Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll discuss a modern security mechanism used for authentication: one-time password (OTP). We’ll explore how to generate an OTP and what are the popular variants of it.
Finally, we’ll highlight the core advantages and disadvantages of OTPs, along with a few crucial applications.
A one-time password (OTP) is a security mechanism used to protect against unauthorized access to sensitive information or systems. We can generate this unique code for single use. Additionally, it comes with a limited lifespan, usually around 30-60 seconds. Furthermore, we commonly use OTPs for authentication in various online services and transactions to enhance security.
An OTP is a string of characters, usually numbers or letters, that verifies a user’s identity for a specific transaction. In order to generate an OTP, we utilize several techniques, such as hashing, encryption, and hash-based message authentication code (HMAC). Furthermore, based on our requirements, we can utilize several types of OTPs, including time-based, event-based, and message-based.
We commonly use OTPs in two-factor authentication (2FA). It’s a security process that requires two forms of identification in order to access a system or account. Typically, this involves a combination of a passcode the user knows and an OTP delivered to the mobile or email.
OTP is more secure than conventional passwords. It’s difficult to intercept and requires physical access to the user’s device to access the code. Additionally, since we can only use them once and comes with a limited lifespan, it significantly reduces the risk of unauthorized access.
The basic idea behind OTP is to generate a unique password each time a user needs to log in or access a system. Furthermore, this password is sent to the user via a separate communication channel, such as a mobile phone, email, or a dedicated OTP device. The user then enters this password along with their regular login credentials to gain access to the system.
Let’s take a look at the steps involved in generating an OTP:
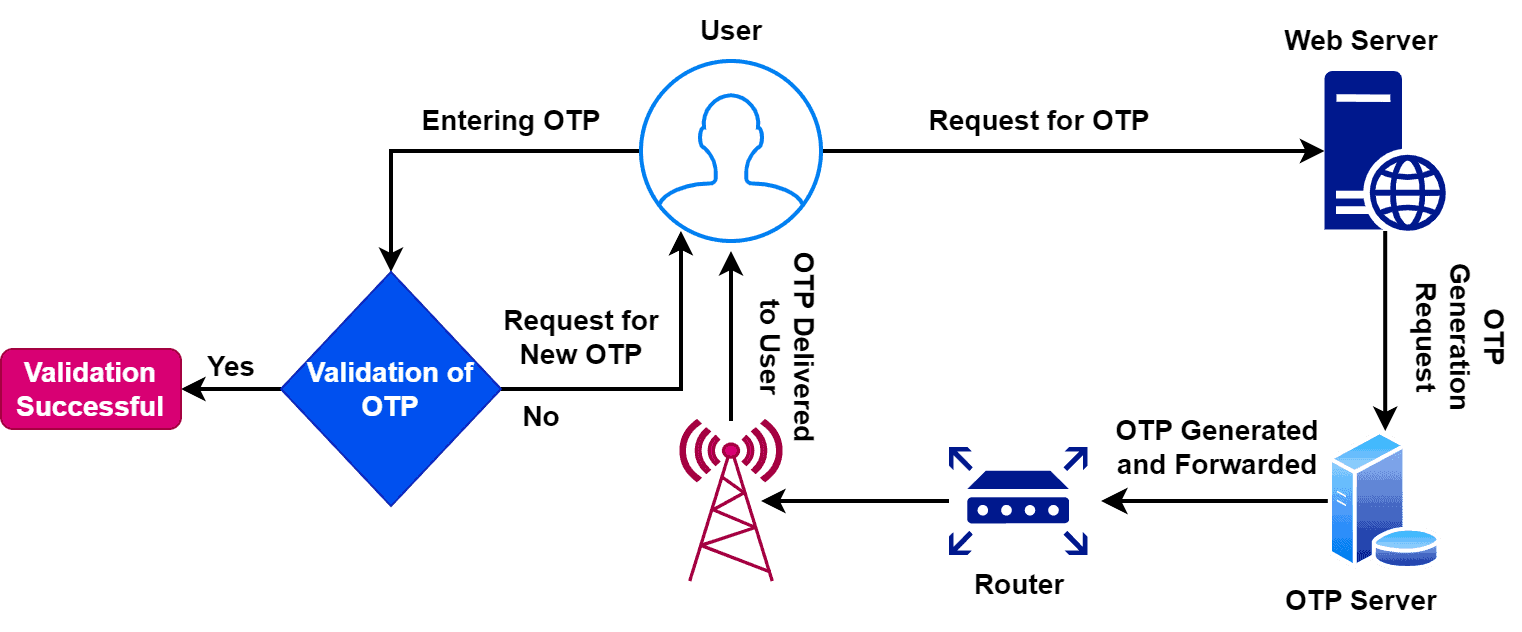
Initially, the user enters their username or email address to request an OTP for authentication. The web server receives the request and forwards it to the OTP server. Furthermore, the OTP server generates a unique OTP and sends it to the user’s registered mobile number or email address.
The user receives the OTP through the selected communication channel. The OTP is usually a random string of characters valid only for a limited time, usually around 30 to 60 seconds. Therefore, the user enters the OTP in the authentication field along with their regular login credentials.
As soon as the user enters OTP, the system verifies the OTP entered by the user with the one generated by the OTP server. If the OTP matches, the user is granted access to the system. If the time associated with an OTP is over, the user must request a new OTP.
OTP is a secure authentication method as the password is valid only for a single use and for a limited time. Even if the OTP is intercepted, it can’t be used again for unauthorized access. Additionally, OTP is also easy to use and convenient, as it eliminates the need for users to remember and manage multiple passwords.
There are several types of OTP we can generate based on the requirement. Let’s discuss some popular types of OTP.
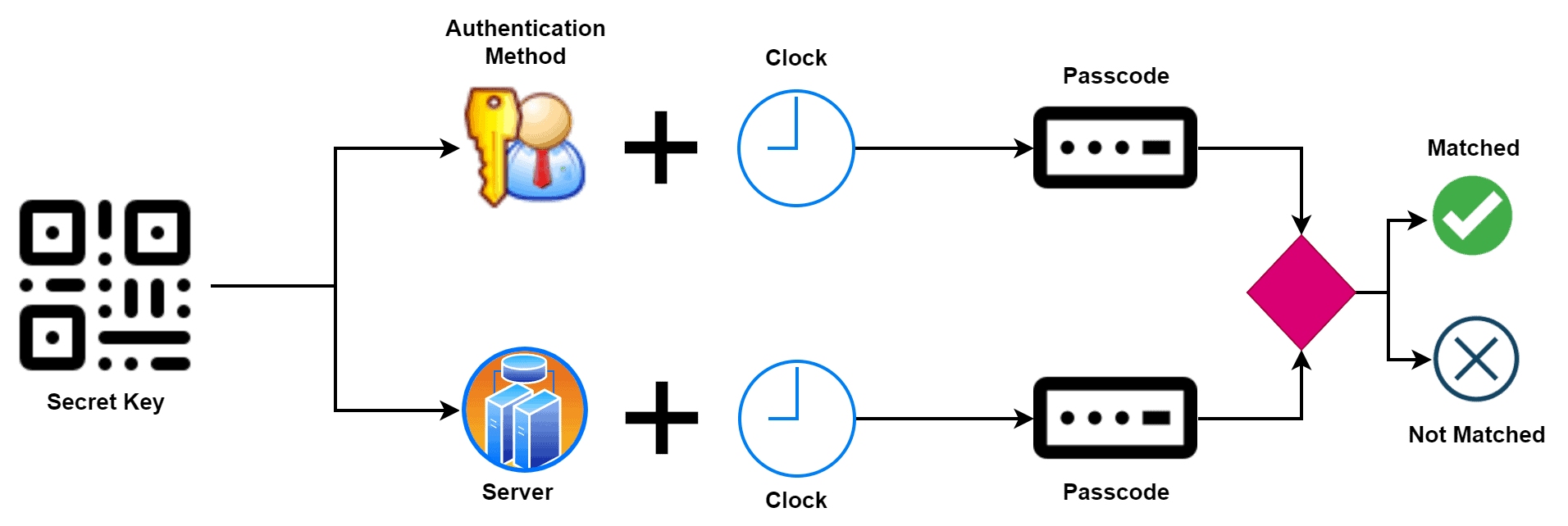
The most popular and widely used variant of OTP is the time-based one-time password (TOTP). TOTP uses a combination of a secret key and the current time to generate a unique password that we can only use once. First, we generate a secret key. The system generates a secret key, typically using a cryptographic algorithm such as HMAC. The secret key is unique to each user.
Furthermore, we must synchronize the user’s device and the system’s server clock to ensure they generate the same TOTP simultaneously. We can achieve this using a time synchronization protocol such as Network Time Protocol (NTP). Popular applications like Google Authenticator use TOTP. Additionally, the TOTP algorithm generates a new OTP every 30 seconds:
Another popular variant of OTP is event-based OTP. It uses a secret key and a counter in order to generate an OTP. We generally use the HMAC-based one-time password (HOTP) algorithm to implement event-based OTP. Furthermore, we can send OTPs via SMS to the user’s mobile phone. The service provider generates the OTP, which is usually valid for a limited time period. Such OTPs are known as SMS-based OTPs.
Similar to SMS-based OTPs, we can generate OTPs using email and mobile-based applications. When generating OTPs, it’s important to use a secure method and keep the secret key confidential.
Now let’s discuss the core advantages and disadvantages of OTP:
| Advantages | Disadvantages |
|---|---|
| Provides an additional layer of security beyond traditional passwords | Relies on the generation and delivery of a unique code, which can sometimes be affected by technical issues such as network outages or delivery delays |
| As OTPs are time-sensitive and only valid for one usage, it’s very difficult for hackers to get access to a user’s account | Users may endure frustration and even be locked out of their accounts if the network is overloaded |
| Typically, generated and delivered to the user’s device automatically, without the need for the user to remember the password | Due to the limited lifespan, users need to be vigilant about using the code within the specified time frame |
| Implementation cost is low and is compatible with most platforms and devices | Typically, generated and delivered via a user’s mobile device or email, which means that if the device is lost, stolen, or damaged, the user may be unable to access their OTPs |
| Can be generated and delivered via a variety of channels, including SMS, email, or mobile apps, making them a flexible authentication option | Some services use SMS as the primary method of delivering OTPs, which can be problematic in areas with poor network coverage |
One-time passwords (OTPs) have become an increasingly popular authentication method for online services due to their enhanced security features. Let’s discuss some of the most common applications of OTPs.
OTPs play a very crucial role in two-factor authentication (2FA). We can use OTPs as the second factor in 2FA. In this setup, the user needs to provide a static password as well as an OTP to gain access to the system. Thus it’s very challenging for attackers to launch attacks on a system with 2FA, as they need both the static password and the OTP.
Additionally, we can use OTPs in online banking. Many banks use OTPs as an additional layer of security when customers perform transactions online or via mobile banking. Generally, the banks send an OTP to the customer’s registered mobile number or email address when they try to access their bank account online. Hence, the customers need to enter the OTP along with the regular password to complete any transactions.
Online shopping websites often use OTPs to verify the identity of the user during checkout. This helps prevent fraudulent transactions and protects the user’s payment information. Furthermore, we can use OTPs for remote access to corporate networks or cloud-based services. The OTP serves as an additional layer of authentication beyond the standard username and password. Finally, several VPN services use OTPs to ensure only authorized users can connect to their network.
In this tutorial, we discussed a modern security mechanism used for authentication: one-time password (OTP). Then, we explored how to generate an OTP and what are the popular variants of it. Finally, we highlighted the core advantages and disadvantages of OTPs, along with a few crucial applications.