Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Differences Between Network-level and Application-level Information Security
Last updated: March 18, 2024
1. Overview
In this tutorial, we’ll discuss two types of information security: network-level and application-level security.
Finally, we’ll present the core differences between them.
2. Information Security
Information security is a critical component of modern technology. Additionally, it’s essential to protect data and systems from malicious actors. Furthermore, it refers to the practices used to protect electronic data and information systems from unauthorized access, use, disclosure, disruption, modification, or destruction.
Further, it includes measures to prevent cyberattacks and ensure the confidentiality, integrity, and availability of information. Information security is crucial for businesses, government organizations, and individuals to protect sensitive information. Additionally, implementing an effective information security plan can prevent financial and reputational damage.
There’re several types of information security, such as network, cloud, application, data, and endpoint. Furthermore, we’ll discuss network and application-level information security in detail.
3. Network-level Information Security
3.1. Introduction
Network-level security (NLS) is an approach to enhance the existing network security. Additionally, it makes use of the network infrastructure as a means of protecting systems and data from cyberattacks. Furthermore, NLS is a comprehensive cybersecurity strategy that relies on multiple layers of security to protect systems and data from cyberattacks.
Network-level information security refers to the measures to protect a computer network from unauthorized access. Additionally, it preserves the confidentiality, integrity, and availability of data transmitted over the network.
Let’s look at an example where the attacker launches an attack using the network. Here, the attacker can extract the information and violate data integrity:
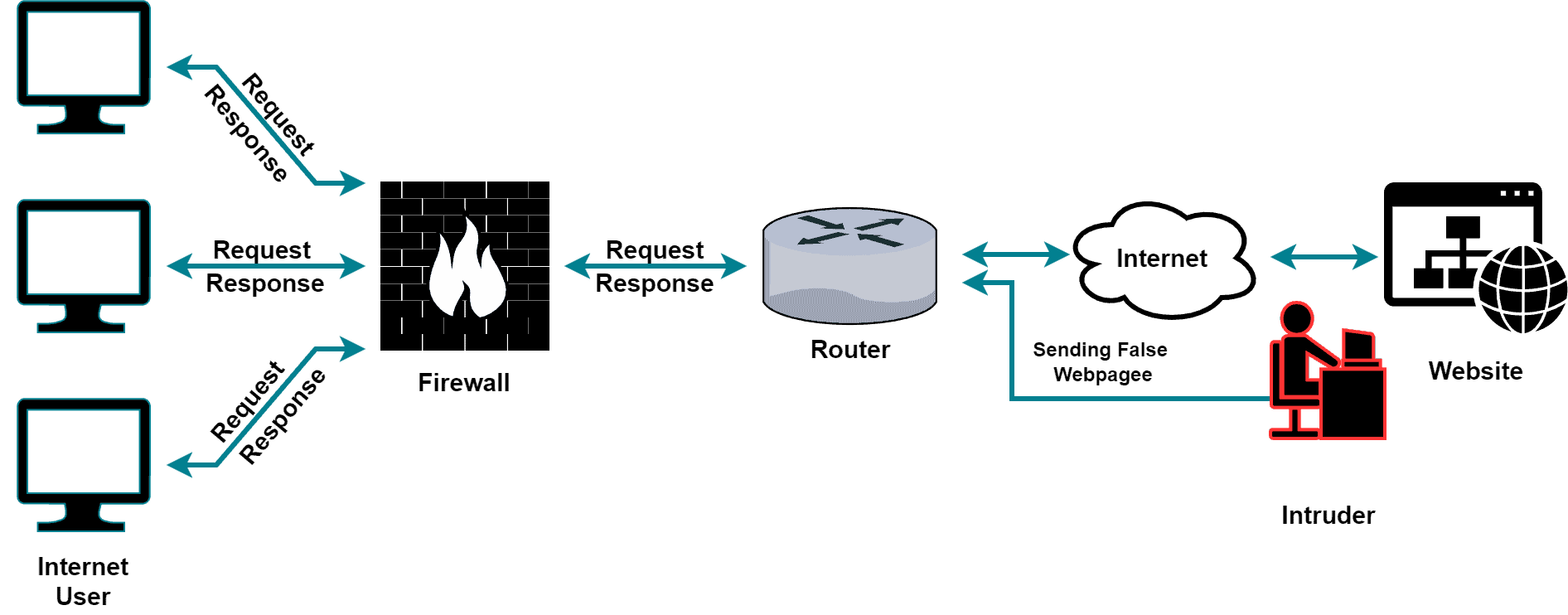
Hence, the main goal of network-level information security is to protect the network and its data from a wide range of security threats, including cyberattacks, viruses, and data breaches.
3.2. Techniques
Let’s discuss some techniques and tools we can use to enhance network-level security.
We can use firewalls to regulate network access by blocking or permitting traffic based on predefined rules. Additionally, a firewall can be hardware or software. Furthermore, we often install it at the network’s perimeter to manage incoming and outgoing traffic.
Another powerful technique is using intrusion detection and prevention systems (IDPS). To find and stop unwanted access to the network, we utilize IDPS. They can recognize suspicious behavior, such as efforts to scan the network for vulnerabilities and notify users. Additionally, they can also prevent or recover systems from such activities.
Furthermore, devices and the network can connect securely using virtual private networks (VPNs). They can be used to safely link various network components within an enterprise as well as to connect remote users to the network. Furthermore, network access control (NAC) is another security mechanism that manages network access by confirming the user’s identity and the device’s security status before granting access to the network.
Finally, we can use the segmentation technique. The technique of segmenting a more extensive network into smaller, easier-to-manage subnetworks is known as network segmentation. Additionally, it can aid in reducing the network’s vulnerability to malware and other security risks.
4. Application-level Information Security
4.1. Introduction
Application-level information security describes the procedures employed to safeguard the accuracy, privacy, and functioning of data. Additionally, it protects the applications utilized by a business. It involves guarding against unwanted access, misuse, disclosure, interruption, and alteration. Furthermore, it provides protection against the destruction of software, including web applications, mobile apps, and other applications.
The main goal of this security is to protect the data and functionality of the application from malicious actors. Additionally, it ensures that only authorized users can access and use the application.
Let’s look at a network architecture where we implemented application-level information security:

In this architecture, we ensure application-level information security by using several techniques like authentication and encryption.
4.2. Techniques
Let’s discuss techniques and tools we can use to protect application-level security. We’ll discuss four popular techniques: authentication and authorization, input validation, encryption, and security testing.
Authorization is the process of figuring out what activities a user is permitted to take within the program. On the other hand, authentication is the process of confirming a user’s identity. Additionally, only authorized users can access the program due to authentication and authorization constraints.
Another security technique, input validation, ensures that data submitted into an application is accurate and in the correct format. Hence, it can aid in preventing attacks like SQL injection, in which the attacker attempts to introduce harmful data into the application to take advantage of holes in the database.
We can transfer data into a code through the process of encryption to prevent unwanted access. Additionally, data saved on the program’s servers or devices can be secured via encryption.
Security testing is the process of evaluating the security of an application and an effective way to preserve application-level security. Specifically, it attempts to identify vulnerabilities and weaknesses in the application’s design, implementation, or deployment. Additionally, it can include techniques such as penetration testing and code reviewing.
5. Differences
Let’s take a look at the core differences between network-level and application-level security:
| Network-level Security | Application-level Security |
|---|---|
| Secures connections at the network level | Secures connections at the application level |
| Secures connections between any two devices, regardless of the type of connections being used | Secures connections between applications running on the same device |
| Protects all data, including sensitive data and data being sent across public networks | Protects data sent between two applications running on the same device |
| Can be applied on a variety of devices, such as networking devices, firewalls, and servers | Can only be implemented on devices that run applications, such as computers and databases |
| Requires minimal effort as it is implemented on devices that are already part of most computer networks | Requires significant effort as it requires building systems to secure connections between applications |
| Network admins are responsible for monitoring and maintaining network-level security | Programmers are responsible for monitoring and maintaining application-level security |
6. Conclusion
Information security is essential for protecting networks and computer systems. In this tutorial, we discussed two popular information security variants: network-level and application-level security. Furthermore, we explored the core differences between them.