Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Introduction to SSH
Last updated: March 18, 2024
1. Introduction
Secure Shell (SSH) is a popular networking protocol that lets us access a remote computer over an insecure network such as the Internet.
In this tutorial, we’ll dive into it and explore various aspects of it.
2. What Is Secure Shell?
Secure Shell or Secure Socket Shell is a network protocol. It is an application layer protocol that is in the 7th later of the Open Systems Interconnection (OSI) network model. It also refers to the suite of utilities that implements the SSH protocol.
Secure Shell also supports both password and key-based authentication. Password-based authentication let users provide username and password to authenticate to the remote server. A key-based authentication allows users to authenticate through a key-pair. The key pairs are two cryptographically secure keys for authenticating a client to a Secure Shell server.
Furthermore, the Secure Shell protocol also encrypts data communication between two computers. It is extensively used to communicate with a remote computer over the Internet.
3. Secure Shell Architecture
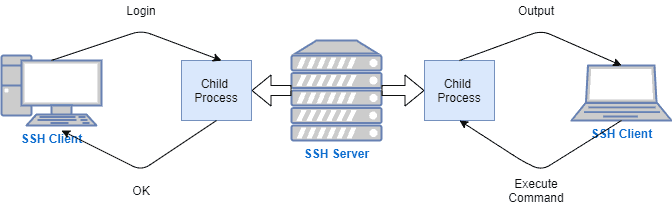
Secure Shell has a client-server architecture. Typically, a server administrator installs a server program that accepts or rejects the incoming connections. Besides, a user runs a client program on their system that requests the server. By default, the server listens on HTTP port 22.
4. Where Should We Use Secure Shell?
In most cases, the Secure Shell application is available by default with all operating system servers. SSH connections are used for a variety of purposes. For instance, the following are some of the usages:
- Communication between local and remote machines
- Remote access to server resources
- Executing commands in the remote host machine
- Performing numerous system administration tasks
Moreover, the key-based authentication provides convenient Single Sign-On (SSO) access across the remote hosts. This lets users move between their accounts without the need of a password.
5. Secure Shell Commands
Secure Shell provides several executable commands with additional features:
- ssh – for logging into a remote machine and for executing commands on a remote machine
- sshd – it’s an SSH server daemon process that waits for incoming SSH connection requests from SSH clients and enables authorized systems to connect to the localhost
- ssh-keygen – new authentication key pair for SSH, used to automate logins to implement Single Sign-On and to authenticate hosts
- ssh-copy-id – allows to copy, install and configure an SSH key on a server
- scp – an SSH-secured version of the RCP protocol that lets us copy files from one machine to another
- sftp – an SSH-secured version of the FTP protocol that is used to share files in Internet
6. How Do We Use Secure Shell?
The most common way to use Secure Shell is to log in to a remote computer, using the ssh command:
In the above command, we’ve used the ssh executable to connect to the server.example.com server with the admin user. The format of the command is user@servername. The user is the server user, and the servername is the name of the server. Besides, we can also use an IP address in place of the DNS or the server name. For example, the command, [email protected] lets user root logs into the server 10.1.1.2.
6.1. Creating Key Pair
We can also use SSH to generate the private and public key pair in your machine:
ssh-keygen -t rsa
We’ve used ssh-keygen command to create the private-public key pair. The public key is shared with the remote computer, and the private key is kept confidential for security.
6.2. Copying File
We can also use the Secure Shell protocol to copy files from one machine to another using the SCP command:
scp fileName user@remotehost:destinationPath
In the above command, fileName is the file to be copied in the current directory of the host machine. The remaining part of the command represents the user and server details with the destination path on the remote computer.
7. Secure Shell Tunneling
Secure Shell tunneling is a technique that enables a user to open a secure tunnel between a local and remote host.
Its main purpose is to redirect network traffics to a particular port or IP address. This allows a remote host to be directly accessible by the applications on the local machine. The destination may be on the remote SSH server, or that server may be configured to forward to yet another remote host.
8. Conclusion
In this tutorial, we have provided an overview of the Secure Shell protocol. First, we discussed what it is and the architecture. We then talked about how to use it and the areas where it suits most.
In the end, we discussed commonly used commands and talked about a useful feature – Secure Shell tunneling.