Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Public DMZ Network Architecture
Last updated: March 18, 2024
1. Introduction
In our everyday life, we provide different levels of protection for our properties. For instance, let’s consider an office room with a safe box. We can leave less relevant documents on the office’s desk and only lock the door when leaving the room.
The previously described documents will be protected by a physical barrier (the door). However, typically, many people have the keys to your office’s door for many reasons. So, these people can access the documents left on your desk.
In this way, top-secret documents require an extra security layer. This new layer aims to restrict the access of particular documents to a specific group of people. Thus, we can employ the safe box to keep these documents, only disclosing the safe’s combination to authorized people.
The presented scenario is an intuitive analogy of how a Demilitarized Zone (DMZ) works in current networks. In short, a DMZ is a perimeter network that divides an organization’s public and private networks.
In this tutorial, we’ll study the characteristics and architectures of DMZ networks. At first, we’ll explore what exactly a DMZ is and how it works. So, we’ll investigate the implementation architectures of a DMZ. Finally, we’ll discuss the benefits of implementing a DMZ.
2. Demilitarized Zone in a Nutshell
Demilitarized zones, sometimes called perimeter networks or screened subnetworks, create layers to divide public networks from the private networks of organizations.
The main objective of a DMZ is to enable an organization to access untrusted networks, such as the Internet, securely. In such a manner, a DMZ isolates internal and private networks from untrusted networks, avoiding unauthorized access to the first ones.
We can cite firewalls as one of the most relevant resources for implementing a DMZ.
In general, we use firewalls to isolate the public Internet from the DMZ and the DMZ from the private network. The rules enforced by these firewalls are typically different according to the isolated system’s segments.
Although firewalls are the core function of a DMZ, we can also employ other functions to improve the security and isolation of the systems. Examples of these functions are Intrusion Detection and Prevention Systems (IPS and IDS), antiviruses, and load balancers, among others.
We can analyze a DMZ concerning about two properties:
- Security Domains: networked security domains refer to dividing a networked system into segments isolated from each other. The access to different system segments is controlled and trackable.
- Defense in Depth: we should have multiple security solutions to defend a secured network domain. Thus, if a particular security solution fails, others can avoid attacks.
Considering a DMZ, we can classify the Internet as an untrusted domain, the demilitarized zone as semi-trusted, and the private network as trusted. So, the more reliability we demand from a system segment, the higher the number of security solutions we should use.
The following image exemplifies the previously presented concepts:
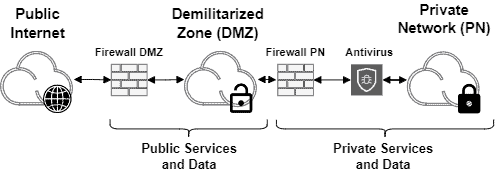
3. Demilitarized Zone Architectures
The basic about demilitarized zones is that they intermediate the public Internet and a private network. Furthermore, firewalls control the network traffic incoming and outgoing the system.
Considering the basic definition of a DMZ, there are two main architectures to implement it in the real world: double-firewalled and single-firewalled architectures.
The double-firewalled architecture is the most traditional one. In such a case, we have a firewall instance deployed between the public Internet and the DMZ. Moreover, we have a firewall instance deployed between the DMZ and the private network. These firewalls work independently.
The following image depicts a simple double-firewalled DMZ:
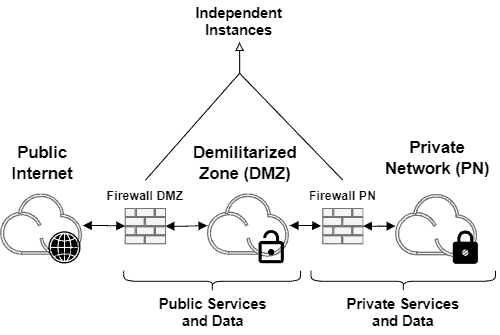
Although the double-firewalled architecture represents the most classic and didactic DMZ, the single-firewalled architecture is often implemented. It occurs due to the cost reduction of deploying and maintaining a single firewall instance instead of two.
The following image exemplifies a single-firewalled DMZ:
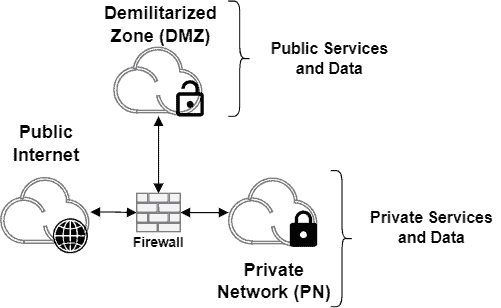
Operationally, the single-firewalled architecture is equivalent to the double-firewalled architecture. Of course, there are differences in the configuration of the firewall instances in these architectures, but it is not the main difference.
Actually, the main difference is that, in the single-firewalled architecture, the firewall is a single point of failure. In such a way, attackers can focus malicious actions on the firewall to unprotect both the DMZ and the private network.
Furthermore, as a single firewall tackles many rules, it can become a bottleneck faster than when we have two firewalls working in different network segments.
Adopting a single-firewall or double-firewall architecture should consider a cost/risk tradeoff. Moreover, it is relevant to ponderate the capacity to maintain the firewalls updated and configured with the proper set of rules: a single well-configured firewall may be better than two bad configured ones.
4. Benefits of Demilitarized Zones
Without a doubt, the main benefit of implementing a DMZ consists of setting an extra security layer between public and private networks. However, in addition to this principal benefit, we can analyze other ones that make implementing a DMZ a very promising idea:
- Network Access Control: in a DMZ, it is possible to limit and track access to organizations’ public and private networks. Besides being a security feature, tracking access to organizations’ systems may be strategic in terms of accountability
- Network Scanning Avoidance: attackers may be interested in scanning an organization’s network to find potential vulnerabilities and exploits. A well-projected DMZ discloses systems projected to be public, avoiding the scanning of systems designed only for internal use
- Performance Improvements: usually, public services are accessed by many users, but the traffic of these accesses may interfere with systems designed for private use only. A DMZ can reduce the load on the private network, improving the performance of systems running there
5. Conclusion
In this tutorial, we studied the technical details and implementation architectures of demilitarized zones. First, we reviewed the purposes of a DMZ and its most relevant operational characteristics. Thus, we investigated some popular architectures to implement a DMZ. Finally, we explored the specific benefits of setting up a DMZ in the context of organizations’ networks.
We can conclude that well-designed demilitarized zones can improve the security and arrangement of organizations’ networks by segmenting them into multiple layers.
Different policies can secure particular services and data by creating public and private layers in the organizations’ networks. These policies may include, for example, submitting the network traffic to several security network functions and requiring user credentials to access resources.