Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll learn about cryptojacking attacks. We’ll start by defining the basic concepts of cryptojacking and cryptomining. Then, we’ll explain how these attacks work and what are the potential methods used to execute them. Next, we’ll present common examples of cryptojacking scripts. Finally, we’ll go through ways to detect these attacks and prevent them on one’s device.
Cryptojacking is a type of cyber-attack where cybercriminals use people’s devices, such as computers, smartphones, and servers, without their permission to mine cryptocurrency. The main objective of this activity is to generate profit. It is particularly challenging because it can operate secretly and goes undetected.
Let’s define cryptocurrency in order to understand cryptojacking attacks.
Cryptocurrency is a digital or virtual currency that uses cryptographic algorithms to secure and verify transactions, such as Bitcoin, Ethereum, and Monero. Specifically, it uses a decentralized database to control and create units or blocks called a blockchain. This database is regularly updated with information about all transactions that have taken place since the last update.
Cryptocurrencies require individuals to provide computing power to solve complex mathematical equations and generate new blocks. In exchange, these individuals receive cryptocurrency as a reward. Generally, this is the process of trading computing resources for currency, called cryptomining. The involved individuals are known as miners.
The following figure explains the cryptomining process:
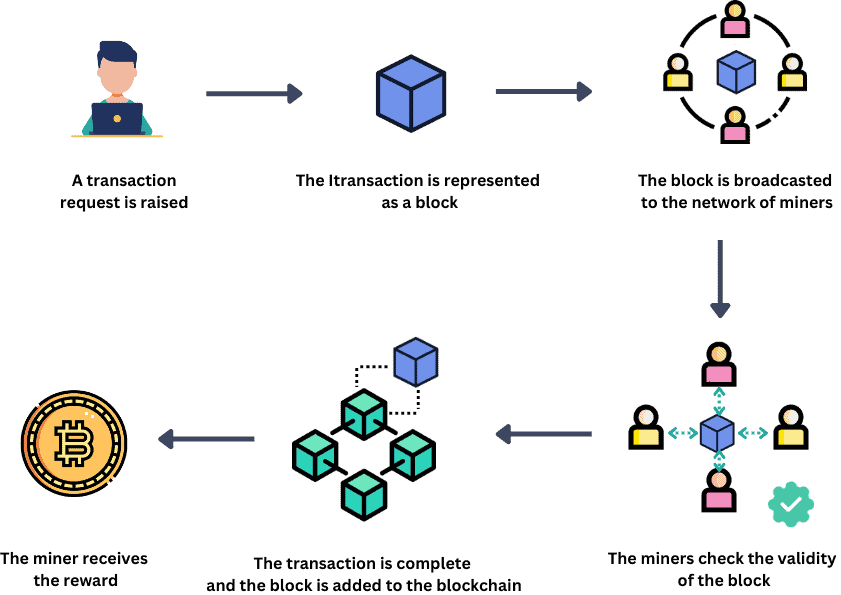
To resume, the hackers will execute the same process but illegally. They’ll use other people’s computers and exploit their energy to work for them and get the currency. This is called cryptojacking.
Let’s now explain how these attacks work.
Cryptojacking attacks typically involve two stages: infection and mining.
The first step of a cryptojacking attack is infecting the user’s computer or device with malware. This latter runs silently in the background without the user’s knowledge. There are common ways in which infection can operate:
The second step of a cryptojacking attack is mining. Once the malware infects the user’s computer or device, it begins to mine cryptocurrency without the owner’s consent. In fact, the malware uses the device’s processing power to solve complex mathematical problems required to validate transactions.
Each time the malware validates a transaction, it adds it to the blockchain network and receives a certain amount of cryptocurrency. The rewards in cryptocurrency are sent to the attacker’s digital wallet.
We can recognize three different types of cryptojacking attacks: browser-based, system-based, and cloud-based.
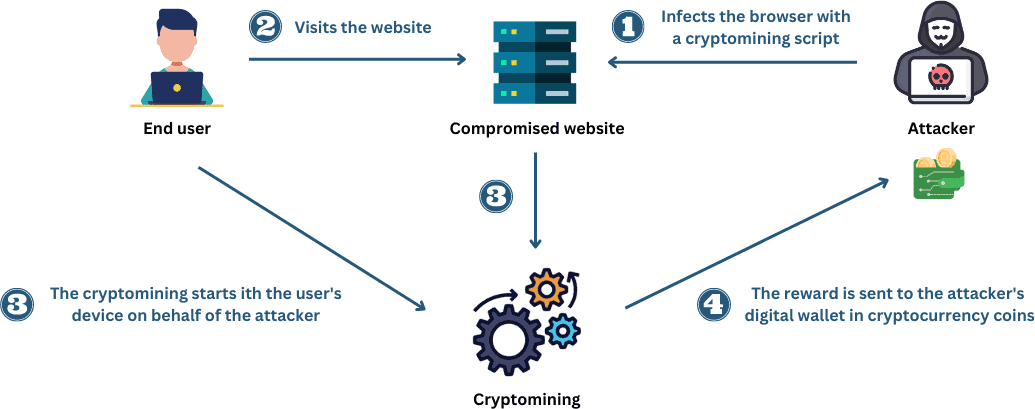
Browser-based cryptojacking involves running JavaScript code directly on the user’s web browser. Here, the attacker creates a cryptomining code and injects it into a website or advertisement. When the user visits the site or clicks on the advertisement, the JavaScript code runs automatically in the background and uses the user’s CPU resources to mine cryptocurrency.
This type of cryptojacking typically causes less damage compared to other methods because it only impacts the user’s web browser. Specifically, there’s no need to install any harmful software on their computer. However, this makes it more difficult to detect.
Let’s represent this with an explicative figure:
This type occurs when a user downloads and installs malware onto their computer that spreads cryptomining script into their system. One of the most common ways to deliver malware is through email impersonation. Here, the attacker sends an email that looks legitimate and tricks the receiver into clicking on a malicious link. The malware runs in the background and uses the user’s computer to mine cryptocurrency.
This type of cryptojacking is more harmful than browser-based cryptojacking. In fact, it allows the attacker to gain control over the user’s computer, steal sensitive information, and even cause damage to the whole system.
This type of cryptojacking attack involves compromising a cloud server or a container in a cloud environment to mine cryptocurrency. Attackers can use various techniques to gain access to cloud servers, such as exploiting vulnerabilities in software or using stolen credentials.
We should know that cloud-based cryptojacking attacks are becoming increasingly common since more organizations move their operations to the cloud. This results in significant costs for the organization and potential performance issues for the cloud infrastructure.
Let’s discover some well-known examples of cryptojacking attacks:
Coinhive was a cryptocurrency mining service that allowed website owners to monetize their websites by using their visitors’ CPU power to mine the Monero cryptocurrency. The service was launched in 2017 and gained popularity among website owners as an alternative to traditional advertising.
However, it also faced criticism for its potential to be used for malicious purposes, such as cryptojacking. In March 2019, Coinhive announced it would be shutting down its operations due to the declining value of Monero and the negative reputation it had acquired.
WannaMine v4.0 is a type of malware that was discovered in 2018 and is a variant of the WannaMine malware family. This malware is particularly dangerous because it can mine cryptocurrency on infected computers and propagates to other machines on the same network.
WannaMine v4.0 is usually spread through phishing emails. Once installed, it can cause the computer to slow down and become less responsive by using its processing power to mine cryptocurrency. It can also cause damage to the computer’s hardware by overworking the CPU and GPU.
FaceXWorm is a type of malware that targets Facebook Messenger users, discovered first in 2018. It’s popular for its ability to spread quickly through social engineering tactics. Simply put, it tricks users into clicking on fake YouTube links, taking them to a fake site that requires downloading a Chrome extension.
Unfortunately, this extension hijacks the user’s Facebook account and propagates itself by sending links to the user’s Facebook contacts. It’s, thus, a rapidly spread malware that can steal login credentials, install cryptocurrency mining software, and display malicious ads.
Cryptojacking can be challenging to detect since the malicious code is designed to operate silently in the background. However, there are some signs that may indicate cryptojacking is occurring in our system:
We can use several means to protect ourselves from cryptojacking attacks and reduce the risk of infection. Here are some common precautions we can take, depending on the method of infection:
| Infection methods | Prevention tools | Definition |
|---|---|---|
| Phishing email | Raise security awareness | Improving our familiarity with social engineering techniques, such as email phishing, can assist us in avoiding falling prey to such schemes. Additionally, if we’re responsible for an organization, it’s crucial to educate our employees on current security trends. |
| Software vulnerabilities | Update our environment | Ensuring that our environment remains up-to-date by regularly upgrading drivers, software, and operating systems is essential to minimize the risk of exploiting vulnerabilities. |
| Malicious websites | Use Ad-blockers, install specific browser extensions and disable JavaScript | Malicious ads on websites are a way to deliver cryptojacking malware. That’s why, using ad blockers prevents these ads from loading on our browser. However, it’s not always a perfect solution since it may impact the website’s proper functioning. |
| Public Wi-Fi networks | Install anti-malware | Anti-malware programs scan files and programs for known malicious code, and block any threats found. Some popular examples of anti-malware software include Malwarebytes, Norton Antivirus, and Windows Defender. |
In this article, we talked about cryptojacking attacks and their potential dangers.
Cryptojacking attacks are a growing threat to computer users, allowing attackers to mine cryptocurrency using their processing power illicitly and secretly. That’s why it’s important to remain cautious and keep ourselves up to date regarding the attack and the potential protection tools.