Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 26, 2025
Passwords are the keys to our online existence. If our passwords fall into the wrong hands, it may create havoc. Password management involves setting and storing safe passwords for our internet-based accounts and endpoints.
In this tutorial, we’ll discuss why password management is important, and how to build reliable login credentials. Further, we’ll discuss how to use a password management tool to maintain them secure and organized.
Security breaches such as theft of identities, attacks by ransomware, and cyber spying are some of the network weaknesses that could have serious implications. Therefore, protecting a network is critical. Above all, it lowers the likelihood of unforeseen legal, regulatory, or reputational implications for system administrators and managers.
Let’s discuss some of the key benefits:
Passwords are the first defense against intruders because login credentials are entry keys to access network resources and systems as per access rules. They’re the most simple and inexpensive to set up and maintain compared to other options like biometrics, encryption, or multi-factor authentication (MFA).
Let’s see what are the most frequent password errors that help hackers get access to our accounts:
Hackers could exploit our compromised accounts to steal our identity and distribute malware. Furthermore, the majority of hacks might have been avoided by following proper security procedures. Cybercriminals can readily assume or obtain account information through social media.
Further, passwords are the keys to our online accounts. As a result, if they are easy to guess, or stolen, we end up exposing our information to threats. Therefore, we need a strong password that secures our information using the following criteria:
| Criteria | Rule | Benefits |
| Complexity | Combination of uppercase, lowercase letters, numbers and symbols | A random password is difficult to compromise. |
| Length | More than 12 characters | Difficult to guess or crack |
| Uniqueness | Use of different passwords for different accounts. | This reduces the risk of compromise |
| Frequency | Periodically change passwords | This minimizes the risk of compromise even if a hacker gets access to older passwords. |
| Verification | Add multiple factors to verify the identity | This involves an improved secured access mechanism to verify passwords. |
We’ll be required to make the password more challenging to guess to prevent password theft. Let’s discuss how we can overcome these password thefts while still creating secure and distinctive login credentials.
Below are a few pointers to prevent password thefts:
Authentication is a method through which a system ensures that they’re really who they claim to be.
Single Sign-On (SSO) and Multifactor Authentication (MFA) are two extensively used authentication techniques.
While SSO and MFA serve distinct purposes, they are not mutually exclusive. Moreover, SSO and MFA can collaborate to establish a robust and user-friendly authentication environment.
Let’s discuss in detail about both SSO and MFA.
SSO is a user authentication technique that allows users to use different apps and networks with a single set of usernames and passwords. Additionally, SSO simplifies the user login process as shown below:
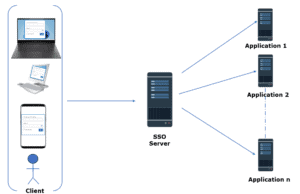
Let’s consider that a user wants to access an application using SSO. The application sends a request to the SSO server to authenticate the user. Upon validating the credentials, the SSO server confirms the authentication and grants access to the application.
Moreover, this simplified technique greatly improves the user’s experience by removing the requirement to balance and handle several login details. Additionally, SSO enables access to all SSO-authenticated applications and websites without logging in again.
MFA raises a safety bar by requiring users to give extra confirmation factors in addition to regular passwords. Further, it adds layers of security through multiple authentication factors as shown below:
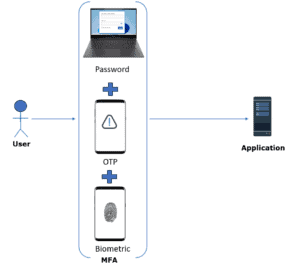
MFA is usually an amalgamation of a password, a mobile device for OTP, and an identity. The password is something the user understands. Mobile devices are things they own. A user’s identity describes who they are.
Password management tool allows users to store credentials in a straightforward, safe method and instantly access them when needed.
As Users, we can manage our credentials from a single, centralized location with the help of a password management tool. Further, we use them for much more than just saving our login credentials.
A password management tool helps to select and rotate complex passwords regularly. Furthermore, it enforces several cybersecurity guidelines.
For example, the password should be at least 20 characters long. Include numbers, symbols, upper and lower case letters. Further, during deboarding an employee, reset passwords or close accounts. Additionally, use the same password for linked network systems and accounts.
The key components of the password management tool are shown in the figure below:
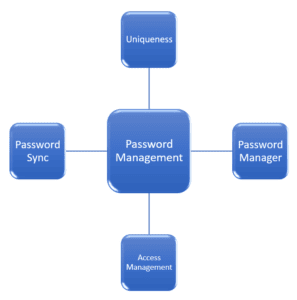
Managing password techniques differs based on the network’s configuration and end-user needs. However, the following are the key components of a password management tool :
Passwords manager allows easy login to websites and applications by using previously saved passwords. Further, the password manager maintains encrypted passwords for every application and uses them as needed.
Users often access different applications via the Internet. The password manager uses cloud sync to provide credentials to applications accessed over the internet.
Password management tool is an all-encompassing solution to safeguard user’s credentials. It also automates the adoption of password management standards.
Further, it eliminates the need for rigorous training and stringent compliance. Following are some of the best practices to follow with an efficient password management tool:
In this article, we discussed about password management, one of the key aspects of network security. A password manager keeps our passwords safe and organized. Our online accounts and devices need to be protected against breaches to have a better online experience.
Incorporating SSO with the MFA and an efficient password management tool achieves a harmonic balance of user comfort and increased security.