Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: May 24, 2023
Information is a valuable asset targeted by all types of hackers. In addition, the number of internet-connected devices is dramatically increasing in the current digital age. That’s why cybersecurity attacks constantly evolve, and information security has become a considerable challenge.
In this tutorial, we’ll learn about four categories of cybersecurity attacks: interruption, interception, modification, and fabrication. We’ll study their characteristics and differences. Furthermore, we’ll show some examples and ways to shield against them.
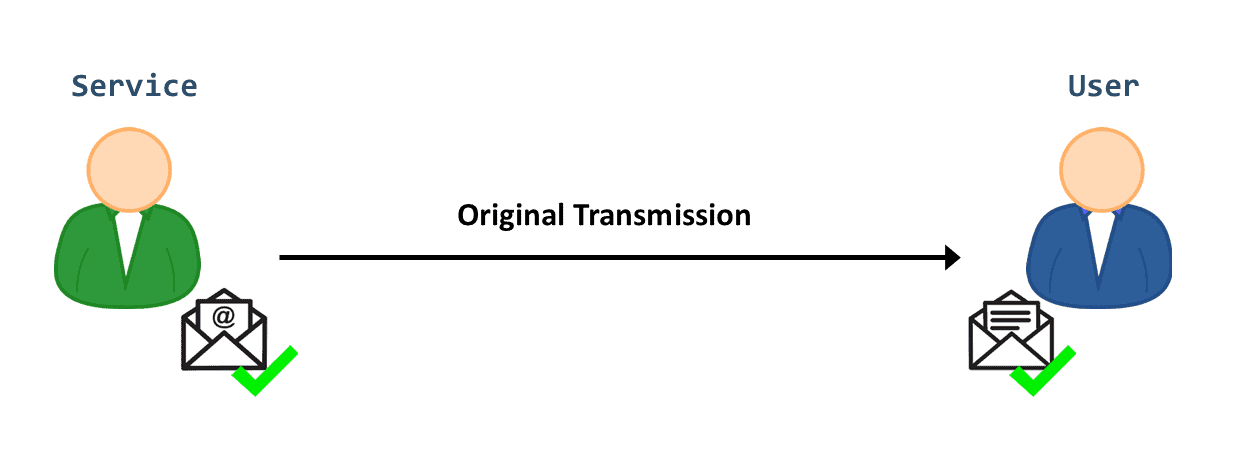
Let’s start with the first category of attacks, interception. Usually, data communication occurs when two connected entities exchange a message over the Internet:
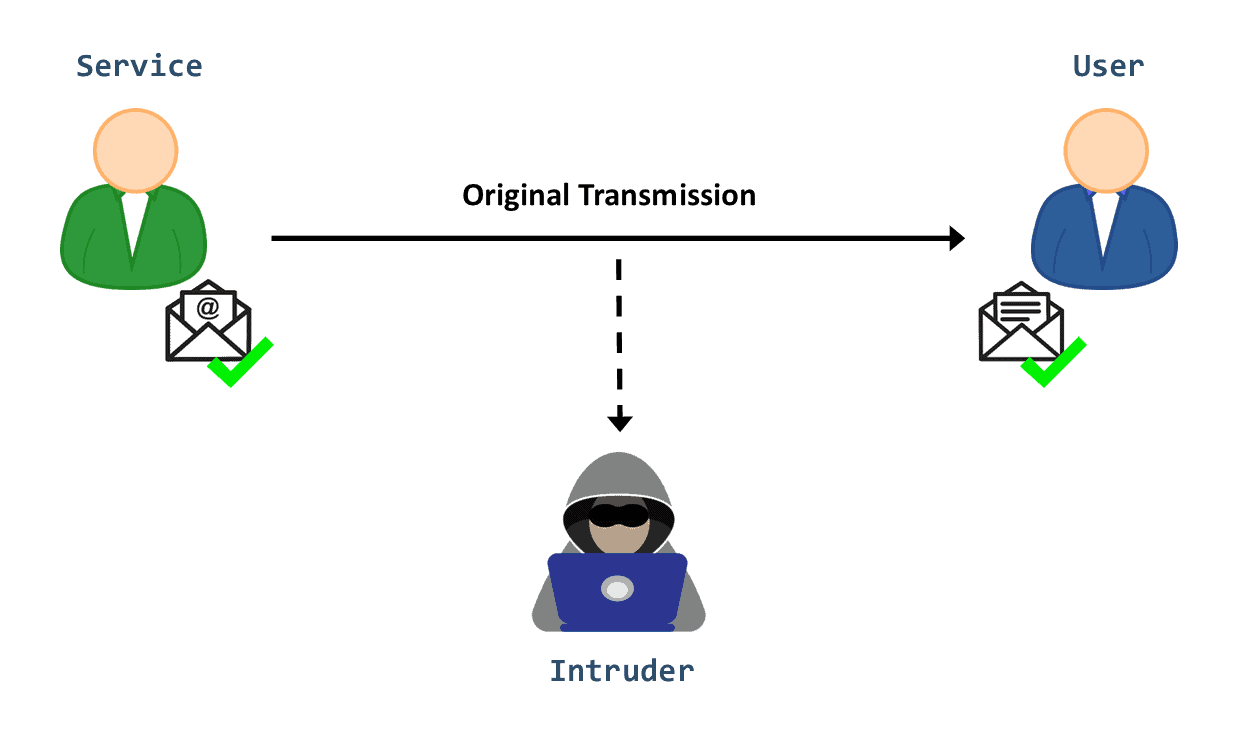
In the case of an interception attack, a malicious actor can access private or confidential information with no legitimate authorization. Eavesdropping attacks are a typical example of this category of attack. Namely, an intruder can refer to several techniques, such as packet sniffing and man-in-the-middle (MITM).
Generally, he aims to obtain critical information such as passwords and credit card numbers or to disturb data exchanges on the network. When effectively executed, it can be very hard to identify traces of the attack:
This category of attacks is mainly a threat to data confidentiality. We can mitigate it by encrypting communications, avoiding untrusted Wi-Fi networks, and regularly updating our software.
Let’s examine the second category of attacks, interruption. This form of attack manifests when a network service or a system asset is disrupted or destroyed:
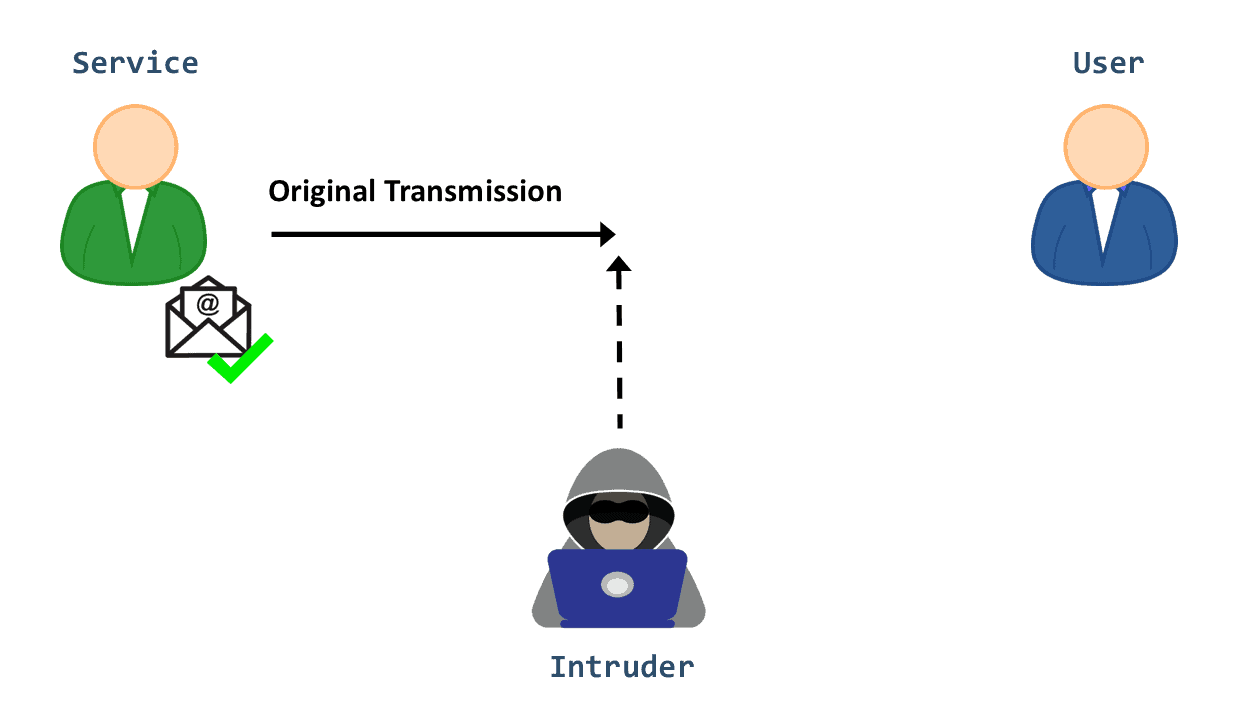
As a result, legitimate users can no longer reach it, either permanently or temporarily.
For example, an attacker may steal or damage a hardware/software component. He can also overwhelm a server host with requests so that it can’t respond, causing a DoS attack. Another example is using malware, such as viruses or trojans, to delete data or disable a system’s functioning.
This type of attack is a threat to data availability.
To protect against interruption attacks, we need appropriate precautions such as firewalls and system backups. Moreover, we can use cloud-based solutions and Content Delivery Networks (CDN) to boost security against these attacks and keep our system and network operable.
The third category is modification. This one involves not only gaining access to the asset but also manipulating it:
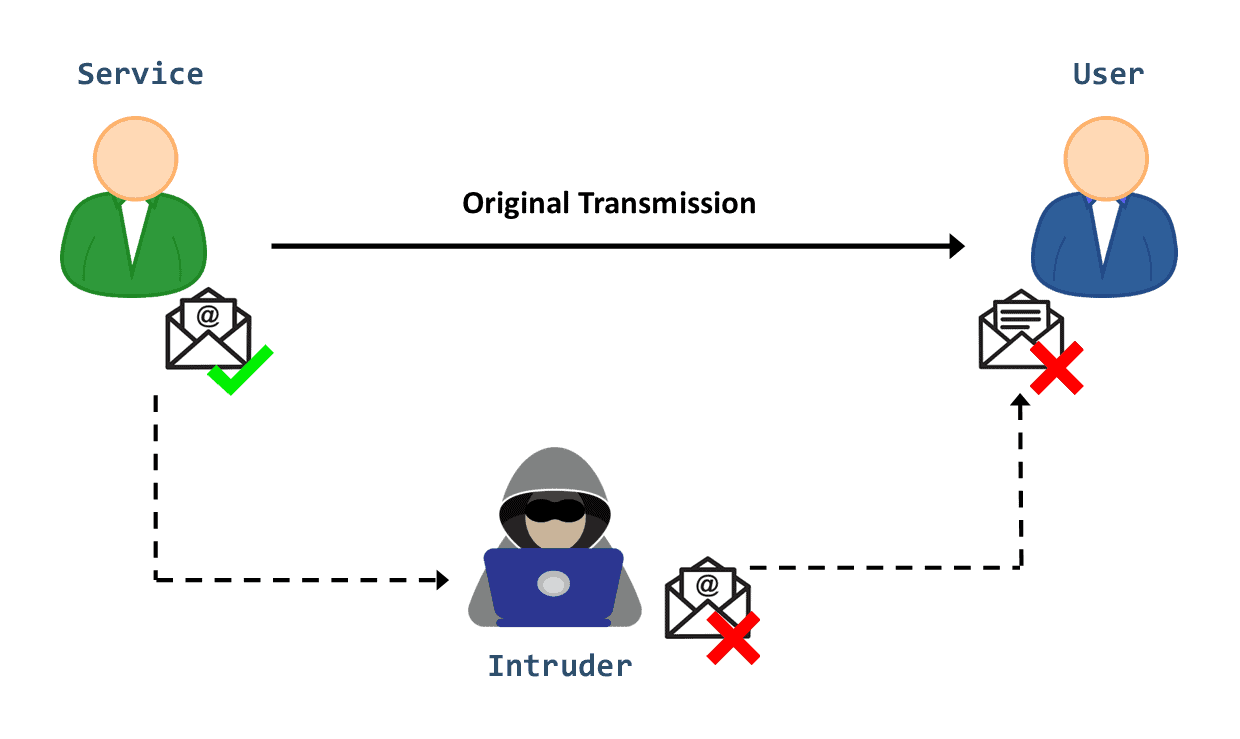
The man-in-the-middle attack (MITM) is a notable example. After intercepting data, the attacker can reconfigure the system hardware, remove a message in a network or modify its content. Cross-Site Scripting (XSS) attack is a second example where the hacker injects malicious script into a web application to alter its content or to obtain sensitive data illicitly.
Modification is primarily an attack on integrity. However, it can also manifest as an attack on availability. For example, let’s say the target is a configuration file that controls how a service is delivered. When manipulating its content, that service will no longer be available.
We can implement several techniques to prevent a modification attack, including Intrusion Detection Systems (IDS), data encryption, and Access Controls.
Now, we’ll go through the last category of cyber-attacks, fabrication.
Fabrication occurs when an intruder injects bogus data or creates a false trail in the system. For example, a hacker can execute identity spoofing by creating a fake version of a legitimate user. Then, he can attempt to commit fraud or hijack a bank account:
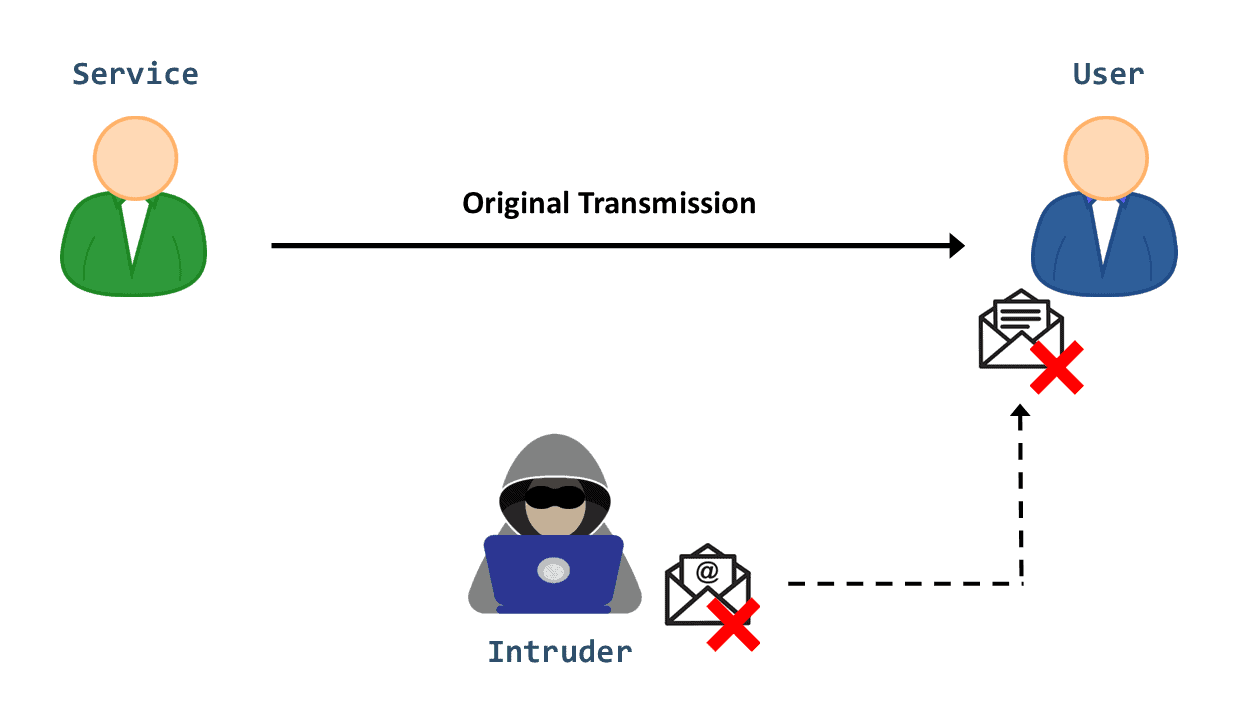
Further, there are other techniques to carry out a fabrication attack, such as SQL injection and phishing attacks.
Fabrication attacks mainly affect data authentication. That’s the case when the intruder creates a spoofing attack and impersonates a user’s identity or IP address. Meanwhile, fabrication can also threaten the availability objective of the CIA triad; for instance, injecting an overdose of traffic into a network can block a service.
We can mitigate fabrication attacks by using digital signatures and data encryption or by implementing firewalls in the network.
We can further classify these attacks as active or passive. Here’s a summary:
| Attack Category | Characteristics | Examples | Type |
|---|---|---|---|
| Interception | An unauthorized actor access a service or information shared between two legitimate users |
|
Passive |
| Interruption | An unauthorized actor disrupts a service or destroys hardware |
|
Active |
| Modification | An unauthorized actor gains access to a service or data and tampers with the content |
|
Active |
| Fabrication | An unauthorized actor inserts malicious data in the system |
|
Active |
We can also define these attacks by which security aspect of the CIA triad they attempt to affect:
| Attack Category | CIA Triad | Mitigation Techniques |
|---|---|---|
| Interception | Confidentiality |
|
| Interruption | Availability |
|
| Modification | Integrity and Availability |
|
| Fabrication | Authentication and Availability |
|
Information security is always an evolving challenge with the continuous advent of communication and information technologies.
In this article, we talked about four types of security attacks: interception, interruption, modification, and fabrication.