Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: July 6, 2024
In this tutorial, we’ll take a look at watering hole attacks. We’ll see what a watering hole attack is, how it’s implemented, and study some real-world cases. Finally, we’ll discuss the latest techniques utilized by attackers and also touch on measures we can take to protect our systems.
Let’s start by discussing what a watering hole attack is and what it may include.
Let’s assume that we have a very well-guarded and secure organization in terms of cybersecurity. Any attack on our infrastructure will likely fail, and our network defense is impregnable. The day-to-day network traffic of this organization may look something like this:
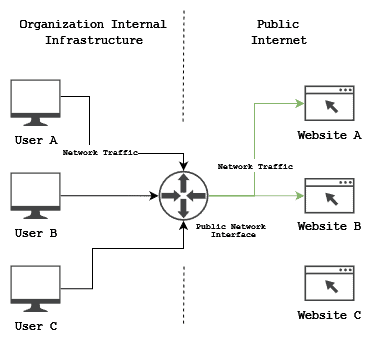
Users visit third-party internet websites using organization infrastructures.
A Watering Hole Attack compromises the systems of organization users indirectly, using infected websites visited by said users. It is an attempt to override the actual security measures of the organization and exploit insecure websites to infect the user’s systems and gain access to the organization in that way.
Even if our infrastructure’s security is superb, the safety of third-party websites isn’t guaranteed, and that is what attackers count on using to infiltrate our organization. The attack strategy is cleverly named after the behavior of animals that wait near watering holes for their prey.
The anatomy of a watering hole attack consists of a series of steps, from identifying target audiences to gaining unauthorized access to target systems.
First, attackers target a specific group or organization and gather information on its online behavior, habits, and preferences. This effort’s goal is to accumulate a set of online websites that users of the selected group tend to use and visit the most. With this insight, attackers pick out websites from this list and try to compromise them.
Following this step is the actual exploitation of these websites. Website owners are also usually unaware of the attacks, making them harder to detect. Malicious code is then injected into the websites’ infrastructures. This code serves as a delivery mechanism for malware to the systems of unsuspecting visitors.
Furthermore, well-thought-out watering hole attacks craft their code so that they only infect users from the target organizations to avoid broader system infections that increase the risk of detection:
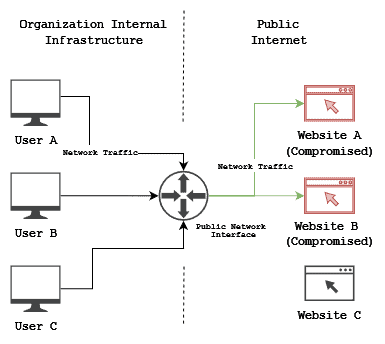
With the malware in place, users visit the websites and infect their systems. The code injected into the websites is specially crafted to try and avoid any detection mechanisms (i.e., firewalls, antivirus software, intrusion detection mechanisms (IDS), etc.) until reaching their destination.
Once malware infects users’ computers, attackers start exploiting and gaining access. This essentially marks the initiation of the attack, opening avenues for data exfiltration, surveillance, or the installation of additional malware:
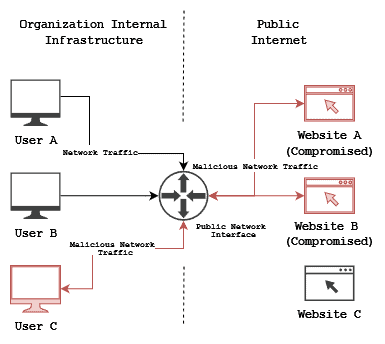
Lastly, a very important last piece of successful attacks is covering their tracks. To prolong their presence and avoid detection, attackers employ tactics to cover their tracks. The ability to remain undetected is paramount for the success of watering hole attacks, making this phase critical. Such a step typically involves removing digital traces, manipulating logs, etc.
In recent years, several real-world cases have used a watering hole attack to gain access to an organization. Studying some of them can give us a better understanding of both the end goals and the process of these attacks.
In the CVE-2014-0322 exploit in 2014, a popular U.S. Veterans of Foreign Wars (VFW) website was compromised to host a zero-day Internet Explorer exploit (CVE-2014-0322). The exploit contained a previously unknown use-after-free vulnerability and infected the website. Visitors to the site, primarily military personnel and defense contractors, unknowingly downloaded malware onto their systems, allowing attackers to conduct espionage and exfiltrate valuable information.
Also, in 2014, the Darkhotel attack happened. Darkhotel, a sophisticated APT group, employed watering hole attacks as part of its espionage campaign targeting executives traveling in Asia. The attackers compromised hotel Wi-Fi networks and injected malicious code into legitimate websites frequently visited by their high-profile targets. This led to the compromise of many devices of unaware targets surfing the web.
Operation Aurora is one of the earliest and most notable watering hole attacks. Operation Aurora targeted several major corporations in 2009, including Google, Adobe, and Juniper Networks. The attackers compromised legitimate websites frequented by employees of these companies, exploiting vulnerabilities in Internet Explorer to deliver malware and gain unauthorized access to sensitive data.
The common factor in all the above scenarios is that the attackers never directly compromise the target organization or people’s devices – they only attack commonly used third-party websites. This is what distinguishes them and turns them into watering hole attacks.
The ever-evolving nature of cyber threats demands an exploration of the latest tactics and techniques employed by attackers in watering hole campaigns.
Picking the correct websites to compromise is a big part of an attack on its own. Balancing between frequently visited sites and sites that have holes in their defenses is crucial. A widely visited and well-maintained site is less likely to be compromised, but compromising a site that no target will visit is worthless.
As for the actual website compromisation, the techniques are similar to standard web exploitation techniques. Attackers often leverage zero-day vulnerabilities, polymorphic malware, or deploy sophisticated social engineering techniques to gain initial access to targeted websites.
Zero-day vulnerabilities could be used if the attack is deemed to be worth it, as a zero-day exploit is “burned” after use. This happened in the CVE-2014-0322 exploit we mentioned earlier. It’s also probable that attackers use more widely known exploits on the websites and the web browsers if possible. Attackers aim to balance between exploit strength and popularity, as antivirus software usually includes well-known exploits’ signatures.
The nature of the watering hole attacks usually requires malware to reside in the victim’s system for a longer period. Attackers deploy APTs (Advanced Persistent Threats) in systems for continuous access and espionage. This, in turn, means that malware needs to hide from detection mechanisms constantly. Polymorphic malware plays a big part here. Polymorphic malware, which dynamically changes its code to evade traditional signature-based detection methods, is an essential and sophisticated technique that serious watering hole attacks utilize.
In addition to technical methods, attackers exploit human vulnerabilities in watering hole attacks by crafting convincing phishing lures and impersonating trusted entities. These tactics leverage human trust, increasing the effectiveness of leading users to compromised sites and facilitating the attackers’ objectives.
Mitigating watering hole attacks requires a strategic approach, as it’s not a simple task. Watering hole attacks do not rely solely on the security of the organization’s infrastructure, making them especially tricky to deal with.
Firstly, organizations should invest in robust web filtering solutions that can identify and block access to potentially malicious websites. Regular updates to these filters and incorporating the latest threat intelligence are essential to fortify against evolving attacks. Attackers gain their foothold using malicious sites, so the organization should identify and preemptively block them.
User awareness training is a critical element in the mitigation strategy. Educating employees on the risks of visiting unfamiliar websites and exercising caution when encountering unknown links helps create a proactive culture. With a heightened sense of cybersecurity awareness among personnel, organizations can reduce the likelihood of falling victim to watering hole attacks.
In addition, maintaining the overall resilience of digital systems involves diligently applying software updates and security patches. Outdated systems often expose vulnerabilities that attackers exploit to execute watering hole attacks. Regular updates significantly boost an organization’s ability to deal with potential threats, enhancing the security of its infrastructure.
In this article, we looked at what a watering hole attack is. We saw how we could infect systems from another target organization by compromising third-party websites.
We saw three major watering hole attack incidents from real life and discussed the techniques utilized within them. From zero-day vulnerabilities and polymorphic malware to traditional social engineering, we saw what the backbone of such an attack consists of. After discussing mitigation for this obscure attack, we concluded that web filtering and user awareness are the two key strategies to shield organizations.