specific technique for a given assignment is, therefore, case by case, and we should try some of the mentioned techniques to find out which one works best.