Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: May 20, 2025
In this tutorial, we’ll go through the technical definition of impersonation attacks and the main pattern when executing them. Then, we’ll explain the most common forms of impersonation attacks and give measures to prevent them.
Impersonation is a type of cyberattack where an adversary illicitly identifies as a known person or trusted associate to gain unauthorized access to sensitive resources.
Mainly, the attacker pretends to be someone else and tricks the target into divulging information such as login credentials or into executing actions such as paying invoices and clicking malicious links.
Impersonation attacks are attacks on authentication. Basically, they rely on social engineering and phishing tactics. In the following, we’ll talk about the steps of an impersonation attack and its potential forms.
An impersonation attack is composed of a target, a story, and an impersonated account:
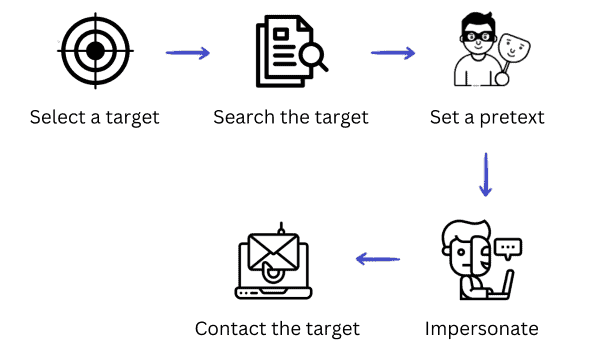
They typically follow these steps:
The attacker begins by choosing a target person, usually from a specific company or organization.
They pick an executive or an employee with access to critical data. Generally, it will be someone working in the accounting, legal, or HR departments.
The attacker studies the target person’s role, responsibilities, and coworkers using online platforms such as LinkedIn and the company website.
The attacker can even go further to find out about the target’s hobbies, address, and family through social media. Their goal is to draw a complete profile of the target to successfully set the trap afterward.
The attacker creates a false asset to fool the target. It can be a spoofed email or a fake social media account.
Pretending to be someone else by imitating or compromising an original account is at the core of an impersonation attack.
At this point, the attacker has already set a convincing outreach story based on the research carried out on the target profile.
Then, they approach the target via email, phone call, or any other communication medium to commit fraud. They’ll ask the target to provide credentials, pay a fake receipt or download a counterfeit app.
There are various forms of impersonation attacks.
Let’s start with the most famous impersonation attack, which is email impersonation. During this attack, the hacker pretends to be someone else (a coworker, a manager, or a friend) and uses a false or hijacked email address. Emails often include malicious links or attachments leading the target to phishing websites or malware installation.
The attacker may also manipulate the target into replying with sensitive information. For example, they can address the target by name, use familiar company language, or share finite details about a recent company event to make the targetted person trust them.
A common example of email impersonation is CEO fraud, also called business email impersonation, in which the attacker impersonates a high-rank executive or manager in the company.
Here, the attacker fabricates a fake website or email with an address that looks similar to the official website. Usually, they choose a trusted and known website or a brand to lure the victim. Also called a lookalike domain, this attack is created by different means, such as misspelling words and replacing some letters with numerals.
In short, the attacker makes slight and almost invisible changes to the domain code to seem legitimate. For example: baelldung.com instead of baeldung.com.
An account takeover means logging into an account with stolen credentials gained by credential stuffing, using malware and various keylogger software, or buying passwords on the dark web. Poor password management also helps the attacker access and steal logging details.
The attacker can use the stolen accounts to send a phishing story to the victim’s social media contacts. More dangerously, the stolen accounts can be financial and banking accounts. The adversary can make purchases or blackmail the target with money.
Here, the attacker changes the IP address of a source packet or hides it. In general, spoofing can take various forms. In addition to IP spoofing, there are also website spoofing and extension spoofing.
The former creates a website layout with a design that appears almost similar to the original website, fooling the target into giving away its personal information. The latter disguises a file and hides its true format to make the victim run an executable malicious file.
The man-in-the-middle (MITM) attack intercepts two communicating parties and impersonates one of them to get illicit access to confidential resources.
For example, the adversary eavesdrops on network traffic between a user and a club membership website. Then, they pose as the website and steal the login credentials.
Phishing attacks also trick people into divulging sensitive and confidential information.
Smishing and vishing are two common types of phishing attacks. They use social engineering strategies. The former uses SMS texts for scams, whereas the latter exploit voice communication as phone calls and voicemails.
5. How to Protect from Impersonation?
Impersonation attacks can be challenging to detect and prevent since they exploit human nature. Still, there are technical and non-technical countermeasures we can implement to reduce the risk:
In this article, we defined impersonation attacks and examined their different forms. To summarize, impersonation means the attacker is posing as someone else to fraud the target. They create a false identity through a fake email, website address, social media account, IP address, or even a fake document format. It is essential to cultivate awareness about these types of attacks and methods to mitigate them.