1. Overview
Authentication is required to verify the identity of a user or a system that wants to access a web app. Additionally, to create secure web apps, session security is crucial. Further, because of the incorrect implementation of authentication, attackers can exploit and acquire unauthorized access.
In this tutorial, we’ll discuss popular authentication methods for web apps and best practices.
2. What Are Different Ways to Authenticate Web Apps?
Authentication is necessary for a secured web application. Further, this is essential to give users superior experiences.
Let’s start by describing the numerous methods for achieving authentication:
- Cookies-Based Authentication
- Authentication Using Tokens
- Third-party access (OAuth, API token)
- OpenID
- SAML
Let’s now discuss which authentication method to Pick.
For SSO, OpenID has dominated the consumer sector. Furthermore, SAML is frequently the choice for many commercial applications.
Cookie- or token-based authentication is best for web-based applications. API-token authentication is better than cookie-based authentication to support both web and mobile.
In addition to the methods mentioned above, if necessary, we’ll use one-time passwords (OTP), multi-factor authentication (MFA), email verification, etc.
3. Cookies-Based Authentication
Let’s elaborate the steps for cookies based authentication as shown in below diagram:
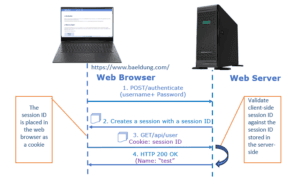
- Using their login information, the user tries to log in
- The server creates a session with a session ID after verifying the user using the supplied credentials
- The web browser (client) maintains the session ID as a cookie
- Upon subsequent requests, the session IDs on the client and server sides are compared, and if they are the same, the request is accepted
- Additionally, the session is ended on both the client and server sides if a user logs out of the application
3.1. Advantages and Disadvantages
Now, let’s discuss a few benefits and shortcomings of cookies-based authentication:
3.2. Best Practices
To avoid brute force assaults, the session ID should be long (128 bits) and generated randomly. The session ID should be free of any sensitive information pertaining to the user.
Further, the information should consist of a meaningless string of random characters. All session-based applications should use HTTPS communication.
The secure and HTTP-only properties are set when creating cookies. Keep sessions under control by deleting them when the browser is closed, a timeout occurs, the user logs out, or they log in from a different site.
4. Authentication Using Tokens
JSON Web Tokens (JWTs) are the most widely used web app authentication method. Further, they are standalone tokens having usernames, roles, rights, etc.
The server creates a JWT and sends it to the client with secret information. With each subsequent request, the client sends the JWT stored on the client.
The server would then check the JWT with each request made by the client before responding. Additionally, the secret key to digitally sign JWTs guarantees the integrity and authenticity of the web app.
4.1. Advantages and Disadvantages
Now, let’s discuss a few benefits and shortcomings of token-based authentication:
4.2. Best Practices
Let’s conclude by describing the best practices for achieving authentication using tokens:
- Let’s avoid including sensitive information in the payload
- Give tokens an expiration date
- Implement a proper and secure token management approach
- Avoid sending tokens through insecure connections when using HTTPS communication, if the requests get intercepted, they are vulnerable
- Avoid hardcoding tokens in online applications because this makes the web application more vulnerable to attack
5. Third-Party Access (OAuth, API-Token)
Open Authentication (OAuth) and API-token expose APIs to systems outside their own.
API-token functions similarly to a JWT token and is sent via an Authorization header and processed by an API gateway to verify the user’s identity. Additionally, there is the option of using OAuth 1.0a or OAuth 2.0, a protocol that enables applications to log in to servers as users.
Google, Facebook, Twitter, and other companies use OAuth 2.0, which offers secured delegate access to a resource based on the user and relies on HTTPS for security. With the user’s consent, OAuth 2 enables the identity provider (IDP) to issue a token to these third-party applications. To access the resource on behalf of that user, the client utilizes the token.
6. OpenID
To validate a user, OpenID, an HTTP-based protocol, utilizes an identity provider (IDP). IDP is responsible for protecting the user credentials.
Furthermore, IDP extends to other service providers a mechanism to implement Single Sign On (SSO) without the user’s input. Several websites that accept OpenID as an authentication method include Google, Facebook, WordPress, Yahoo, PayPal, and many more.
The most recent iteration of OpenID is called OpenID Connect, which adds OpenID (authentication) on top of OAuth 2.0 (authorization) for a security solution.
The below diagram shows a typical OpenID Connect process:
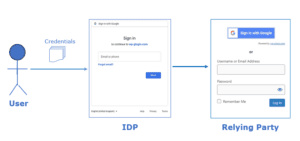
The relying party needs to be in direct touch with the IDP for a user to use the identity they shared with the third party. End-user authentication and providing end-user IDs to relying parties are the responsibilities of IDP.
7. SAML
While OpenID uses an IDP, SAML (Security assertion markup language) is XML-based and more versatile. SAML 2.0 is the latest version. Using the IDP URL, a user can log in to the system and have the system reroute them with XML data back to an application page. Furthermore, to obtain the user’s information, XML needs to be decoded.
SAML also offers a mechanism to implement SSO. Some SAML service providers are G Suite, Office 365, OneLogin, and Okta.
Let’s discuss the SAML process using the following diagram:
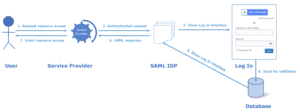
The identification service gives the service provider the user credential first. Next, each end user must log in using SSO just once for SAML parameters to be passed seamlessly to the service providers.
Furthermore, the service provider contacts IDPs to inquire about the authenticity of a request. The configuration of SAML SSO also requires permission during this process. This process guarantees the user authentication and authorization.
8. Pros and Cons of Different Methods for Authentication
Web app authentication involves several methods, including cookies, JWT, OAuth, API Token, SAML, and OpenID. Depending on the use case and the security requirements, they have various advantages and downsides.
Now, let’s discuss a few benefits and shortcomings of commonly used authentication methods:
9. Conclusion
In order to create secure web apps, session security is crucial. Without defense against external threats, a web application is not secure.
In this article, we’ll learn the crucial roles of methods in authentication for web applications and how to handle authentication on RESTful APIs.