1. Introduction
Malicious attacks have been developed since the emergence of the Internet. Many of these attacks take advantage of potential architectural vulnerabilities in online services.
Specific characteristics such as server centrality in the client/server architecture and multiple sources in the peer-to-peer architecture are exploitable in different ways.
Among the most famous networked attacks is the Denial of Service (DoS). DoS attacks aim to overload a service available in a network (usually connected to the Internet), thus making it unavailable. It can be executed from a single source or multiple sources (Distributed DoS – DDoS).
In this tutorial, we’ll explore DDoS attacks holistically. First, we’ll study the principles of a DoS attack and understand how they become distributed. Next, we’ll see the different techniques of DDoS and how they work. At last, we’ll discuss the potential consequences of a DDoS.
2. Basics of Denial of Service Attacks
A DoS attack has as main objective to make a networked service unavailable by overloading it. The most usual form to execute that is sending a massive number of malicious requests to the service provider, so many requests that the server just stops responding at some point.
We call massive requesting attacks of flooding DoS. However, there are other techniques of denial of service that exploit specific characteristics of particular services. These techniques, in turn, can make the services unavailable with a reduced number of requests.
To execute a simple DoS attack, the attacker selects a target (typically a server from the client/server architecture) and systematically sends service requests to them. As these requests are fake, the attacker can simply ignore the server responses. So, the attacker avoids overloading himself.
Furthermore, DoS attackers frequently change the origin addresses of their requests to avoid being detected and blocked by the security systems of the server or running in the core network itself. So, it is not unusual for a single attacker to impersonate dozens or hundreds of fake users.
The following image depicts a DoS attack with a high level of abstraction:
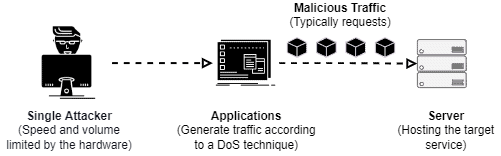
It is relevant to highlight that attackers not only exploit the end service as monolithic software. Actually, they can exploit vulnerabilities of protocols and subsystems that compose the service. In this manner, DoS strategies become more generic and reusable. We’ll see some of these generic exploits in the following sections.
However, even faking lots of users and executing a DoS attack, a single attacker with few computers is still very limited in the amount of traffic generated.
These limitations arise, for example, due to hardware constraints, such as the network card speed. So, to bypass such limitations, attackers use distributed approaches to execute a DoS, then called DDoS.
2.1. Distributed Denial of Service
DoS and DDoS attacks are absolutely similar regarding exploiting strategies used and final objectives. But, adopting multiple, distributed, and not faked sources make the attack much more powerful in many aspects.
First, let’s understand how a DoS attack becomes distributed.
Basically, before trying to make a service unavailable, the attacker must infect lots of computers of legit Internet users. To do that, attackers spread a malware program on the Internet through social engineering, worming, and other infection techniques.
The malware turns the infected computers into bots available to the attackers.
In general, a DDoS malware is discrete in the computer system and doesn’t overload the users’ daily operations, acting only when the DDoS attack starts. So, it is hard for the users to note the presence of malware and try to remove it.
The set of infected computers (bots) compose the attacker’s botnet. Thus, the attacker configures the botnet to execute requests to a server in a coordinated way considering a particular exploit and strategy.
The following image summarily depicts a DDoS attack:
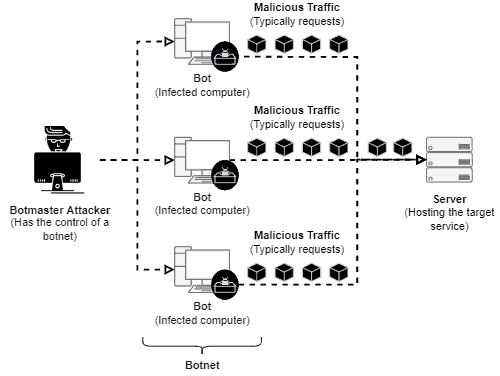
DDoS attacks are, in general, much more efficient than simple DoS attacks. It occurs due to some specific characteristics:
- Hard to mitigate and trace sources: since DDoS attacks come from multiple locations, it is difficult to distinguish which requests are from attackers and which are from legit users
- High speed and traffic volume: DDoS attacks start abruptly, reducing the time available for security systems to react and block them before harming the service. Furthermore, DDoS attacks can massively send network traffic all along
- Sophisticated strategies: with lots of bots in a botnet, attackers develop strategies to elude security systems. For example, make the bots’ behavior similar to the real users, thus trying to make the DDoS look like a natural service overloading
3. Techniques of Denial of Service Attacks
As we previously discussed, DoS and DDoS attacks have the main objective of making a service unavailable. To achieve this objective, attackers typically consider one of two specific goals: exhaust the targeted server resources forcing it to restart, or overloading the communication channel to isolate the server.
Algorithmically, attackers exploit protocols and services’ features to fulfill their objectives. Some of the most known techniques are SYN flood, TTL expiry attacks, amplification attacks, and low-rate targeted attacks. We’ll briefly discuss each of them in the following subsections.
3.1. SYN Flood
The SYN flood attack (sometimes called of half-open attack) exploits the connection establishment scheme of the TCP protocol.
The main idea of this technique is to send lots of synchronization requests to a TCP server without sending any posterior acknowledgments messages to really establish connections.
In such a way, the TCP server still waits for the acknowledgment message from the fake users for a considerable time until dropping the connection due to timeout.
However, the massive number of fake requests consumes the server’s resources. So, the overloaded server ignores connection new requests, including the requests from legit users.
3.2. TTL Expiry Attack
The target of TTL expiry attacks is the routers in the core network. The main idea is to massively send packets that will expire the TTL counter at some specific router.
Since the TTL expires, the router will employ extra computational resources to create and send an “ICMP time exceeds” response.
Since there are lots of packets expiring the TTL at the same router, it becomes overloaded and stops or significatively slowdowns, turning into a bottleneck in the network.
3.3. Amplification Attacks
Amplification attacks consist of spoofing requests with the victim server IP and thus sending them to services that generate large amounts of traffic as the response.
Examples of services that can be exploited to amplify attacks are based on DNS and NTP.
In the DNS scenario, the attacker exploits the responses of the DNS lookup operations to generate malicious traffic.
In the NTP case, attackers usually exploit the operation called moonlist, which sends information about hundred hosts that recently have requested the NTP server. Thus, a simple and small request results in a large amount of data transferred.
3.4. Low-rate Targeted Attacks
Unlike the other attack techniques in this tutorial, which are generic attacks, low-rate targeted attacks exploit distinct features of very particular services.
Low-rate attacks do not have the purpose of flooding the victims with network traffic. Actually, the main idea is to send the minimum amount of traffic but cause the maximum impact on the service.
For instance, let’s consider a networked AV service. The attackers can forge network packets with many signatures and patterns checked by the AV. So, the forged packets require much more computational resources to be processed by the AV than the average in normal conditions.
Since different AVs may have different behaviors, the attacker will need to make a new analysis and probably forge another attacking packet to exploit heterogeneous AV servers.
The principal advantage to the attacker is that it is easier to mimic legit users’ behavior in low-rate attacks. So, it is harder for security systems to detect and block malicious sources.
4. The Potential Consequences
We saw in the last sections that the most expected consequence from a denial of service attack is to make a service unavailable. However, there are other potential side-effects and purposes related to DoS and DDoS attacks:
- Distraction: denial of service attacks can be used as a distraction. For example, a DDoS can hide exploitation of a determined system vulnerability that enables the attacker to intrude on it
- Data leakage: services can leak data as a consequence of being overloaded. It occurred, for example, in the first switches that, when overloaded, would send data to all ports
- Service Tracking: a single server may host multiple services at the same time. Overloading one of these services and forcing the server to reboot will make all hosted services reboot. So, attackers can track this behavior to detect hidden services and shared resources
5. Conclusion
In this tutorial, we studied denial of service attacks. At first, we reviewed the basics of both DoS and DDoS. Next, we saw that there are several techniques to execute a denial of service attack. Thus, we particularly explored the most known ones: syn flood, TTL expiry, amplification, and low-rate targeted attacks. Finally, we had a look at potential side-effects consequences of a (D)DoS.
We could notice that denial of service attacks are a real threat in the digital world. If a server provides service over the Internet, it naturally becomes a possible target for a DoS or DDoS.
Furthermore, mitigating denial of service attacks is not a trivial task. There exist several different (D)DoS techniques which require different detection methods and countermeasures.
So, large investments in security may be necessary to keep networked services always available.