Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll talk about a method used by cybercriminals to steal information and conduct attacks: spam. We’ll demonstrate how a spam message work.
Finally, we’ll present the impacts and important techniques for handling spam messages.
Spam is the digital equivalent of junk mail, comprising unsolicited messages that are sent to a large number of recipients at once. They can be sent via email, text messages, social media, or instant messaging platforms. Additionally, spam may contain various types of content, such as advertisements, scams, phishing attempts, or malware.
Spam can be a significant threat to individuals and organizations. Phishing scams can trick people into divulging sensitive information, such as passwords or financial details. Furthermore, malware can infect computers and steal data, causing significant damage.
Various anti-spam measures have been developed to combat spam, including spam filters, blacklists, and anti-spam laws. Despite these efforts, spammers continue to find ways to evade detection and send spam messages. Therefore, it’s essential to remain vigilant and take steps to protect from spam. Furthermore, avoiding clicking on suspicious links or downloading attachments from unknown senders is recommended.
Spam works by exploiting the ease of sending messages via digital channels such as email, text messages, social media, and instant messaging platforms. Additionally, spammers use automated software programs to send large volumes of messages to a wide range of recipients without their permission. Now let’s discuss how a spam message typically works:
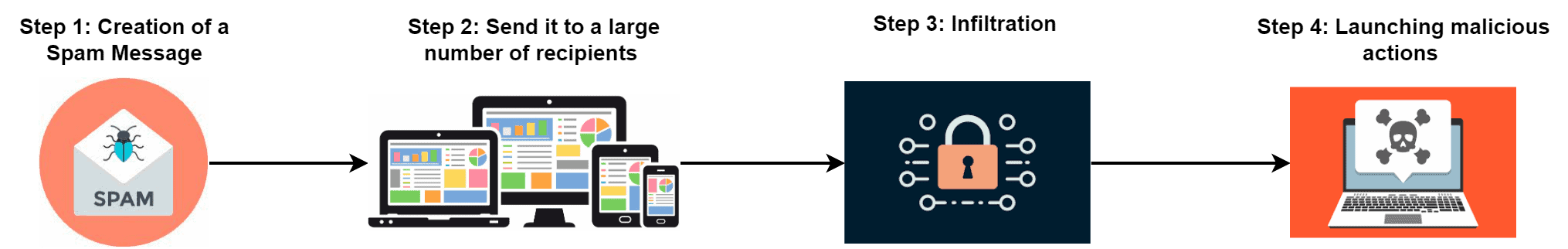
The first step is the creation of a spam message. The attacker creates a spam message based on some objectives. The objective might be extracting sensitive information or exploiting particular vulnerabilities. As soon as the spam message is ready, the attacker sends this message to a large number of recipients.
The next crucial step is to deliver the spam message to the user’s inbox by bypassing the system’s security measures. Spammers execute this step using various approaches such as social engineering tactics, phishing attacks, or exploiting vulnerabilities in email or messaging software.
Spammers often use tactics such as creating fake email addresses and spoofing email headers to make messages appear to come from legitimate sources. They may also use bots or fake accounts to post spam messages on social media platforms or instant messaging apps. Additionally, spammers utilize the strategy of targeted messaging, sending messages to individuals or groups based on their interests, demographics, or online behavior.
Once the spam message has infiltrated the system, it can significantly increase traffic on the network. This can cause congestion and slow down the system’s performance, making it difficult for users to access the necessary resources.
Additionally, if a user clicks the spam message, it can launch various malicious actions such as social engineering, malware distribution, Distributed Denial of Service (DDoS) attack, and backdoor installation. Using social engineering techniques, spammers can deceive people into disclosing sensitive information, such as usernames, passwords, or credit card details.
Furthermore, spam messages may contain links to websites that contain malware, such as viruses, trojans, or worms. When users click these links, the malware may infect their system and compromise security. Additionally, spammers may use botnets to launch DDoS attacks on the system. A botnet is a network of compromised devices that can be used to flood the system with traffic, causing it to crash or become unresponsive.
Finally, spammers may use spam messages to install backdoors in the system. A backdoor is a hidden entry point that allows unauthorized access to the system. Once the backdoor is installed, the spammers can access the system anytime, steal sensitive information, or launch further attacks.
Spam can have various impacts on a system, ranging from minor inconveniences to serious security threats. Let’s discuss some of the ways spam can impact a system:
| Impacts | Description |
|---|---|
| Resource consumption | Spam messages can consume system resources, such as storage space, bandwidth, and processing power. Therefore, they can slow down the systems |
| Email servers overload | Spam messages can overload email servers, causing delays or disruptions in email delivery. This can affect individuals and organizations, especially those that rely on email for communication |
| Malware infection | Some spam messages contain malware, which can infect a system and cause damage. Malware can steal sensitive information, such as passwords, financial data |
| Phishing | Spam messages are intended to deceive recipients into disclosing personal information or login credentials. This can lead to identity theft, financial loss, or other security breaches |
| Reputation damage | If a system sends out spam messages, it can damage its reputation and affect its ability to communicate with legitimate users. This can lead to email providers or Internet service providers (ISPs) blocking or blacklisting the system |
Overall, spam can seriously impact a system’s performance, security, and reputation. Therefore, it’s essential to protect systems from spam, such as using spam filters, reporting spam messages, and educating users on how to identify and avoid spam messages.
There’re various techniques and strategies to handle spam messages. Let’s discuss some of the most effective techniques.
One of the common approaches for detecting spam messages is to use spam filters. Spam filters are computer applications that can recognize and block spam messages. Moreover, major email and messaging service providers use spam filters that analyze messages for suspicious content or characteristics. Furthermore, users can also install anti-spam software on their devices to block spam messages.
Another effective approach for handling spam messages is to create rules for receiving emails. It allows users to automatically filter incoming messages based on specific criteria, such as sender, subject line, or message content. This can help users to sort legitimate messages from spam.
In order to handle spam messages, it’s highly recommended not to click on suspicious links or download attachments. Spammers often include links or attachments in their messages that can contain malware or phishing scams. Users should refrain from opening files or clicking links in emails from unknown senders or messages that seem dubious.
Additionally, users can report spam messages to their email or messaging provider. This helps providers identify and block spam messages.
Finally, educating users on how to identify and avoid spam messages is important to prevent them from falling victim to scams. Users should be aware of common tactics used by spammers and how to recognize suspicious messages.
Therefore, handling spam messages requires a combination of technical measures as well as user awareness. By taking these steps, users can protect themselves from spam and reduce its adverse impacts on their systems.
In this tutorial, we discussed a technique spammers use to steal sensitive data and launch cyber attacks: spam. We demonstrated how a spam message work. Finally, we presented the impacts and important techniques for handling spam messages.