Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll discuss two protocols that provide a secure connection for data transfer: SSL and TLS. We’ll explore the working procedure of the protocols.
Finally, we’ll present the core differences between them.
We use Hypertext Transport Protocol (HTTP) for transferring website data over the Internet. HTTP sends the data in a clear-text format. This clear text format works as long as we’re not sending sensitive personal data over the Internet, including credit card numbers and passwords. A hacker sitting in the middle can get access to sensitive information if the data sent by the sender is not encrypted.
HTTPS or secure HTTP was introduced to fix the security problem in HTTP. In HTTPS, we can send data between a computer and a server in encrypted form. Therefore, a hacker sitting in the middle can only extract the encrypted data. Although, in order to see the original message, the hacker would need a decryption key that the sender safely stores.
Moreover, websites without sensitive information are using HTTPS nowadays in order to enhance security. We use different port numbers for insecure and secure communications. For example, HTTP commonly uses standard port 80, while HTTPS uses port 443.
Secure socket layer (SSL) and Transport layer security (TLS) provides a secure connection between two devices on the Internet and the local network. Additionally, they also offer a mechanism to encrypt data being transferred between a device and a server. Moreover, the encryption mechanism helps prevent unauthorized access to sensitive data.
Both SSL and TLS provide authentication, encryption, and data integrity checks. A web browser connecting to a server commonly uses SSL and TLS. However, the secure version protocols, including HTTPS, FTPS, SMTPS, use TLS over SSL.
TLS is the successor of the SSL. TLS provides authentication of data by using asymmetric cryptographic keys. A website sends a digital certificate called SSL certificate to identify itself. Once a web browser checks the certificate, the data transfer proceeds further.
Usually, in an HTTP request, the server mainly provides authentication. Additionally, there’re cases when a client can also provide authentication, but it’s optional. Moreover, the client verifies the digital certificate of the server to ensure it’s a genuine website.
SSL/TLS encrypts data exchanged using symmetric cryptography for privacy. Additionally, it also helps ensure data integrity. We check the data integrity using a tag or a message authentication code (MAC).
TLS is a newer version of SSL with significant similarities, but it still has several differences. TLS is sometimes referred to as SSL/TLS due to similarities. Let’s now talk about the history of SSL and TLS.
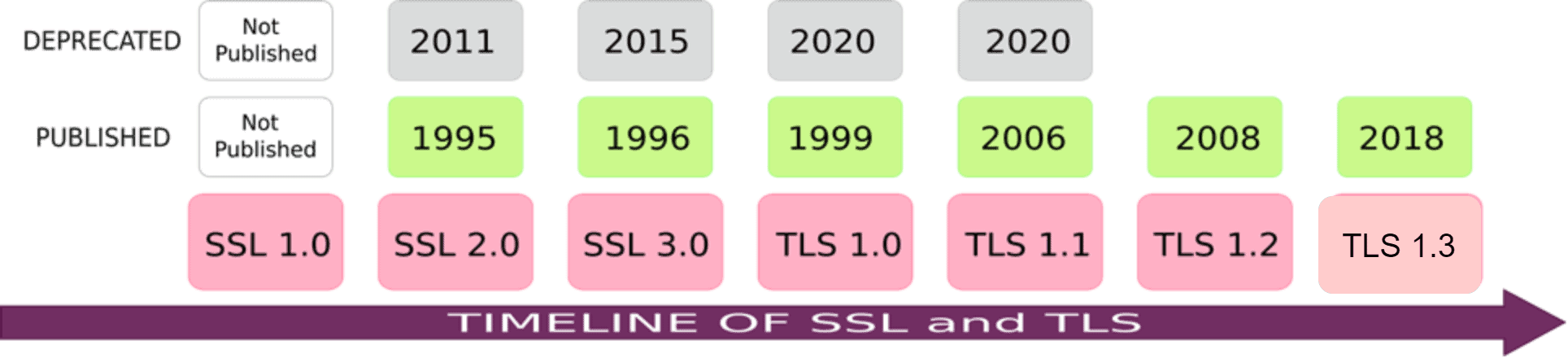
SSL 1.0 was developed in 1995 by Netscape and was never released. SSL 2.0 was published in 1995. An updated version, SSL 3.0, was released a year later in 1996. All the versions of SSL are deprecated mainly due to security flaws.
TLS 1.0 was released in 1999 by IETF. It was updated in 2006 as TLS 1.1. Furthermore, TLS 1.2 was released in 2008, followed by TLS 1.3 in 2018. Moreover, the TLS versions 1.0 and 1.1 are deprecated now. TLS 1.2 and 1.3 are the only non-deprecated versions of TLS as of 2022:
As all the SSL versions are deprecated now, let’s talk about the TLS handshake process.
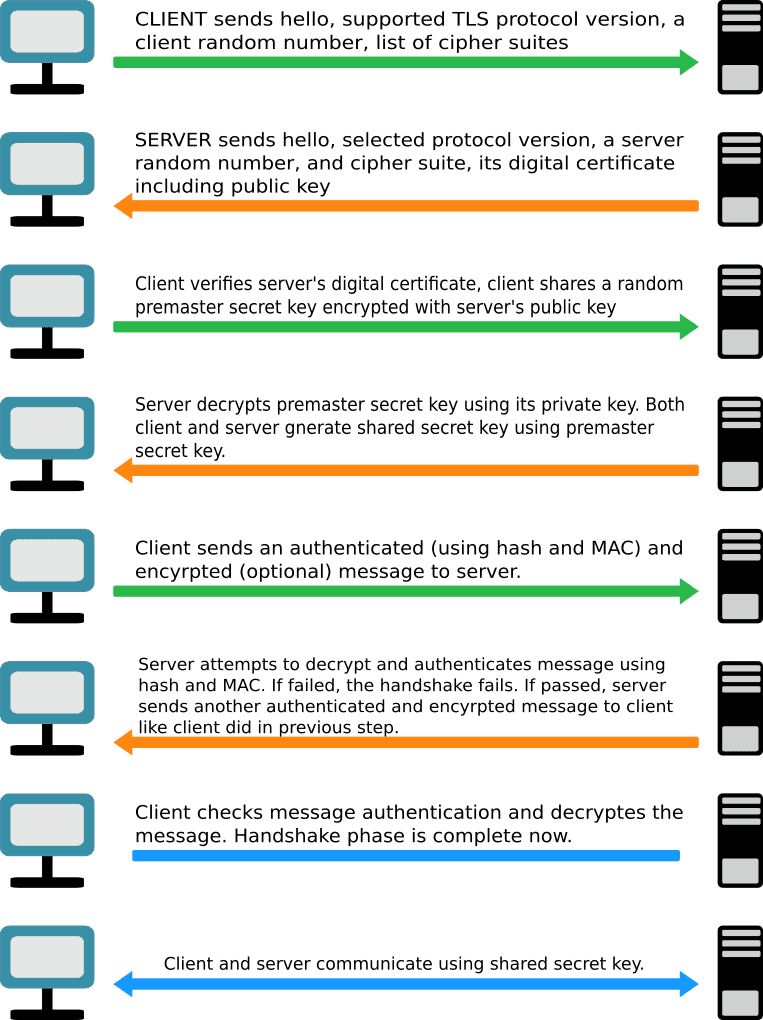
First, a handshake happens between a client and a server. Initially, the client sends a hello message, a list of TLS versions supported by the client, and a cryptographic algorithm to start the handshake process. Therefore, the server responds with a hello message alongside the selected TLS version, the cryptographic algorithm, and its digital certificate, including a public key.
As soon as the client receives the response from the server, it verifies the server’s digital certificate and shares a secret key encrypted with the public key of the server in order to make it safe from hackers. Next, the server decrypts the secret key using its private key. At this point, both the client and server have the key to encrypt and decrypt the data.
Moreover, now the client sends the encrypted data authenticated by MAC and hash to the server. As soon as the server receives the data, it starts the decryption and authentication process. On the successful completion, the server responds with an encrypted and authenticated message to the client. Finally, the client decrypts and authenticates the data using its secret key. This is how the SSL/TLS handshake works.
Now, if the client or server fails to decrypt or authenticate the data at any point, the handshake fails. Let’s now look at the diagram, which presents the handshake process briefly:
TLS uses a hash-based message authentication code (HMAC) for data integrity checks. TLS 1.3 utilizes authenticated encryption with associated data (AEAD), which provides both encryption and authentication. SSL uses MD5 and SHA1 based on a message authentication code (MAC).
Additionally, TLS provides a different set of cipher suites than SSL. TLS 1.3 cipher suite drops various legacy algorithms to provide more security in comparison to previous TLS versions. SSL generally uses the Fortezza cipher suite.
Let’s look at the core differences between SSL and TLS:
| TLS | SSL |
|---|---|
| More secure in comparison to SSL. | Less secure in comparison to TLS. |
| TLS 1.0 and 1.1 are currently deprecated but TLS 1.2 and TLS 1.3 are actively used as of 2022. | All the SSL versions are deprecated now. |
| Provides more alert messages than SSL. | Less alert messages in comparison to TLS. |
| Provides support to the alert messages generated by SSL. | No support provided for the alert messages. |
| Uses HMAC for data integrity. TLS 1.3 uses AEAD for both encryption and authentication. | Uses MD5 and SHA1 based on a MAC. |
| Doesn’t support the Fortezza cipher suite | Supports the Fortezza cipher suite. |
| Client sends an insecure Hello request and once secure connection is made communication switches to a port like 443 in case of HTTPS. | An explicit secure connection is made at a port. For example explicit HTTPS connection is made at port 443. |
In this tutorial, we discussed TLS and SSL protocols. We explained the working procedure with a diagram.
Finally, we presented the core differences between them.