1. Introduction
A virtual private network (VPN) is an overlay network. It is a logical network established on top of a physical, usually public, network and may span several geographical regions. That’s why it is called virtual. If a device is connected to a VPN, it gives the users an illusion of being directly connected to their organization’s private network. Of course, a VPN’s traffic traveling across public networks is encrypted giving the users security and privacy when working remotely. Remote access, security, and privacy are the main reasons for using VPNs.
2. Types of VPNs and the Concept of a Tunnel
VPNs differ in their architecture and transport protocols used to establish the overlay network. The VPN architecture may be either point-to-point or site-to-site. A point-to-point VPN is used to provide a device with remote access to a private network. In contrast, a site-to-site VPN is used to establish an imaginary bridge between two private networks as if they were connected directly:
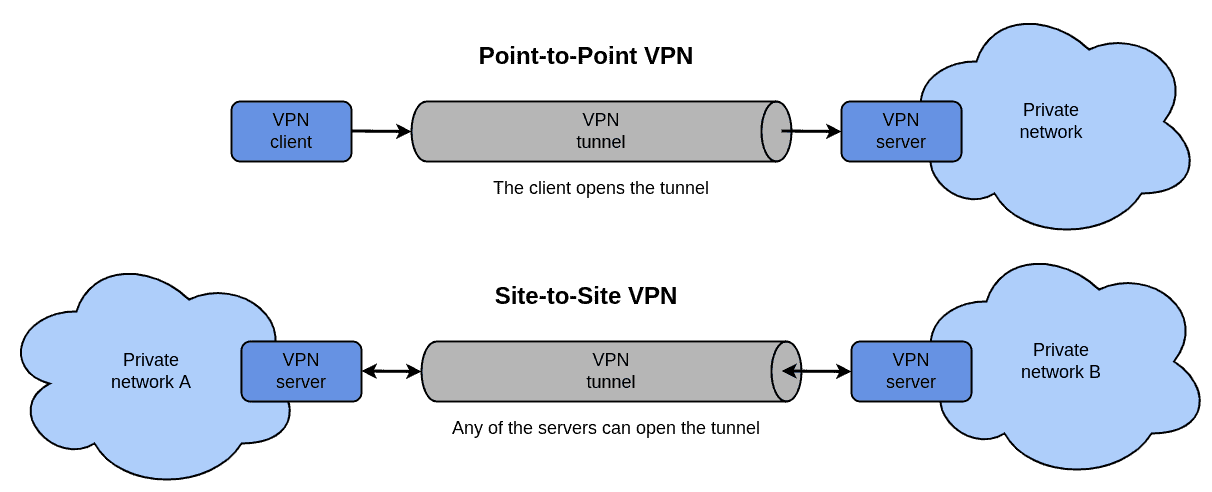
The transport connection established between two VPN entities is usually called a tunnel and the process of routing traffic through that tunnel is called tunneling. This happens only by using software without requiring any additional hardware. Of course, there exist also hardware VPN boxes, but they are usually used for purposes requiring very strong security measures.
According to the ISO/OSI layered model, the tunnel can be theoretically established above any level starting from the Data link layer (L2) and going over the Network Layer (L3) to higher layers. Moreover, the overlay network can be either an L2 or L3 network. In the case of L2, we’re talking about bridging (or switching), whereas in the case of L3 about routing. To give an example, a VPN may provide an L2 service over the TCP transport layer.
3. VPN Protocols
VPN protocols are usually designed for a particular combination of the overlay network layer and the transport layer. The most common VPN protocols are:
- PPTP (Point-to-Point Tunneling Protocol) provides a point-to-point L2 service (PPP) over TCP (Transport layer). This protocol was once very popular but is now obsolete.
- PPPoE (Point-to-Point over Ethernet) provides a point-to-point L2 service (PPP) over Ethernet (L2).
- L2TP (Layer 2 Tunneling Protocol) provides a point-to-point L2 service (PPP) over UDP (Transport layer).
- IPsec (Internet Protocol Security) provides both point-to-point and site-to-site L3 service over IPv4 and v6 (L3) depending on the operation mode.
- SSL and TLS both provide a point-to-point L3 service over a secure transport connection established by using either the SSL or TLS protocol.
- SSTP (Secure Socket Tunneling Protocol) provides a point-to-point L2 service (PPP) over SSL or TLS secure connection. It was designed to replace less secure PPTP and L2TP.
- DTLS (Datagram Transport Layer Security) provides a point-to-point L3 service over UDP (Transport layer).
- OpenVPN is an open-source VPN that can provide both a point-to-point and site-to-site L3 service over a secure transport connection (L4) established by using either the SSL or TLS protocol.
- SSH Tunnels are used for tunneling connections using SSH. They are also a kind of VPN, but provide an L4 service, so it’s rather called port forwarding. We mention SSH tunnels because they provide a transport service over an SSH connection and don’t need any special software (VPN server or client) to be installed on both sides of the tunnel. For more information and usage examples see the article on SSH tunneling and proxying.
4. Increasing Privacy
Although a VPN provides security by encrypting the transmitted data, it doesn’t ensure privacy. The remote VPN server may be logging usernames, IP addresses, and user activities. Moreover, some services may use IP address-based geolocation or a Wi-Fi positioning system to reveal the user’s location, sometimes with surprising precision. When using a VPN server, the location service reveals only the location of the VPN server, but not the location of the client. So what can we do if we don’t want to reveal our identity or location to a VPN server or a remote service? We can establish a VPN tunnel to another VPN server (hop) inside a VPN tunnel. We can even repeat it several times by nesting VPN tunnels. This nesting method is called multi-hop VPN or onion routing. At each subsequent hop, a nested VPN layer is dropped, much like peeling away layers of an onion:
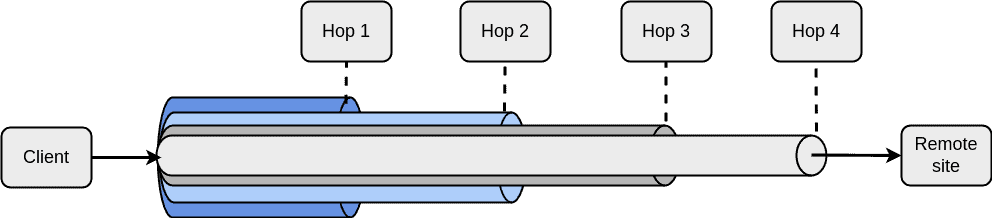
This approach is used by the well-known Tor relay network. Because the VPN client reaches the target (the innermost tunnel endpoint) indirectly over multiple hops, it is very hard to reveal the client’s real IP address and identity. Of course, this is all achieved at the burden of higher overhead and slower virtual connection speed.
5. Things to Consider When Using a VPN
There are two important facts we must consider when using a VPN:
- A VPN connection creates additional traffic overhead and consumes additional CPU power for data encryption.
- Using a VPN may result in suboptimal or unwanted traffic routing.
While the first one is obvious, let’s explain the second one. Suboptimal routing is simply the nature of overlay networks. Let’s consider, for instance, a user remotely working from London (UK) who is connected over a VPN to a headquarters network in Bombay (India). If the user logs onto a virtual host located in a data center in Frankfurt (Germany), then the traffic travels all over the world back and forth. This happens when the VPN client routes all traffic through the tunnel (routing mode) or in the case of L2 bridging when even broadcasts travel through the tunnel.
Suboptimal routing in VPNs can be mitigated by using selective routing. This means that only traffic for target hosts inside the private network is routed through the tunnel and the rest is sent to a local gateway as usual. But most organizations have policies that require all traffic to be routed through their firewall for security reasons.
A firewall or a NAT gateway may pose a problem for some VPN protocols. Firewalls usually allow only some protocols (like SSH, HTTP, HTTPS) to pass and other protocols are blocked. Also, devices behind a NAT gateway are not directly accessible from outside networks. In summary, SSL and TLS-based VPN protocols can bypass firewalls and NAT gateways. Other protocols may require a special router configuration (port forwarding) or less strict firewall rules.
6. Conclusion
In this article, we explained what a VPN is and its basic principles. We use a VPN if we want to get remote access to the internal network of our organization or if we want security and privacy while being connected to a public WiFi hotspot. A VPN may also connect geographically separated networks as if they were connected directly. Finally, let’s review the pros and cons of using a VPN: