Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 11, 2023
People worldwide use VPN services to break down the barriers of Internet censorship. Theoretically, a VPN hosted in a country with permissive laws allows us to access any website and app. Many VPN providers imply that we can safely use their VPN for illegal online activities. They also claim that they do not log us or share data with third parties. No end-user can verify these statements, which may fuel a false sense of security.
In this tutorial, we’ll analyze whether using a VPN makes us anonymous and untraceable.
Every day most of us pour private, confidential, and sensitive information on the Net, heedless of the long-term consequences. Distance education, remote work, and social life often force us to use zero-privacy online services that collect our private data. But our control over proprietary software and hardware is minimal or non-existent. In addition, smartphone localization is always possible, with or without our permission.
We can neither address nor mitigate the problem solely on a technical level, for instance, learning how to use privacy settings. While technical expertise is desirable, it is entirely irrelevant when we accept Big Tech’s contracts, such as those shown when we first use Facebook or Whatsup. We permanently authorize big companies to do what they want with all of our private information and with the content we post.
Moreover, a VPN can’t help us avoid data breaches on online services. It doesn’t defend against cyber threats and identity theft, neither it prevents our medical information or personal or family photos from getting into the wrong hands. It cannot force us to be wise in choosing passwords and use two-factor authentication.
Another issue is that parents, employers, partners, and acquaintances can easily spy on our smartphones. Many articles give precise instructions for spying on Whatsup or, more generally, our activities with the smartphone. This spying is easier if the smartphone is corporate or taken over by people other than the owner. There is a lot of free and paid software to carry out this spying.
In addition, a growing number of smartphones, desktops, and laptops are pre-infected before purchase by altering a popular legitimate app, such as Facebook. This alteration allows those who control the infected app to read and send messages, install apps, see and modify data on the phone, read the contact list, monitor the user’s location, record phone calls, make fraudulent purchases or bank transactions, and so on.
Sometimes, snoopers don’t need to physically access the spied smartphones even once, as in the case of NSO’s Pegasus spyware, one of the world’s most sophisticated hacking tools, repeatedly in the news. Moreover, many governments force citizens to use apps to track their movements and expenses. No VPN can remedy these aggressive forms of tracking. In short words, anonymity and privacy with a smartphone are virtually impossible.
Global surveillance disclosures demonstrate the conservation of all the information collected on people to profile them precisely. This mass filing is not an exclusive problem of social networks. In fact, it concerns all the mediated communication, including phone calls, messages, and emails.
To face the problem of privacy protection on the Net, we must clarify some basic concepts:
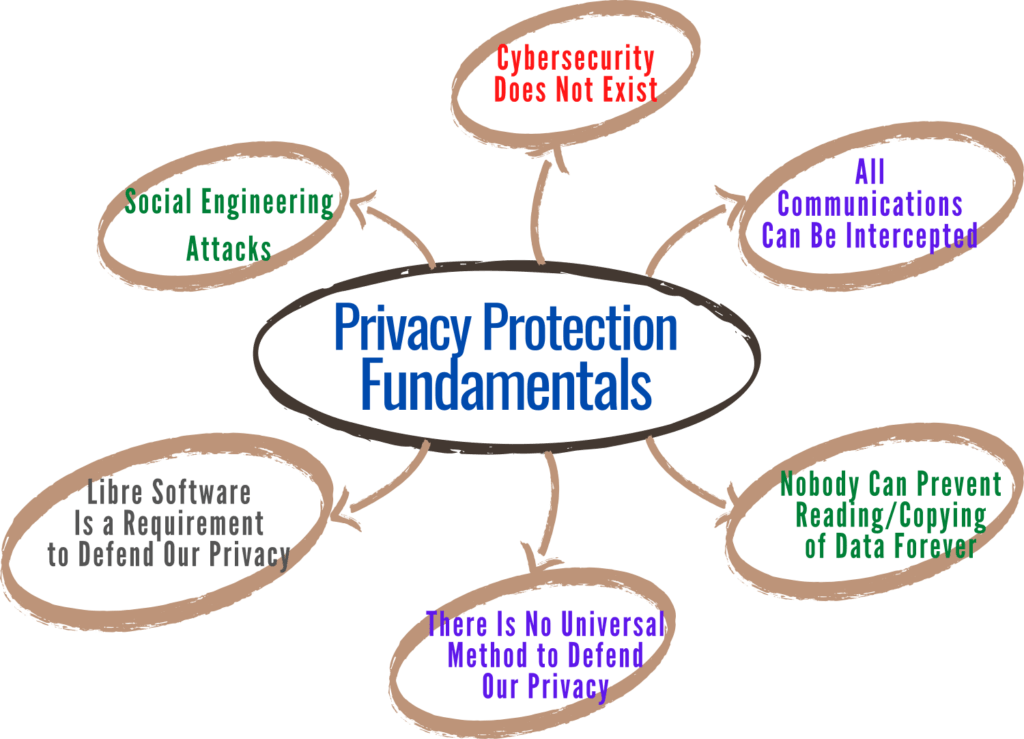
Errors are an unavoidable part of any computer system. Many commonly used devices are terribly complex, from smartphones to the latest car models, from personal computers to the newest television models. The more complex a system made up of hardware and software is, the greater the likelihood that something will get out of the control of both designers and users.
This lack of control can be due to coding or design errors, unintended or unforeseen circumstances in which such devices operate, or unknown reasons. Therefore, in an absolute sense, there is no security.
A hidden camera, spy software, or a physically close person can discover our activities and passwords. We can also show them because of a trivial distraction or because we are social engineering targets. Our devices can be stolen, hacked, and spied on as well.
Sometimes passwords are useless since expert people can access confidential data on our devices, bypassing any password, as many tutorials demonstrate. But even if our smartphones or computers were safe, our chats and passwords can pass through or be stored on compromised servers. So, in short words, any information is potentially accessible to unauthorized parties.
Any technique adopted to prevent copying digital data will sooner or later prove ineffective: it is only a matter of time. Security by obscurity isn’t safe, as secret algorithms could be discovered or reverse-engineered. Conversely, open security is temporary anyway, since public algorithms that the current computers cannot break, could be broken in the future by supercomputers or new techniques.
Those who offer quick guarantees and security may attract us, perhaps with a one-step solution. The promise of a single service (like a VPN) to solve all information security and privacy issues sounds comforting, but it doesn’t exist. Besides, our Internet traffic goes through the VPN provider’s network if we use a commercial VPN. Whoever has control of the servers can see and record everything we do online.
More and more data about each of us is being generated faster and faster by more and more devices. Protecting our privacy is usually a losing game. The solution could be to use only technologies over which we can have control, which would involve not using the most popular communication services and technologies. It’s a matter of trade-offs.
Privacy is one of the most important reasons to use exclusively libre software. The difference between libre and non-libre software is whether we have control over the program. In practice, non-libre software is often malware because developers, aware of the inability of users to repair any malicious functionality, are tempted to impose it.
A smartphone running exclusively libre software would not require or pressure users to provide their data to an untrustworthy company. Software’s actions would be known, learnable, and adaptable. The community could develop an alternative if the software does not respect the user. In other words, privacy problems would be, if not entirely avoidable, at least preventable and more contained.
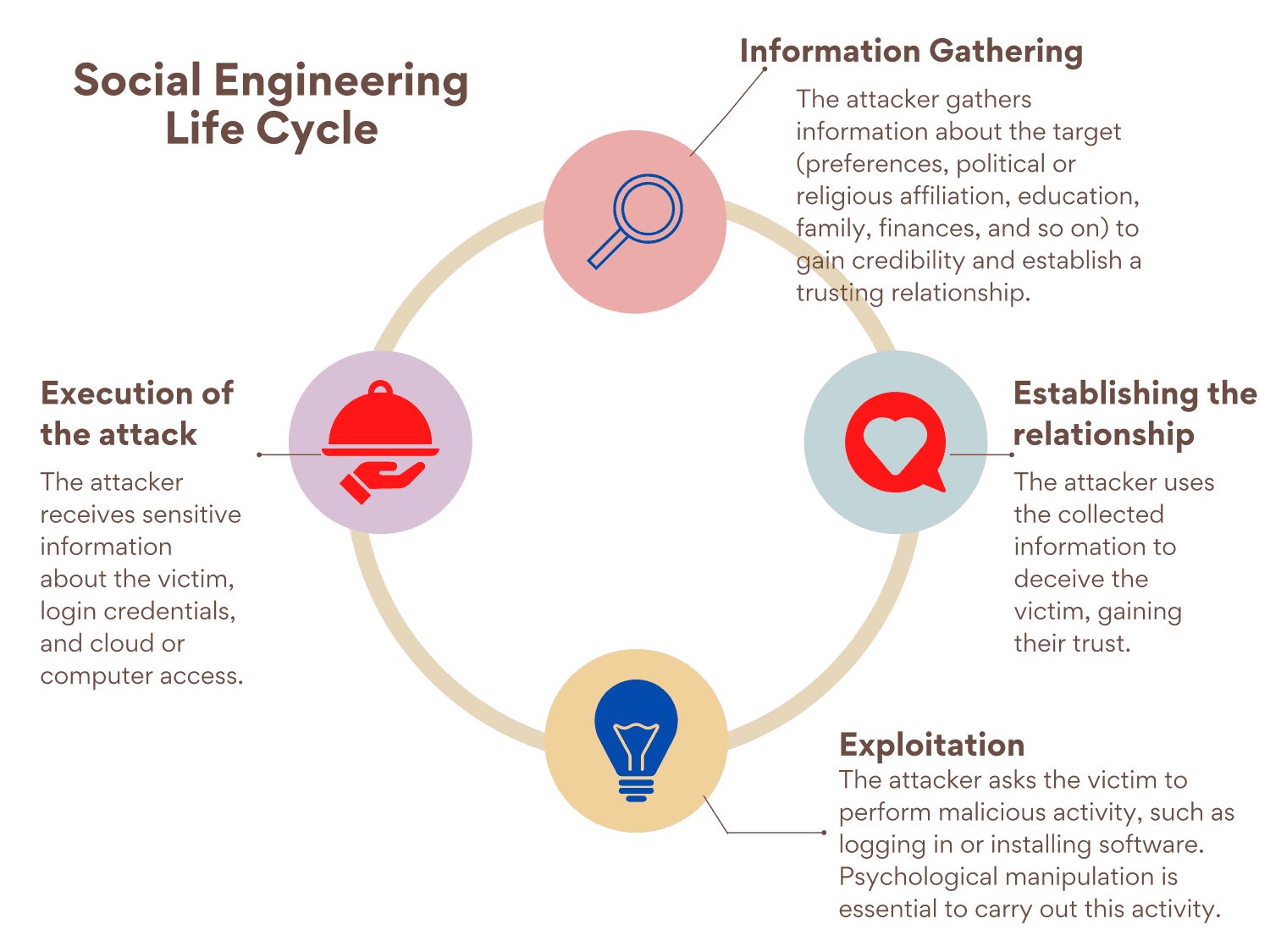
Social engineering relies on human error rather than vulnerabilities in software and operating systems. It uses psychological manipulation to get people to make security mistakes or provide sensitive information. The attacker will do anything to gain the victim’s trust or obedience, including using threats or posing as an authority.
There are too many types of attacks to describe them all. It all depends on the creativity of the attacker and the lack of awareness of the victim. Some types of attacks have become known even to the media, such as phishing. Others are still little known but fascinating for their cunning, such as baiting:
We essentially transfer trust from our network provider to the VPN provider by using a VPN. This choice can lead bad actors to exploit our trust. A worse aspect is that the consumer-oriented language on VPN websites uses a lot of hyperbole and unrealistic promises.
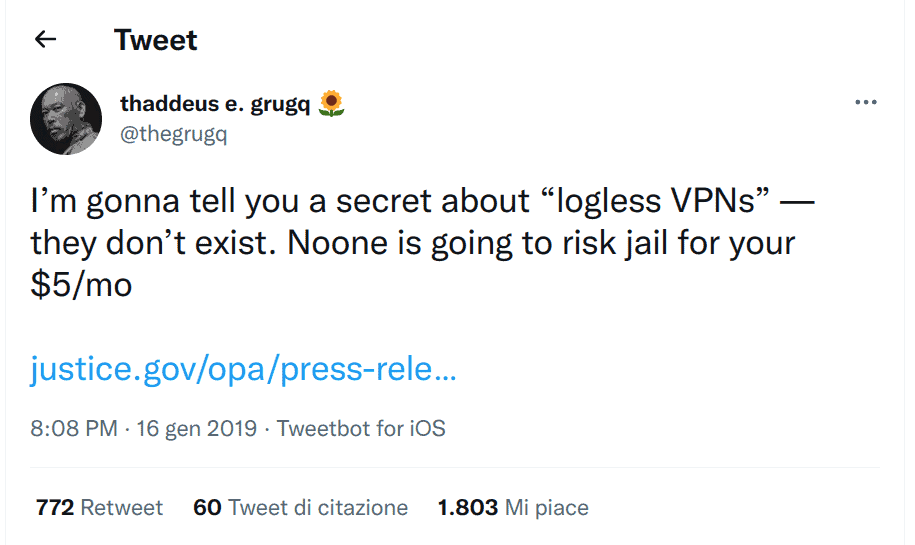
This issue is a hot topic that we can argue with firm evidence. VPNs often promise not to keep logs, leading privacy enthusiasts and criminals alike to assume that their data is private. But court documents, like when IPVanish handed over logs that weren’t supposed to exist, dispel this idea.
Moreover, this criminal complaint about cyberstalking and other cybercrimes (District of Massachusetts, USA) is very instructive, demonstrating that VPN services maintain logs of users’ activity. It also shows that FBI agents can expose even those who know all the tricks to anonymize themselves.
A lengthy report of Consumer Reports’ Digital Lab analyzed commercial VPNs to check security practices, data leaks, and privacy policies. This report is overall very discouraging. Among other issues, it demonstrates that some VPNs leave logs on users’ devices that may contain detailed and sensitive information. In some cases, user passwords are stored and transmitted in an unencrypted format.
Another deep investigation of Top10VPN shows that many VPNs fail to protect user privacy due to DNS and other leaks, and that almost all VPNs feature excessive permissions or functions with potential for privacy abuses.
As an additional concern, most apps appearing in the top results for VPN searches are free products from obscure and highly secretive companies. Most of them have Chinese ownership or are operated by companies located in mainland China. As the Free VPN Ownership Investigation reveals, they deliberately make it very difficult for consumers to find out anything about them.
Under no circumstances can we investigate the hosting providers of VPN companies or other third-party partners. It is impossible to determine whether these VPNs have unsafe functions or libraries, or what happens on their server-side:
DNS hijacking (also named DNS poisoning or DNS redirection) and DNS spoofing are practices to subvert the resolution of DNS queries. In addition to these problems that are difficult for the end-user to remedy, there are DNS leaks.
When using a VPN, a DNS leak occurs if a DNS request reaches a DNS server unprotected, often the DNS server of the Internet service provider (ISP). The personally identifiable DNS packets resulting from a DNS leak pose a severe threat to security and privacy, especially in countries with strict censorship and possible personal repercussions. Moreover, some ISPs use “transparent DNS proxies” to intercept all DNS lookup requests and proxy the results. In other words, they force us to use their DNS service without us knowing it.
We can check if this issue also affects our VPN with DNS leak testers.
WebRTC is a browser-to-browser communication for high-bandwidth applications like video chat that requires our public IP address. It can also bypass the VPN tunnel, so third parties can exploit WebRTC functionality to request our actual IP address. However, it’s a less common problem than DNS leaks.
We can test this issue with browserleaks.com/webrtc or similar tools.
Some VPN clients have an option to block our Internet traffic when the VPN disconnects, but it does not always work, as the previously reported VPN investigations show.
Many VPN clients require inappropriate and intrusive permissions such as GPS location, access to personal information, camera, microphone, contacts, SMS, ad so on. Aside from potentially malicious purposes, many of these intrusive permissions can arise from advertising practices or lousy development practices.
When using a proprietary VPN client, we rely on whoever developed and published it. Even if the source code were available, there is no guarantee that this code is identical to the code used to create the build we downloaded. It can contain viruses, spyware, and malware in general.
As we have previously mentioned, the only alternative is to use exclusively libre software. This approach can mean using a GNU/Linux distribution and its Network Manager, usually provided by default. Network Manager is compatible with any commercial or self-hosted VPN (such as OpenVPN) that provides configuration files with an .ovpn extension.
Websites can use many methods not prevented by any VPN to track users, such as device fingerprinting, browser fingerprinting, web cookies, tracking pixels, and more. Websites often request data to pinpoint people’s geographic location, such as WiFi networks, device location based on GPS, and cell tower identification (CDMA or GSM cell IDs). Various companies collect wide-ranging data beyond IP addresses and sell that information to data brokers.
coveryourtracks.eff.org is an Electronic Frontier Foundation project to test how well our browsers resist tracking and fingerprinting. We can easily find many other similar testers.
In this tutorial, we have seen that a VPN rarely offers absolute anonymity and no traceability in everyday life. We must be cautious about the false sense of security that any service in the hands of a third party, including a VPN, can give.
A VPN encrypts our traffic and hides our actual IP address from websites and peer-to-peer nodes. It’s useful when connected to Wi-Fi in airports, hotels, cafes, and libraries since it protects our connection from man in the middle and other common attacks. It helps to circumvent censorship or geographical blocks on websites and content. It also prevents ISPs from logging our Internet traffic. But, it usually doesn’t make us anonymous or untraceable.