Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll discuss antivirus software in detail. We’ll also explore the need for it. Finally, we’ll explore various virus detection methods used by antivirus software.
Before discussing antivirus, let’s first talk about viruses. In our daily life, a biological virus causes diseases or malfunctions. When we get infected with a virus, our body doesn’t function properly and displays abnormal syndromes. The same thing happens a computer virus infects a system.
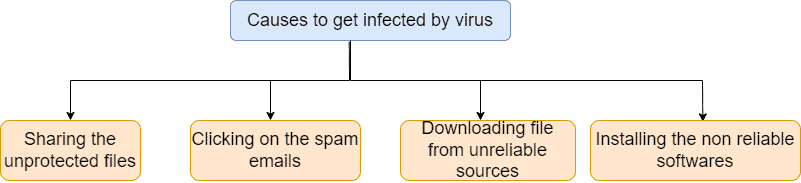
A computer or digital virus is a computer program or code that causes malfunctions in our computer system. Each virus has a different way of impacting systems. There are various ways a virus can enter into systems. The most common mistakes which increase the chances of getting infected by viruses are sharing unprotected files, clicking unknown links inside an email, and downloading software from unreliable sources:
We can divide computer viruses into three broad categories: worms, trojans, and ransomware:
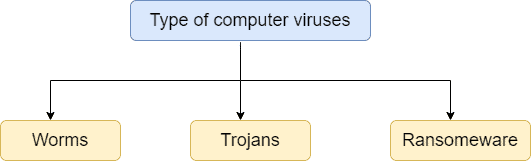
Computer worms spread from one system to another using the security flaws of the systems. On the other hand, trojan viruses hide their true intentions and enter the system as a legitimate file. Later on, they start performing malicious activities on the targeted systems. Finally, ransomware encrypts the victim’s crucial files and asks for a ransom in return for the decryption key.
As we take antivirals medicines to prevent us from virus infection, antivirus software in computing does the same for computers. An antivirus is a computer program or software which prevents a system from being infected by computer viruses.
Antivirus software is essential for any machine which has an operating system. Without antivirus software, a system becomes very vulnerable. A hacker can take this opportunity to exploit the data, take control of the system and misuse it.
Therefore, antivirus software can protect systems from dangerous computer viruses, spyware, trojans, worms, bots, and ransomware attacks. It can reduce the probability of further spread of malicious software or files. Furthermore, it can block unnecessary spam emails and auto-generated ads.
A common practice of hackers is to send a malicious file to the victim’s system and create a gateway to send crucial information to the hacker’s system. Antivirus effectively monitors the incoming and ongoing traffic from a system. Hence, it can block any suspicious activities while receiving or sending information.
An easy way to carry and transfer data is to use removal devices like a USB pen drive. Antivirus software automatically scans the files from the removal devices and removes any malicious files found.
Additionally, using antivirus software, we can set a rule and restrict the access of certain websites in order to boost the security of the systems.
Most of the antivirus software runs in the background and scans the system continuously or periodically. In case of detecting any suspicious file or application, it either removes or informs the user to handle the file immediately.
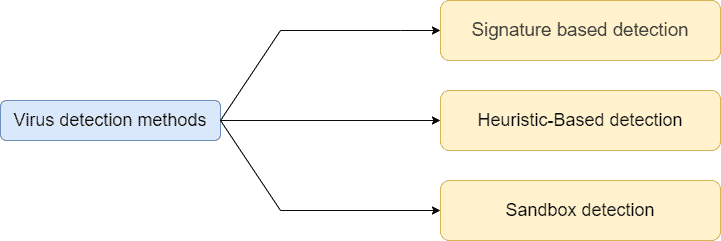
Now let’s talk about the methods antivirus software uses to detect malicious programs or files. In order to detect viruses or malicious files, the antivirus software follows three main approaches: signature-based, heuristic-based, and sandbox detection methods:
All the files in a computer system have a signature associated with them. A signature means a digital fingerprint or pattern of a file. The signature can be a pattern of bytes or some kind of digital certificate associated with the file’s header.
We can view the digital signature of any file in the Windows OS by right-clicking on the file and going to the properties. Next, we need to go to the digital signature tab in the properties window. Here, we can view the digital signature of a file.
It’s one of the most basic and widely used methods to detect the virus. Antivirus software companies maintain a massive database of digital signatures of the different types of files, viruses, and malware. When installing any antivirus software, the whole signature database comes with it. Therefore, when we install any software or download any files, antivirus software running in the background scans that file and matches the digital signature with the signature database.
The benefit of the signature-based detection method is that a single signature of a certain type of virus can match with a set of malicious files with some commonalities. In this way, with a single signature, we may be able to detect several malicious files.
If the digital signature of the newly-downloaded file matches with any malicious signature from the existing database, it notifies and warns the user. Although antivirus software keeps the signature database updated, there can be files for which there’s no match in the signature database. In such a case, antivirus won’t be able to decide whether the newly-downloaded file is safe or not.
Heuristic-based detection is also commonly used for the detection of the virus. In this method, there’s an algorithm to find the source code of the malware program without using the signature of the program. This detection method is beneficial for identifying new unknown and modified versions of known viruses.
Heuristic-based detection performs better in handling viruses compared to signature-based detection. In signature-based detection, antivirus must have the signature of all types of available malware. Hence it’s highly limited and entirely dependent on the signature database. If it doesn’t have the signature of any specific malware, it’ll not be able to detect. Heuristic-based detection works better in such cases.
It is usually faster than other detection methods because it doesn’t have to run the program all the time in the background to check the signature or behavior of the program.
The potential issue of the heuristic-based detection method is to generate false-positive warnings for perfectly safe codes. When scanning a sample file, an antivirus with a heuristic-based detection method only provides the threat name. However, the heuristic-based detection method provides optimum protection from known and unknown viruses.
In this type of detection technique, antivirus software runs the program or file in a virtual environment before allowing them to enter the actual system. The primary purpose is to record the files’ behavior and analyze them automatically through a weights system in the sandbox. The goal of the analysis is to check the purpose of a file and if it displays any malicious behavior. Antivirus will allow a file to execute in the real environment only if it’s safe.
The sandbox detection method not only decides the malicious nature of a file but also provides detailed information about the file. It’s a slow process because, after the installation, the antivirus has to execute the program in a remote or virtual environment. Additionally, it has to wait for the results of behavioral analysis. Therefore, the detection method takes time, and it’s not ideal for small systems like laptops or desktops. Big organizations where security is more critical than time mainly uses antivirus with sandbox detection.
After the detection process, there are different types of optional scans performed by antivirus software to detect malicious files accurately. The significant advantage of the sandbox detection method is that it opens the file and predicts the actions the file can execute in a real system. Additionally, instead of giving a binary result, it provides a detailed file report.
The main limitation is the time required to complete all the processes involved in the sandbox detection method. Additionally, it needs a separate virtual environment in order to execute and collect the behavior report.
In this tutorial, we discussed antivirus software. We talked about various harmful computer viruses. Finally, we explored three methods that are used by the antivirus software in order to detect viruses.