Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
A firewall is one of the most essential and critical devices in modern-day network security. It protects organizations and enterprises from unauthorized and malicious access and plays a pivotal role in the way we work with the Internet.
In this tutorial, we’ll discuss firewalls and their various aspects.
A firewall is a network security device. Its primary purpose is to inspect incoming and outgoing traffic and decide whether to allow or block it based on a predefined set of rules. Its purpose is also to establish a barrier between the internal network and incoming traffic from external sources, such as the Internet, to block potentially malicious traffic.
Firewalls have been the first line of defense in the area of network security for decades, and its use is still widespread. They can be a hardware device, software, or a combination of the two.
An example configuration is shown below:
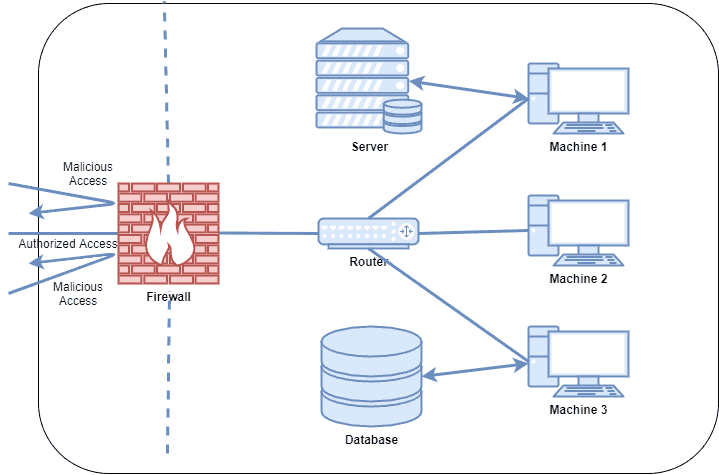
A firewall carefully inspects incoming traffic based on a predefined set of rules. It filters the incoming traffic from unsecured networks or malicious sources to prevent attacks and unauthorized access.
A firewall typically protects a computers’ entry point or the ports. For example, to access a Unix machine remotely, we log in through an SSH client through SSH protocol. In this case, we reach the remote server’s port 22 where the SSH server is running.
Firewalls can either be software or hardware, and it’s fine to configure both in a network. A software one is an application that is installed on each computer and regulates traffic through port numbers and applications. A physical one is a piece of equipment installed between the network and the gateway.
As the name suggests, this type inspects the incoming network packets and decides to let them through based on preconfigured security policies. Packet-filtering validates the packet’s source and destination IP addresses. This is the most common firewall type.
Packet-filtering is further classified into stateful and stateless categories:
Although packet-filtering firewalls are effective, they provide limited protection. These filters usage is also minimal: they can’t determine if the packet contents of the request can adversely affect the application. Most notably, a malicious request from a trusted source address can cause catastrophic damage to the application without the firewall having any knowledge about it.
The next-generation firewall (NGFW) combines traditional firewall technology with smart features, such as anti-virus, encrypted traffic inspection, and more.
Besides, NGFWs include deep packet inspection (DPI), which inspects the data within the packet itself, enabling users to more effectively identify, categorize, or stop packets with malicious data. This is a more advanced capability compared to the packet-filtering, which only examines the packet headers.
Proxy firewalls filter network traffic at the application layer level. The proxy acts as an intermediary between two connecting systems. The incoming request to the firewall is evaluated against a set of security rules configured in the proxy and then permitted or blocked.
Moreover, proxy firewalls monitor traffic for application layer protocols such as HTTP and FTP. They use both stateful and deep packet inspection to analyze traffic.
Network Address Translation (NAT) firewalls let multiple devices with independent network addresses connect to the Internet using a single IP address. Thus, they translate distinct IP addresses to a common IP address to keep individual IP addresses hidden. As a result, attackers scanning a network for IP addresses can’t capture specific details. Thus, it enables better security against attacks.
A NAT firewall is similar to a proxy one. Both act as an intermediary between a group of computers and outside traffic.
In this article, we’ve discussed the firewall and its role in securing organizations.
First, we discussed what a firewall is and how it works. Then, we explored various types of firewalls – such as basic packet-filtering ones to more advanced NAT firewalls.