Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In our everyday lives, we are concerned about different security aspects. We commonly have security protocols followed, for example, for driving, working, and living in a society in general terms. Examples of these security protocols are using a seatbelt when driving or protective clothing and equipment for working (when required).
In the digital world, it is not so different. Securing data requires paying attention to multiple relevant aspects and preparing the system to deal with them.
For instance, we typically control access to sensitive data. Thus, we allow only authorized people to read and write it. Moreover, we also aim that, for those people, the sensitive data are always correct and available.
The above example depicts what we call the Confidentiality, Integrity, and Availability (CIA) triad in computing systems. This triad summarizes the security aspects of digital data and systems.
In this tutorial, we’ll investigate what means each security aspect of the CIA triad. First, we’ll study what security means in computing systems at a high level. Thus, we’ll explore each particular security aspect of the CIA triad.
First, we can understand security in computing systems in two ways:
Hardware security refers to keeping the physical equipment safe. Thus, we can achieve this kind of security by restricting access to the hardware. We can do that, for instance, by using secure rooms with locks, alarms, and cameras, to host our hardware devices.
Protecting software and data, however, is a complex task. It commonly requires installing security software, deploying security network functions, and configuring user privileges, in addition to other actions to guarantee confidentiality, integrity, and availability of digital systems and data.
Particularly, software and data security became a huge concern after the 2000s, when the Internet became very popular. With networked systems, malicious programs and hackers could start acting to attack systems and steal data kept anywhere in the world.
So, the academy and industry dedicated efforts to find practical manners to enforce the CIA triad in computing systems. In the following sections, we’ll explore each one of the security aspects related to the CIA triad.
The confidentiality aspect of the CIA triad regards the control of who accesses data. Robust systems in terms of confidentiality prevent sensitive data from being accessed by unauthorized entities. So, we have a confidentiality breach when data leaks without the proper control.
Taking into account the content of a given file, for example, we can classify it as being more or less sensitive. However, the simple presence of a file in a system or its meta-information (pointing out, for example, the file creator) can also be classified as sensitive data.
Thus, besides granting confidentiality to the written data, such as files and databases, we also must attempt to make the operations and communications confidential.
In practical terms, there are several ways to improve the confidentiality of data and systems. Let’s see some of them:
The following image exemplifies the process of accessing data protected with an authentication plus encryption scheme:
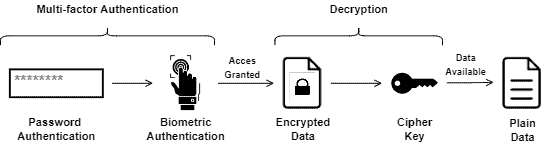
Besides the previously cited manners to improve confidentiality, it is relevant that the design of the systems makes it possible to keep data secured. Demilitarized/militarized zones are examples of a system design that deals with different confidentiality levels.
In the most strict definition, the integrity aspect of the CIA triad implies that unauthorized entities can not modify a given data.
However, there are multiple ways to modify data, even when encrypted. For instance, we can suffer a man-in-the-middle attack when transmitting sensitive data. In this case, the attacker can change particular bytes of the messages, compromising the integrity of the entire transmitted data.
Thus, instead of pursuing to enforce integrity in its restricted definition, which is very hard, we can work with a lighter concept of it: unauthorized modifications of data must be identifiable.
One method to achieve integrity is hashing data and saving the generated hash. So, before using the data again, we submit it to the same hash function and compare the generated hash code with the previously saved one: if they match, we can assume that the data was not modified.
The following image depicts an example of the previously presented process:
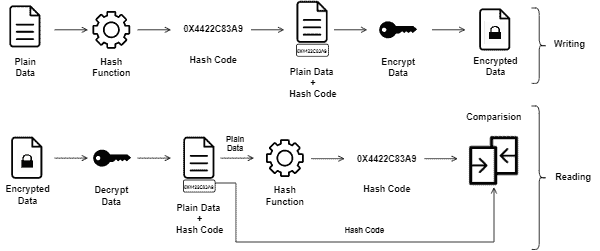
Of course, hashing mechanisms map any-sized data to a discrete and finite space of hash codes. In this way, different data will generate the same hash eventually, an event (called a hash collision) that can compromise the integrity verification process.
However, well-designed hash mechanisms employ different techniques to avoid collisions, turning them into rare and controlled events.
The last aspect of the CIA triad, availability, motivates the efforts to achieve integrity and confidentiality for data and systems. We can ask ourselves: for which purpose have we made our data and computing systems confidential and correct if we can not access and use them?
The answer is “for no reason!”. We should indeed protect and keep our data and systems intact, but they must be widely available for the authorized entities when necessary.
So, there exist two big topics about availability. The first one regards providing standard interfaces to the authorized entities proving their identity, and passing security barriers to access the required resources.
The second topic is to avoid the interfaces provided to access resources becoming a threat. In such a scenario, distributed denial of service attacks can be employed to make a resource unavailable, find vulnerabilities in internal systems, and distract administrators from other malicious attacks.
Granting the availability of resources is not a trivial task. We must consider employing mechanisms that adequately scale the interfaces to support a growing number of authorized entities’ accesses.
Finally, we should also consider employing security solutions and network functions to identify and mitigate distributed denial of service attacks.
In this tutorial, we studied the security aspects of the CIA (Confidentiality, Integrity, and Availability) triad. At first, we reviewed general concepts of security in computing systems. Thus, we explored each aspect of the CIA triad, presenting examples of applications and potential threats.
We can conclude that accomplishing the CIA triad aspects must be a clear objective in the context of data and systems security. So, protecting data and systems, granting their integrity, and keeping the resources available to authorized entities are crucial steps forward for creating trustable digital environments.