1. Introduction
In this tutorial, we’ll see how to check and modify the queried DNS servers when using a VPN.
2. Definitions
Domain Name System (DNS) is the system to translate human-memorable domain names into the corresponding numeric Internet Protocol (IP) addresses. A DNS server contains a database of public IP addresses and their associated hostnames. A DNS name server is “authoritative” if it holds the records for the queried domain; otherwise, “non-authoritative” if it uses a temporary cache without owning the records.
nslookup is a command-line utility for Windows, macOS, and Linux to query Internet domain name servers. dig is another command-line tool for macOS and Linux that offers more info than nslookup, showing the answers of the queried name servers. Android and iPhone have equivalent utilities in the stores. In any case, we can use online tools such as nslookup.io.
VPN stands for “Virtual Private Network,” a protected network connection when using public networks. VPN services hide our actual IP addresses by tunneling our Internet traffic to a remote server. It’s helpful for safe browsing within public WLANs, bypassing the controls and restrictions of the Internet provider and the government, or the regional banning of video streaming or social networking. However, using a VPN does not mean that DNS traffic always bypasses unwanted checks.
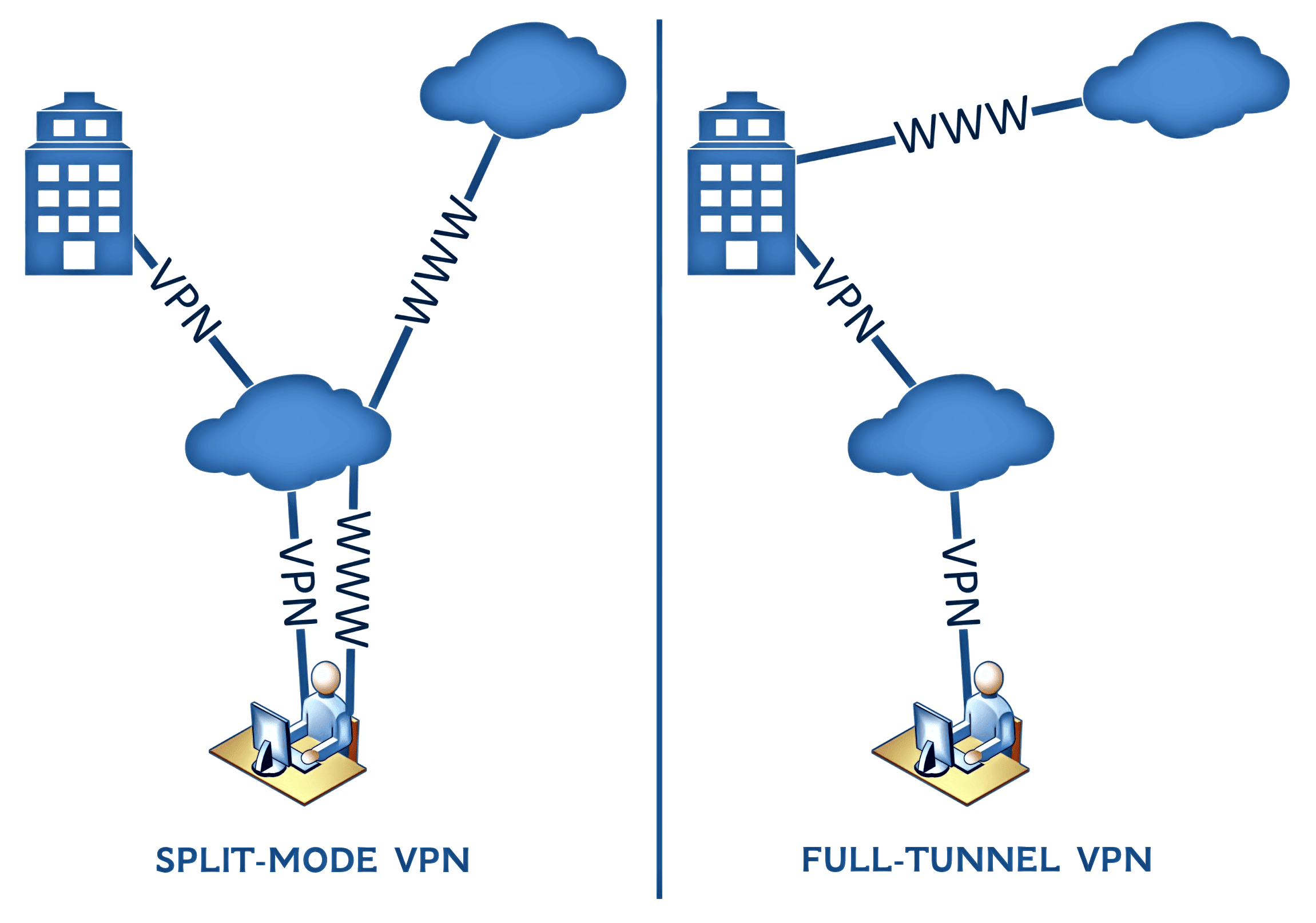
3. Split-Mode or Full-Tunnel VPN
In a nutshell, we can divide VPN services into two categories.
A “Full-Tunnel” VPN routes and encrypts all the Internet traffic through the VPN. Consequently, DNS requests are also encrypted and out of the control of the Internet provider. On the other hand, local network resources are not accessible.
A “Split-Mode” VPN is necessary to access at the same time both local resources and remote resources available by the VPN. It’s used, for instance, in working environments to divide up the enterprise’s VPN traffic and the other personal non-VPN traffic. It could not be clear how DNS requests are addressed in this case.
That’s why we need tools to investigate every possible scenario. In the following examples, we assume that we are using recent versions of the operating systems.
4. Command-Line Tools to Get the DNS Client Configuration
Let’s proceed to check which DNS servers our machines are using. As explained later, let’s keep in mind that this might not correspond to reality or might mislead us if there is a transparent DNS proxy.
Sometimes we might have insufficient information, e.g., the DNS server could be our router, and the actual DNS used will depend on the router configuration. In the case of virtual machines, the design of the virtual network adapter and virtual LAN can hide the address of the actual DNS server.
On macOS and Linux, /etc/resolv.conf lists the name servers used to lookup DNS names. However, the Linux Network Manager doesn’t update resolv.conf, and most macOS processes, including web browsers, don’t use it. In practice, we’re better off ignoring this file.
4.1. Windows
ipconfig /all displays all current TCP/IP network configuration. The output is a list of parameters, and we are interested in the line that starts with “DNS Servers.”
4.2. macOS
scutil –dns reports the current DNS configuration, but the output is quite verbose. We can filter it and immediately have the information we are interested in: scutil –dns | grep ‘nameserver\[[0-9]*\]’.
4.3. Linux
nmcli is a command-line tool for controlling NetworkManager and getting its status. Its output contains various sections, including “DNS configuration.”
5. DNS Leaks and Transparent DNS Proxies
DNS hijacking (also named DNS poisoning or DNS redirection) and DNS spoofing are practices to subvert the resolution of DNS queries. In addition to these problems that are difficult for the end-user to remedy, there are DNS leaks.
When using a VPN, a DNS leak occurs if a DNS request reaches a DNS server unprotected, often the DNS server of the Internet service provider (ISP). The personally identifiable DNS packets resulting from a DNS leak pose a severe threat to security and privacy, especially in countries with strict censorship and possible personal repercussions.
Moreover, some ISPs use “transparent DNS proxies” to intercept all DNS lookup requests and proxy the results. In other words, they force us to use their DNS service without us knowing it.
That’s why we need a reliable way to test which DNS servers we are actually using.
5.1. How a DNS Leak Tester Works
A DNS leak tester is usually a website or a command-line script. Both of them contact a server that uses its domain’s authoritative DNS server and an internal database to discover the DNS servers used by its visitors.
In more detail, the tester generates queries to pretend resources under a randomly generated, unique subdomain. That subdomain could be an UUID (universally unique identifier), such as 779298b9-57ac-40a3-9359-a482b113203a. Any computer can generate a UUID with near certainty that the identifier does not duplicate one that has already been, or will be, created.
To retrieve the resources from this unique subdomain, the browser or the script needs the IP address of the subdomain. Since the tester has never used that subdomain’s name before, no DNS server except the authoritative one can know the IP address. Therefore, the non-authoritative DNS server used by the user asks the tester’s authoritative DNS server for the IP.
The authoritative DNS server matches the randomly generated unique part of the domain name (the UUID) with the querying non-authoritative DNS server’s IP in an internal database. In addition, the tester paired the user’s public IP with the queried UUID. By joining these two database tables that share the same UUID, the tester obtains the non-authoritative DNS server used by the user. If it is an unwanted DNS server (like the one of the ISP), there is a DNS leak.
As a side note, it is evident that any website could detect the DNS we are using if the site owner has control of the authoritative DNS server. An “inquisitive” website can use a DNS leak to identify our actual ISP despite our VPN and, consequently, to see our approximate geographic location. It’s an issue in the case of geographically blocked content and, in the worst-case scenario, could thwart the hiding of our identity.
5.2. Open Source Scripts to Test for DNS Leak
The Github macvk/dnsleaktest repository offers a script to test for DNS leaks. It is available in Bash and Python for Linux and macOS and Powershell for Windows. For all three operating systems, there are also prebuilt executable binaries. Under the hood, this script connects to bash.ws/dnsleak.
D7EAD/Faucet is another similar GitHub repository, with source code in C++ and a precompiled executable for Windows. Behind the scenes, it also connects to bash.ws.
5.3. Third-Party Services to Test for DNS Leak
In alphabetical order, some online tools are bash.ws, browserleaks.com, dnscheck.tools, dnsleak.com, dnsleaktest.com, ipleak.net, perfect-privacy.com, and many more. This list is by no means exhaustive, as we can find a wide range of similar services with any search engine: all of them are websites offering a one-click test.
Another option is the DNS leak test app for Android. We can also integrate a DNS leak tester in WordPress, thanks to macvk/vpn-leaks-test, or in Kodi, thanks to Space2Walker/plugin.program.dnsleaktest.
5.4. How to Implement a Server for DNS Leak Test
If we don’t want to be bound to use a third-party service, we have to create our own server. The nhdms/dns-leak-server repository contains instructions to set up a Linux server and its DNS management to check for DNS leaks.
6. Modify the DNS When Using VPN
Due to the large variety of VPN clients, we need to narrow down the potential clients’ configurations in this discussion. Therefore we assume to use a default installation of the official OpenVPN client, which supports any OpenVPN protocol-compatible service. It’s available for Windows, macOS, Linux, Android, and iOS.
In practical terms, this client is suitable for any VPN service that provides a file with the .ovpn extension. Many commercial VPN services offer a set of .ovpn files as an alternative for their proprietary client.
Let’s suppose we want to use the Cisco OpenDNS primary server 208.67.222.222. By default, in the advanced settings, the OpenVPN client uses Google DNS servers as a fallback if the VPN tunnel doesn’t define any VPN DNS servers. But it doesn’t offer an option to force the use of a custom DNS.
To modify the DNS, we have to just edit the .ovpn file manually with a text-only editor, such as Notepad on Windows, Aquamacs on macOS, Gedit, or Xed on Linux. Before the <ca> tag, let’s add the options register-dns and block-outside-dns if absent. The first forces the client to prefer the configured DNS server over any other it may have received from DHCP. The second prevents DNS leakage to any server other than the configured one. Then let’s add the option dhcp-option DNS 208.67.222.222.
Let’s see an example (instead of x.x.x.x, there is the IP address of the VPN server, followed by the port number). In this case, protocol TCP and port 443 are used to fool a firewall, pretending that VPN traffic is HTTPS traffic:
client
dev tun
proto tcp
remote x.x.x.x 443
resolv-retry infinite
nobind
persist-key
persist-tun
remote-cert-tls server
auth SHA512
cipher AES-256-CBC
ignore-unknown-option block-outside-dns
block-outside-dns
verb 0
log /dev/null
status /dev/null
register-dns
dhcp-option DNS 208.67.222.222
<ca>We can now disconnect the VPN and import the new .ovpn file into the client (and delete the current VPN profile if we wish). After connecting to the new profile, we can quickly check the used DNS servers with dnsleaktest.com. They should be Cisco OpenDNS servers; their IPs may vary because the DNS queries are distributed between global data centers.
Additionally, popular and recent Linux distributions do not need the OpenVPN client. Support for OpenVPN connections via .ovpn files is already integrated out-of-the-box in the Network Manager applet, with the ability to change the DNS.
7. Conclusion
In this tutorial, we looked at how the DNS is actually used during a VPN connection which can be different than expected. We saw how to detect them and change them.
This in-depth exploration has helped us understand why our privacy quickly gets out of control. However, DNS servers are just one of the many aspects to keep in mind since anonymous browsing in critical surveillance contexts involves not only technical aspects but also behavioral ones.