Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
Obtaining confidential information and spoofing identity are classical objectives of attackers in the digital world. Multiple attacks can have these objectives, such as DDoS and certain malware. Of course, the Internet protocols evolved over the years to avoid these kinds of problems, using, for example, cryptography to secure connections.
However, the attacks also evolved as the prevention and mitigation became more sophisticated. A relevant attack that emerged in this context is the man-in-the-middle (MITM) attack. Man-in-the-middle attacks consist of spoofing the attacker’s identity to the legit entities that aim to communicate yourselves, thus enabling the attacker to intercept messages and access their content.
In this tutorial, we’ll study how man-in-the-middle attacks really work.
At first, we’ll see the typical motivations of an attacker to execute a man-in-the-middle attack. Next, we’ll understand the technical details of this attack. Finally, we’ll see notorious cases of man-in-the-middle attacks in the real world.
Since the Internet emerged and popularized, confidential and sensitive information has been passing through the world wide web daily. Parcels of this information may have financial and strategic value, making them a target for being stolen by hackers.
Furthermore, stealing information may reveal the weakness of a certain system. This information can be then explored by the same hackers to employ different categories of attacks.
At last, intercepting a communication, besides enabling the hackers to get information, allows them to create fake messages and send them assuming the identity of a particular victim. This practice can induce some specific response or cause some deception to the other victims that received the fake message.
In this way, we can summarize the motivations for employing a MITM attack into three points:
We can summarize a man-in-the-middle attack in two main stages: identity spoofing and traffic interception.
Identity spoofing aims to convince the client that an attacker is a legit server of the desired service. In the traffic interception stage, however, the attacker obtains and analyzes the network traffic sent by the client.
We’ll see these stages in detail in the following subsections. It is relevant to highlight that we adopted the client/server architecture to explain the man-in-the-middle attack in this tutorial, but it works in other architectures too.
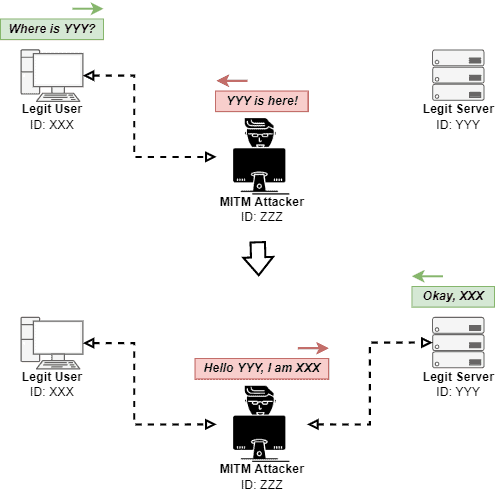
The first objective of the identity spoofing stage is convincing the client that the attacker is actually a legit server of the requested service. From now, the client thinks that he is communicating with a legit server. However, the network traffic is all directed to the attacker.
The attacker receives the requests from the legit client and spoofs your identity again: the attacker communicates with the legit server of the desired service as being the client.
In such a way, the attacker is almost invisible since the client sends coherent requests to the server, and the legit server naturally responds to the client’s requests.
The objective of the identity spoofing stage is to make the attacker intermediate the communication between client and server invisibly. It does not mean that the attacker can not modify data in the network traffic. It means that it should be done convincingly for both client and server.
The following image depicts the described scenario:
Finally, there are different ways to intercept the traffic from the client to the server by the attacker:
Choosing one of these methods depends, for instance, on where the attacker and the victims locate and which protocols they use to communicate with each other.
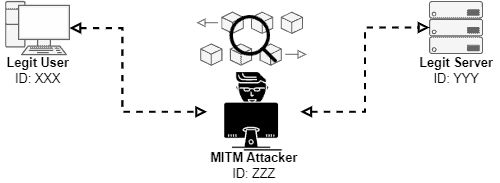
After spoofing your identity to both server and client, the attacker finally acts as the man mediating the communication between two legit entities. It means that the attacker intercepts all the network traffic sent or received in this communication.
However, this stage is far away from being the easy part!
The attacker must keep transparent communication between the client and the server. So, in other words, the legit entities should not note that the traffic an attacker intercepts the communication.
In such a way, if the attacker is only enumerating vulnerabilities or spying on the client, he should avoid degrading the quality of the communication between the legit entities.
On the contrary, if the delay or packet dropping rates, for example, increase too much, the client or server can suspect being attacked. So, they can drop the connection or just stop sending messages.
The following image exemplifies the previously described scenario:
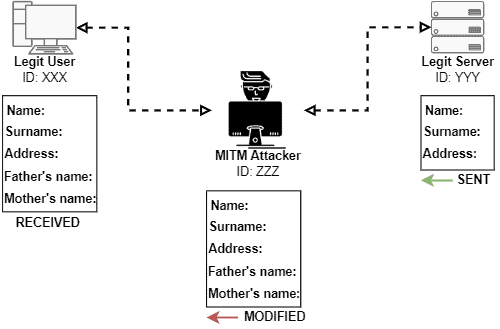
Furthermore, extra caution is taken by attackers when modifying the intercepted network traffic. Thus, the modifications must be convincing enough to induce the client to do some desired action.
Particular examples of actions desired by attackers are: the client providing some specific personal information; causing a deception to the client regarding the accessed service; inducing the client to communicate with another server, usually malicious and controlled by the attacker.
To do that, the attacker can change forms, images, texts, and advertisements sent by the server to the client.
The image next depicts the process of modifying data in an intercepted communication:
In summary, the traffic interception stage, for the attackers, must balance the accomplishment of the objectives of intercepting the communication with keeping this interception transparent.
Although we connect MITM attacks to the digital world, transparently intercepting messages and manipulating them is a historical strategy.
A notorious old MITM is the Babington Plot: a plan to assassinate Queen Elizabeth I (English) in 1586. The MITM attack, in this case, involved double agents and cryptanalysts. So, the letters between Mary Stuart (the conspiracy leader) and other conspirators were intercepted, decoded, leaked to the English crown, and finally delivered to the conspirators.
Another early example of a MITM attack occurred in World War II. The Allies monitored the German radio transmissions continuously. As soon as a German transmission ended, the Allies began to retransmit the same message in the same radiofrequency.
In this way, the Allies’ transmissions were confused with German transmissions. So, the Allies took advantage of this situation to spoof and transmit convenient messages between the retransmitted German messages.
In recent years, we also had several cases of MITM attacks in the digital world.
For example, the DigiNotar register system was breached in 2011, leaking more than five hundred certificates of famous websites such as Google and Skype. Attackers employed these certificates to create mirror websites posing as legit ones. These mirror websites, in turn, could be used to execute MITM attacks.
Another example was the credit score Equifax app in 2017. The app did not appropriately employ the HTTPS protocol. So, attackers were allowed to intercept and obtain data while the users were accessing the app.
In this tutorial, we studied man-in-the-middle attacks. First, we had a look at the principal motivations for executing a MITM attack. So, we saw MITM attacks have two main stages: identity spoofing and traffic interception. We then analyzed each one of these stages in detail. Finally, we identified examples of historical and recent MITM attacks.
Man-in-the-middle attacks concern digital security professionals around the world. The transparency for the user of most of these attacks makes them a real threat to the final users.
In this way, it is very relevant that developers and service maintainers employ countermeasures to avoid MITM as much as possible. Examples of countermeasures are applying robust cryptography protocols and multi-factor and multi-stage authentication.