Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll discuss ransomware in detail. First, we’ll present various types of ransomware.
We’ll describe the working procedure of a ransomware attack. Finally, we’ll explore some vital protection and prevention methods.
Ransomware is a virus that prevents victims from accessing their data until a user pays a ransom. Ransomware malware has a direct financial impact. It has generated a hacker ecosystem that uses it as a business model. Ransomware-as-a-service (RaaS) is a service model that makes it easy to obtain ransomware codes in return for money.
RaaS is a cybercrime economic model that allows malware developers to make money without distributing their threats. Non-technical hackers buy and disseminate viruses, with a portion of the earnings going to the producers. Because the developers take a little risk, their clients do most of the work. Subscriptions are used in certain ransomware-as-a-service scenarios, although registration is necessary for others.
The cost might be an outright purchase or a profit-sharing scheme. It depicts how crooks collaborate. One party is responsible for creating and distributing the ransomware code, while another controls the virus’s propagation or an attack campaign. Additionally, both parties get profit from a successful attack.
A successful ransomware attack has an immediate financial impact on a business or organization. The ramifications of a successful attack go far beyond the amount of the ransom. Companies may experience productivity loss, income loss, customer dissatisfaction, and possibly irreparable data loss. Therefore, it is highly recommended to safeguard systems with necessary ransomware prevention and detection methods.
There’re mainly four variants of ransomware: ransomware encryption, non-encrypting ransomware, leakware (doxware), and mobile ransomware.
Let’s talk about ransomware encryption first. When this type of malware enters a system, it secretly looks for files and encrypts valuable data. After encrypting files, a hacker demands the user to pay a ransom in return for the concealed data. The user receives specific instructions on how to process the payment.
After paying the ransom, the victim receives either a key or code for decrypting the files. In some cases, the user may receive an executable file tailored to decrypt the encrypted files on the victim’s workstation. In order to process payments, bitcoin is presently the most widely utilized form of payment. The average cost of each assault is between $ 300 and $ 400. Examples of crypto-ransomware include CryptoWall, CryptoLocker, WannaCry, and Locky.
Non-encrypting ransomware often prevents or restricts access to the target system before requesting a ransom. Additionally, it may require an action from a user that incurs a penalty to unlock files. Some malware demands the money upfront, while others rely on trickery to get victims to pay the ransom. Two examples of non-encrypting ransomware are Winlock and Reveton ransomware.
Locker ransomware is also a type of non-encrypting ransomware. This sort of ransomware prevents victims from using their operating systems. Locker ransomware restricts and disables access to a user’s computer resources. It prevents users from accessing their data and files on the PC.
Leakware varies from the others as it doesn’t limit access to the victim’s system or any data saved on it. However, it steals crucial information from the system and uses it to blackmail the victim. The hacker stores the obtained data on servers or other compromised PCs. The attacker threatens the victim with fabric disclosure if payment is not made.
Mobile ransomware assaults are focused on mobile devices. Because data is simple to replicate and restore, this virus acts as a blocker with no motivation to encrypt data. Once installed or launched on the victim’s PC, some malware part of mobile ransomware attempts to show a blocking warning on top of the UI, while others employ a variety of click high-jacking techniques to persuade the user to grant it additional privileges.
Let’s talk about the working procedure of ransomware. Like other forms of malware, ransomware has a lifespan and follows some standard steps when infecting a system:
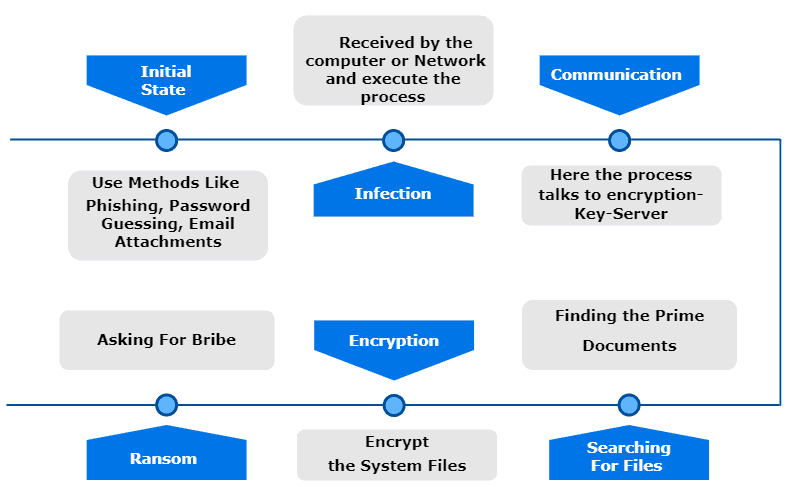
The hackers generally use phishing or attach malicious content to the victim’s email in order to get into the victim’s system. The virus enters the system when the victim clicks on a malicious link in an email attachment or makes an unintended drive-by download from a suspicious website.
Hackers generally use executable file format for the delivery of ransomware. The ransomware becomes active when a user clicks and runs the malicious executable file. After the activation, the ransomware attempts to establish a path for the hackers to access the victim’s system. The hacker then searches for the critical files on the system and encrypts them. After encryption, the hacker asks the victim to pay a ramson in return for the decryption key.
The most challenging part is to enter the victim’s system. There’re many innovative techniques used by hackers, which makes it difficult to predict in advance.
Given the potentially enormous cost of ransomware, a common concern is whether we can recognize or detect ransomware before infiltration. It’s possible to avoid ransomware if we’re able to foresee or detect it. We can avoid ransomware by following safe computing practices and installing the most recent protection software. Installing security software from trusted sources is highly recommended.
It’s important to protect the system with comprehensive security software. It’s absolutely necessary to ensure that all software is up to date. We must update the software on a frequent basis since remedies for flaws are often included in each update.
We need to be very careful when clicking a link. It’s highly recommended not to respond to suspicious emails or messages, and only download software from reputable sites. It’s an essential step because malware authors typically use social engineering to get users to install dangerous files.
Public Wi-Fi networks are unsafe, and hackers can sneak into the system connected to the wifi. On the other hand, installing a VPN can provide a secure internet connection.
Taking regular backup of important data is very important. We should keep a backup of vital files in the cloud and on an external hard drive, to avoid being locked out of them. It helps to safeguard data and prevents a user from paying a ransom.
In this tutorial, we discussed the definition and variants of ransomware. There’s no question that ransomware is a challenging and harmful program that may highly impact a user’s system.
We explained the working procedure of ransomware in order to understand ransomware attacks thoroughly. Finally, we listed some crucial protection and prevention methods to safeguard systems from ransomware attacks.