Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
What Are Brute Force Attacks?
Last updated: March 18, 2024
1. Overview
In this tutorial, we’ll discuss brute-force attacks in detail. We’ll explore how a typical brute-force attack works, along with some examples.
Finally, we’ll highlight the major consequences and some mitigation techniques to prevent such attacks.
2. Introduction to Brute-Force Attacks
In order to crack a password or an encryption key, a hacker can use brute-force attacks. In a brute-force attack, the attacker tries every possible combination of characters until they successfully break the password or get access to certain systems. Automated programs, also known as bots, typically carry out brute-force attacks. Additionally, the attacker designs computer bots in such a way that they can try thousands or even millions of password combinations per second.
Generally, we can find the primary use of brute-force attacks in password cracking. The attackers attempt to gain unauthorized access to a system or account by guessing the password.
Furthermore, they can also be used to break encryption algorithms by guessing the encryption key. Brute-force attacks can be time-consuming and resource-intensive. However, if the password is weak or easy to guess, the probability of successful implementation of brute-force attacks is high. Although, encryption algorithms with long keys and complex key generation processes can make brute-force attacks impractical.
3. Working Procedure
Let’s discuss the typical steps an attacker follows to implement a brute-force attack:
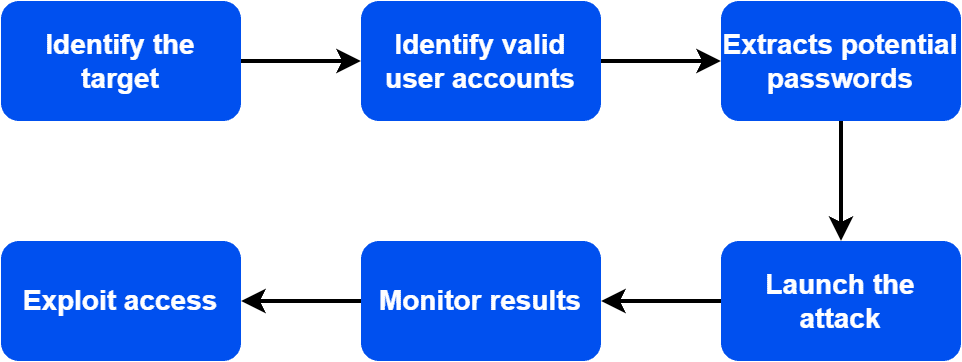
The first step of the attack is to identify the target system correctly. Therefore, the attacker chooses a system or application to which they wish to gain access illegally. The next crucial step is to pinpoint valid user accounts on the target system. The attackers can identify target user accounts by scanning for open ports, using social engineering techniques, or harvesting user credentials from other sources.
As soon as an attacker identifies the system and user accounts, he starts gathering a list of potential passwords. Additionally, the list of potential passwords includes common dictionary words, known passwords, and common password patterns. Initially, the attacker tries to break the password of targeted user accounts by using the potential password list. A brute-force attack is launched if the attacker can’t break the password using the list of potential passwords.
The attacker uses a brute-force attack tool or script to systematically try every possible combination of passwords for each user account. Furthermore, typically such attackers are launched from a single device. However, in order to increase the speed and efficiency of the attack, the attacker can launch such attacks from multiple devices simultaneously.
Moving forward, the attacker monitors the results of the attack to determine if any user accounts have been successfully compromised. Therefore, if the attack is successful, the attacker may use the compromised account to gain access to sensitive data or carry out further attacks.
4. Examples
There’re several kinds of brute-force attacks. Let’s explore some of the popular attacks used by attackers.
The most popular usage of a brute-force attack is to crack passwords. In order to crack a user’s password, an attacker repeatedly try different permutations of the password until they succeed. The attackers use automated tools to try stolen usernames and passwords on multiple websites in the hopes of gaining access to the targeted systems:
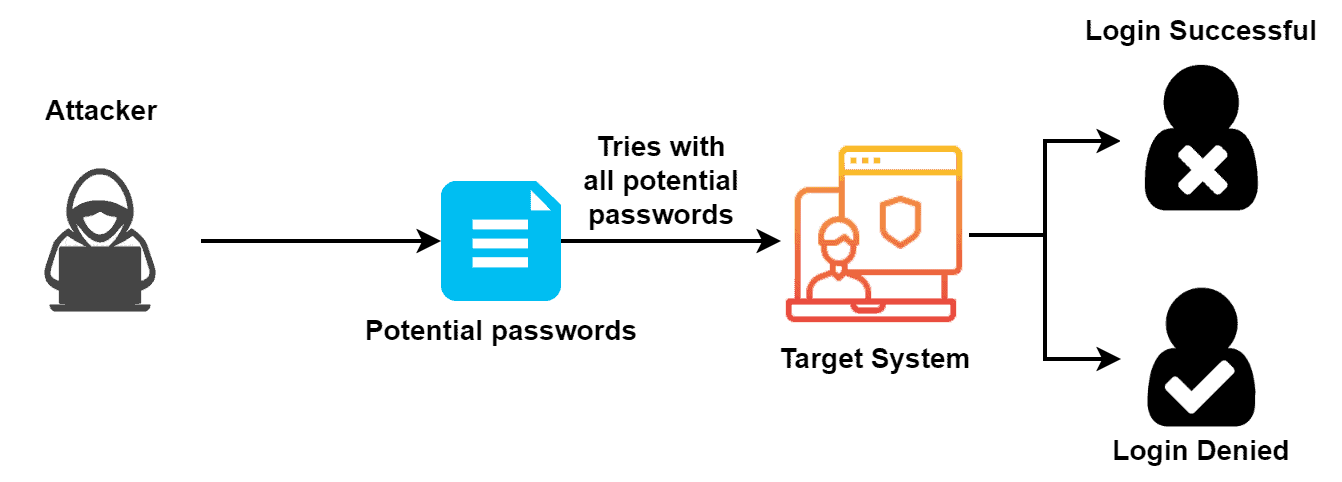
Additionally, an attacker can launch brute-force attacks using the remote desktop protocol (RDP). An attacker attempts to gain access to a remote system by guessing the username and password used to authenticate to the system. Furthermore, this technique is often used to gain access to servers or other critical systems accessible over the Internet.
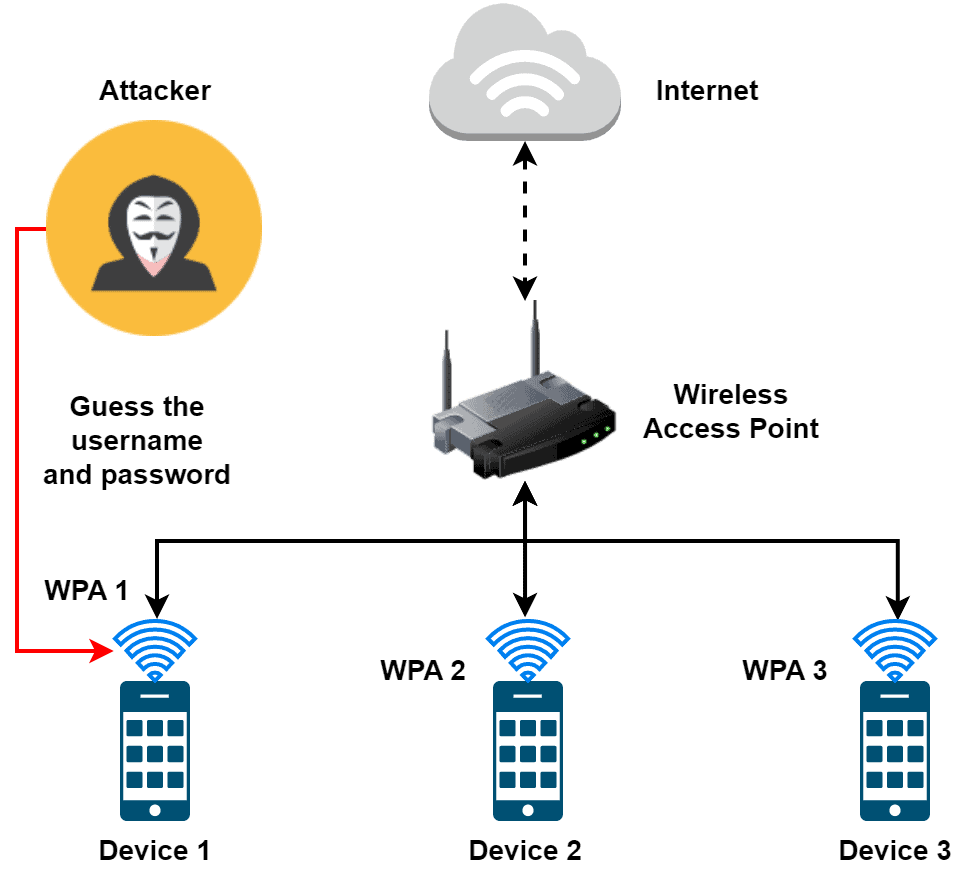
Let’s talk about brute-force attacks on wireless networks. An attacker attempts to gain access to a wireless network by guessing the network’s pre-shared key (PSK) or Wi-Fi Protected Access (WPA) passphrase. Furthermore, attacks use this technique to gain unauthorized access to business networks and devices:
Moving forward, attackers can launch brute-force attacks on a database. In such a case, an attacker attempts to gain access to a database by guessing the username and password used to authenticate to the database. Such an attack mainly aims to expose data such as user details, credit card information, secret credentials, and bank account numbers.
Finally, in order to break encryption algorithms, attackers can use brute-force attacks. Here, the main motive is to guess the encryption key or password used to encrypt the data. A successful attack can expose confidential information. Additionally, it can make ways to implement other types of attacks, such as man-in-the-middle attacks or data exfiltration.
5. Impact
Brute-force attacks can have significant impacts on both individuals and organizations. Let’s take a look at some of the major consequences.
A successful attack can provide access to sensitive data such as financial information, intellectual property, and personal data. Additionally, if an attacker gains unauthorized access to a system or network, they may be able to install malware or viruses. In this way, the attackers can set up the targeted system for future actions.
A typical consequence of a brute-force attack is the disruption of services and networks. It can cause service disruptions or downtime for the target systems or networks. Furthermore, if an organization’s systems are compromised due to a successful brute-force attack, it can damage its reputation. Additionally, it can result in financial losses due to theft of funds, loss of revenue, and the cost of recovery.
Finally, a brute-force attack can lead to legal consequences for organizations. If a company is found to be in violation of data protection rules, it might face fines, penalties, or even litigation.
6. Mitigation Techniques
Now let’s discuss some general practices and techniques to prevent brute-force attacks.
First of all, organizations should enforce the use of strong passwords. Organizations should implement strong password policies, such as requiring long, complex passwords with a mix of uppercase and lowercase letters, numbers, and special characters. It’s also important to change passwords regularly.
Furthermore, organizations can implement account lockout policies. After several unsuccessful login attempts, we can temporarily disable the user account. In this way, organizations can make it more difficult for attackers to implement brute-force attacks on their systems and network.
Additionally, organizations can implement rate limiting on login attempts. By limiting login attempts, they can slow down or block login attempts from IP addresses that are making an unusually high number of login attempts within a short period of time. Additionally, one of the efficient solutions is to use multi-factor authentication (MFA). By enforcing the usage of multiple factors of authentication during login, MFA increases the overall safety of the system.
Organizations can use network security devices like firewalls and intrusion detection systems to keep an eye out for possible malicious traffic. Such devices can block brute-force attacks before they reach the target system. Additionally, we can encrypt sensitive data to prevent it from being accessed in the event of a successful attack.
By implementing these techniques, individuals and organizations can significantly reduce the risk of brute-force attacks as well as improve the overall security of the systems.
7. Conclusion
In this tutorial, we discussed brute-force attacks in detail. We explored how a typical brute-force attack works, along with some examples. Finally, we highlighted the major consequences and some mitigation techniques to prevent such attacks.