1. Introduction
Authentication is a historical concern in different scenarios. Proving that we are ourselves to access some digital or physical resource is a frequent need. So, human beings created different manners to do that over time.
Authenticating a person (or something that a person did) requires a careful examination of how we are and behave, what we have in our possession, and what we know about particular things. These aspects can provide sufficient evidence of authenticity.
However, according to the level of security requested to access a specific resource, we’ll need more than one proof of authenticity. In these cases, we can combine both multiple and different evidence to do the authentication process.
So, in this article, we’ll study the multi-step and multi-factor authentication processes. First, we’ll have a brief review of authentication concepts and methods. Thus, we’ll investigate how multi-step and multi-factor authentication works. Finally, we’ll systematically summarize and compare these authentication alternatives.
2. Authentication
First of all, we need to differentiate identification and authentication. Identification is the ability to identify a person or object uniquely. Authentication, in turn, consists of the processes to prove that identification is genuine.
So, the identification provides who or what will be next authenticated. Supposing a simple login page, an user ID identifies a person while the password does his authentication.
In the digital world, it is usual to authenticate users, regardless of whether they are people or other digital systems. However, the authentication process is before the digital world.
For instance, we can authenticate people through their documents and physical keys. Furthermore, it is possible to authenticate paintings based on their signatures, colors, style, and degradation.
In short, authentication (digital or not) is based on three main factors: what we have, what we know, and what we are. Let’s have a look at each one of them:
- Things that we have: authentication by things we have uses physical or digital resources in our possession. Examples of these resources are from keys and cards to authentication tokens synchronized with particular servers
- Information that we know: authentication by what we know is the most common form of authentication nowadays. In this case, we employ information held particularly by the user to authenticate him. Examples are PIDs and passwords
- Elements that we are: the last factors consider resources intrinsically related to the user. Unlike things that we have that we can lose, what we are don’t easily, fast, or unconsciously change, typically. Examples are biometrics (recognition of a fingerprint, face, iris, and so on)
In simple authentication schemes, we use a single resource of a single factor to grant access to a user. However, in more sophisticated schemes, we can employ multiple resources of different factors to authenticate a user.
3. Sophisticated Authentication Schemes
As stated in the previous section, we can use multiple resources and several factors to authenticate a user to improve the security level of a system. These sophisticated schemes are called multi-step and multi-factor authentication.
3.1. Multi-step Authentication
A multi-step authentication scheme considers using different resources of the same authentication factor to allow a user to access systems or information.
In short, we can understand multi-step authentication as an additive process. First, we provide an authentication resource of a given factor, such as a fingerprint scan. So, if the first authentication succeeds, we must enter with another authentication resource of the same factor, such as a face or iris scan.
Another example of multi-step authentication is the two-passwords scheme adopted by some banks worldwide to execute online operations. In this case, we first have a long and more complex password to access the online system of a bank.
Moreover, besides the long password, the bank also provides a short and numerical password to confirm each operation executed by the user in the system.
The following image depicts the two-passwords multi-step authentication previously described:
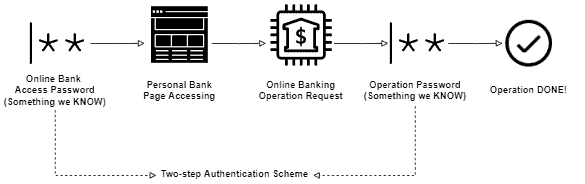
Finally, we can add authentication resources of the same factor as necessary. So, if we employ two authentication resources, we have a two-step authentication. With three authentication resources, we have a three-step authentication, and so on.
3.2. Multi-factor Authentication
As multi-step authentication, multi-factor authentication also uses multiple resources to check if the user identification is valid. However, in this case, these resources belong to different authentication factors.
It means that multi-factor authentication mix things. For example, we’ll need something we have and something we know to access a determined system.
Thus, we can see multi-factor authentication as a multiplicative process. Here, we are not actually providing multiple independent resources but different resources that derive a single credential.
Multi-factor authentication is a good practice in the digital security world. Sometimes we use multi-factor authentication so naturally that we neither notice it.
For example, to withdraw money from an ATM, we typically need our bank card (something we have). But, our bank password (something we know) is also required to finish the withdrawal process. Moreover, particular ATMs also demand a digital scan to allow the user to get the money (something we are).
The image next presents the multi-factor authentication previously exemplified:

In multi-factor authentication, we can add many factors as necessary. The classical authentication factors are three (as presented in Section 2). Thus, only considering them, we can have a two-factor authentication scheme or a three-factor authentication scheme.
3.3. Multi-step and Multi-factor Authentication
Until now, we can create authentication schemes with multiple resources of the same factor (multi-step) or single resources of different factors (multi-factor). However, we can also merge multi-step and multi-factor schemes with no problem.
It means that at least one factor employed in our schemes demands more than one authentication resource. This scenario defines a multi-step and multi-factor authentication scheme.
For example, specific banks provide a portable card reader to enable clients to read their cards and access their accounts in an online system. But, these banks typically still employ a double password scheme, with an access complex password and an operation numeric password.
In the described case, we have a total of two factors, one with one step and the other with two steps: something we have (the card) and something we know (the access and operation passwords).
4. Systematic Summary
As the computing power and the number of attacks and exploits increases in the digital world, more refined authentication schemes are required to grant access to sensitive data and operations.
Multi-step and multi-factor authentication are alternatives to achieve these sophisticated schemes. However, although both concern authentication resources, they aren’t the same.
Multi-step authentication considers having several resources of the same factor in a scheme. Multi-factor authentication, in turn, requires at least one step of two or more factors in an authentication scheme.
The following table compares multi-step and multi-factor authentication through relevant features:
At last, we can have many steps of different factors in a single authentication scheme with no problem. In such a case, this scheme is both multi-step and multi-factor.
5. Conclusion
In this tutorial, we studied multi-step and multi-factor authentication schemes. First, we had a brief review of authentication. Thus, we focused on understanding multi-step and multi-factor authentication. We also observed that multi-step and multi-factor authentication could work together in a single scheme. Finally, we systematically summarized and compared concepts.
We could notice that multi-step and multi-factor authentication schemes improve the security of a computer system in comparison to simpler schemes (with one factor and one step).
Thus, the higher the number of steps and the more the variety of the resources, the less susceptible and exploitable is an authentication scheme.