1. Introduction
In this tutorial, we’ll examine credential stuffing and password spraying attacks. Our main objective is to understand how password attacks work. Thus, we can focus on credential stuffing and password spraying attacks, studying their characteristics, similarities, and differences.
In the first section, we’ll review the category of password attacks, approaching their objectives and typical methods. So, in the following sections, we’ll deeply explore both the credential stuffing and password spraying attacks, finally comparing them in a systematic summary.
2. Password Attacks
There are multiple ways for users to prove their identity to access a system. Usually, authentication methods consider elements we are, have or know (sometimes all of them). These elements, in turn, are processed by algorithms that compare the provided data with the stored one, granting access or not for the requesting user.
When we talk about authentication methods based on elements we expect the user knows, the most popular resource employed is passwords.
We can understand passwords as personal and secret data kept by a user and used to prove his identity, thus accessing restricted systems and data.
Nowadays, passwords protect many sensitive and value-aggregated data around the world. Due to this fact, hackers and other malicious users created several strategies to steal or infer passwords.
Popular examples of password attack strategies are brute-force, keylogger, phishing, man-in-the-middle, traffic interception, credential stuffing, and password spraying.
Each password attack has specific characteristics and execution techniques. However, all have the same final objective: find a valid user credential and use it to access a given system or data.
In the following sections, we’ll particularly see two of these passwords attacks strategies: credential stuffing and password spraying.
3. Credential Stuffing
Currently, we have multiple accounts to access services online. These accounts, in turn, commonly require a password defined by the user. Thus, due to the existence of many accounts, the users tend to choose easy-to-remember passwords and, sometimes, the same password several times.
This scenario, however, is what enables credential stuffing attacks to happen.
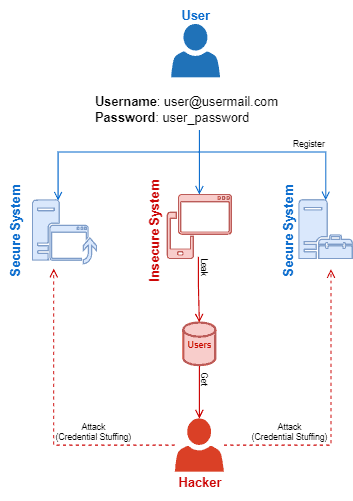
In summary, credential stuffing attacks consist of using leaked credentials of a given system to try to access other systems.
Particular systems employ more rigorous security schemes to keep user credentials than others. For example, some systems store salted hashes instead of plain text passwords. Since a hash is not reversible, these systems’ databases are more robust against data leakage.
On the other hand, some systems store the users’ plain text passwords in their databases. It makes the stored credentials very vulnerable in case of data leakage.
In this way, the most relevant precondition of a credential stuffing attack is the attacker accessing these insecure credentials databases.
At this point, we should highlight that even databases with hashed passwords may be insecure. Choosing bad hashing functions makes them password hashes vulnerable to brute force and rainbow table attacks.
Once the attacker gets users’ credentials, he can test the combinations of usernames and passwords in multiple and different systems. Many attempts, of course, will fail. However, the probability of a few attempts working is high, given an enormous number of credentials stolen and multiple systems tested.
The following image depicts, on a high level, the processes of a credential stuffing attack:
3.1. Precautions and Countermeasures
Avoiding credential stuffing attacks include efforts of both service providers and users. Next, we describe some of the main precautions and countermeasures regarding these attacks:
- Secured Systems: this point considers the systems adopting strategies and mechanisms to avoid being attacked (firewall, antivirus, DMZ, …) and the credentials being reused in case of leakage (hash, salted hash, …)
- Restricted Attempts of Logins: bots make most credential stuffing attacks. So, restricting the number of logins attempts and using bot detector mechanisms (such as captchas) help to mitigate these attacks
- Using Different Passwords: for the users, the definite strategy to avoid credential stuffing attacks is using different passwords for heterogeneous systems
4. Password Spraying
Managing a large number of user accounts is hard. As discussed in the previous section, we usually have many accounts with passwords to access different services. So, to make the process easier, we sometimes opt for using easy passwords.
But, easy passwords are insecure. After being used several times, these passwords became popular and well-known. This is the exact scenario that enables password spraying attacks.
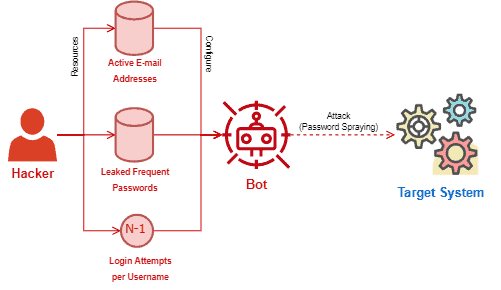
In summary, password spraying attacks are dictionary attacks that employ frequently used passwords to try to get access to systems through a list of potential usernames.
Lists of common passwords are easy to find. Many entities compiled these lists from leaked bases of passwords, thus making them available online.
Lists of usernames are more challenging to get. However, multiple systems adopt the users’ e-mail addresses as usernames. And finding lists of active e-mail addresses is not a very difficult task.
With these lists, the attackers choose a target to try to get some valid credentials. With the selected target, the attackers discover how many invalid login attempts the system supports until blocking an account. Suppose that the number is (N). Thus, the attack will execute (N-1) login attempts for each potential user in the list.
Most of the login attempts will probably fail, and the attackers will get a few valid credentials from a list of passwords and usernames. So, the main objective of a password spraying attack is not getting all the users’ credentials but (with luck) some users’ credentials.
The following image shows a simplified workflow of a password spraying attack:
4.1. Precautions and Countermeasures
The most effective way to reduce the success of password spraying attacks is on the users’ hands by avoiding using common and frequent passwords to protect their accounts. However, there are some precautions and countermeasures regarding the owners of the systems too:
- Password Creation Policies: the idea behind adopting policies for password creation is to make the users use non-obvious passwords. In such a way, the password policies must make simple combinations unavailable for the users
- Reduced Number of Login Attempts: the higher the number of admitted login attempts for a particular user in a given time, the more susceptible the system is to password spraying attacks
- Login Auxiliar Security Mechanisms: similar to credential stuffing, bots execute most password spraying attacks. Using captchas and other verification mechanisms may mitigate such attacks
5. Systematic Summary
Authenticating users became a crucial task due to the increasing number of online services. A usual authentication method consists of correlating usernames to passwords, granting access to a system when a user provides a valid combination.
Although a popular option, password-based authentication is susceptible to multiple attacks. These attacks, in turn, aim to steal or infer valid credentials (username plus password) to access systems as authentic users.
Two particular attacks in this context are credential stuffing and password spraying.
In short, credential stuffing aims to use leaked credentials from a system to access other systems. A password spraying attack, however, uses lists of potential usernames and common passwords, thus trying to infer valid credentials and get access to a system.
The following table summarizes some relevant characteristics of these attacks.
Finally, we highlight that these attacks are password-focused. In such a way, using multi-factor authentication is an efficient option to avoid them.
6. Conclusion
In this tutorial, we studied credential stuffing and password spraying attacks. First, we had a brief review of password attack strategies. So, we examined credential stuffing and password spraying attacks, focusing on their characteristics and requirements. Finally, the studied attacks got compared in a systematic summary.
We can conclude that password-based authentication is essential for several systems nowadays. However, this authentication method should be well-planned to avoid being exploited by attackers.