1. Introduction
In this tutorial, we’ll see Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). The interest in attacking users and providers has been increasing as the networks get more and more popular, as well as the number of threats created by malicious entities.
So, to mitigate these threats, we should consider using security solutions, such as IDSes and IPSes.
In the following section, we’ll see some background about network security, thus understanding the origin and motivation of IDS and IPS solutions. In this way, we’ll specifically talk about both IDSes and IPSes. Finally, we’ll compare these security solutions in a systematic summary.
2. Background
Computer networks have become a crucial instrument for all the spheres of our everyday life. From working to our personal activities, almost everything we do uses (at least partially or indirectly) some network, such as the Internet.
The previously commented scenario also got the attention of malicious entities that exploit network vulnerabilities to achieve some advantage.
These malicious entities conduct different attacks trying to, for example, make networked services unavailable, break security systems, steal information, and spoof connections. Common examples of such attacks follow:
- Distributed Denial of Service (DDoS): the main objective of a DDoS attack is to make a networked service unavailable by overloading it. Attackers can also use it as a distraction or to make other attacks viable
- Man-In-The-Middle (MITM): attack aiming to take control of the message exchange in connections established between benign entities. MITM includes phases of identity spoofing and network traffic interception
- Port Scan: an attack that scans ports in a network aiming to find vulnerabilities and exploits that could enable other attacks
Of course, multiple prevention systems and mitigation solutions for these attacks also emerged.
Among these systems and solutions, we can cite the antivirus and firewalls. Moreover, we also have secure network topologies, such as the DMZ-based ones.
But, in this tutorial, we’ll focus on studying Intrusion Detection Systems (IDSes) and Intrusion Prevention Systems (IPSes). So, in the following sections, we’ll discuss how these solutions operate in the network and how they prevent us from multiple threats.
3. Intrusion Detection Systems
First of all, let’s understand what an IDS is.
In short, we can face IDSes as security solutions that work as monitoring systems. The objective of such systems is to detect suspicious activities, thus triggering alerts or taking actions to inform other security systems about them.
A relevant characteristic of IDSes is that they do not mitigate potential attacks. Our main objective here is only to detect potential threats.
Due to these characteristics, IDSes may not work online or inline. By online, we mean a solution that processes data as soon as it arrives. With inline, however, we refer to a solution that processes data as part of a broader service.
In this manner, IDSes can work analyzing copies of already processed data by other systems.
The image next depicts, on a high level, an IDS analyzing incoming and outgoing network traffic:
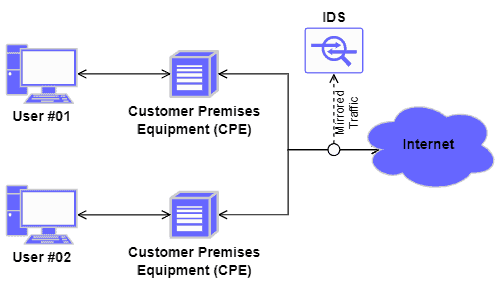
3.1. IDS Categories
We can classify IDSes in some categories. The first category regards the environment in which the IDSes will work:
- Network-based Intrusion Detection System (NIDS): commonly working as a network function, a NIDS has as its objective inspecting network traffic and networking events. In this way, NIDSes can inspect from headers to payloads of frames and packets, working in different network layers
- Host-based Intrusion Detection System (HIDS): different from a NIDS, which works for a network, a HIDS is tailored to inspect events and data of a particular endpoint. So, this host-based inspection can include, for example, the incoming and outgoing network traffic, operating systems logs, and running processes behavior
In addition to the previously presented categorization, we can also categorize IDSes in terms of how they identify potential threats:
- Signature-based Detection: searching for signatures means looking for fingerprints and patterns in data and processes that are potentially malicious. So, signature-based IDSes, in summary, compare the input data with a list of previously known malicious patterns
- Anomaly-based Detection: IDSes in this category build a model representing the expected behavior of the network or a system. So, time by time, the IDS checks the current behavior of the network or system. Thus, if there is a significant change in the expected behavior, the IDS triggers an alert informing that potentially malicious activity is occurring
It is relevant to highlight that an IDS can execute both signature-based and anomaly-based inspections, acting as a hybrid solution. Hybrid IDSes are sophisticated and typically less error-prone.
4. Intrusion Prevention Systems
After studying IDSes, studying IPSes becomes much easier. Actually, IDSes and IPSes are closely related to each other, for example, by sharing the same categories: signature-based IPS and anomaly-based IPS; network-based IPS (NIPS) and host-based IPS (HIPS).
So, what are the characteristics that differentiate an IDS from an IPS?
The most relevant specific characteristic of an IPS is that it can take some actions to mitigate potential attacks. For comparison, an IDS works inspecting traffic or processes, thus triggering alerts, but it does not mitigate attacks or deal with threats.
Due to the previously described characteristic, IPSes must work in line with the traffic and process execution. Thus, they should act before the traffic and processes are delivered or executed.
The following image exemplifies the deployment of a NIPS in a simple network topology:
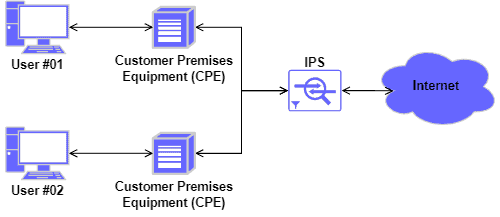
Finally, the most representative action taken by an IPS to mitigate attacks is blocking them. It can apply to the delivery of potentially malicious traffic and the execution of potentially malicious processes.
But, in addition to blocking actions, there are other mitigation alternatives for an IPS, such as using traffic shaping and packet wash strategies in the suspicious network traffic.
5. Systematic Summary
With the increasing number of threats in the digital world, many security systems emerged to keep users and service providers safe. Among these systems are the IDSes and IPSes.
IDSes and IPSes can both work at a networking or host level. In particular, IDSes aim to detect suspicious activities and trigger alerts. IPSes, in turn, besides detecting suspicious activities, can also take actions to mitigate possible attacks.
It is relevant to highlight that there is no definite answer to which system is better: IDS or IPS. It depends on the objective of using these systems and the deployment scenario.
For example, an IDS does not mitigate attacks. However, it can use mirrored network traffic and offline logs for the inspection routines. So, the delay imposed on the services is negligible.
An IPS, in turn, can mitigate attacks. However, it must process the network traffic and check the processes before they are delivered or executed. So, the extra delay imposed by an IPS is typically much higher than an IDS.
The following table summarizes and compares some characteristics of IDSes and IPSes.
6. Conclusion
In this tutorial, we studied Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS). At first, we saw some background concepts that motivated the creation of IDSes and IPSes. Thus, we specifically explored the characteristics and categories of both IDSes and IPSes. Finally, we compared these security systems in a systematic summary.
We can conclude that, with the multiple threats of the digital world, IDSes and IPSes are necessary elements to make networks and services safer. Of course, other security systems usually work with IDSes and IPSes, but these latter ones play a crucial role in a complete security ecosystem.