1. Introduction
Networking is communication. Computer networks enable human beings to fastly and efficiently communicate with each other around the world. In particular, the Internet consists of a global network that makes all this world-around communication concrete.
But, we can organize and design networks to not necessarily rely on the Internet to exchange data using a private environment. Examples of such cases are the intranet and the extranet.
In this tutorial, we’ll study the Internet, intranet, and extranet, thus understanding how they relate to each other. Initially, we’ll briefly review some concepts of networking. So, we’ll specifically study the Internet, intranet, and extranet. Finally, we’ll compare these categories of networks in a systematic summary.
2. Networking
In a computing context, networking means, in short, data exchange between any computing device. Naturally, which enables the computing devices to exchange data is the computer networks. However, these networks are not a simple structure. Actually, we have multiple categories and types of networks, each adapted for specific needs and purposes.
For example, we can categorize a network according to the connection topology of the devices on it. Usual and widely employed topologies in such a case are bus, ring, star, and mesh, among others. Furthermore, large networks can interconnect different topologies, creating a hybrid topology network.
Moreover, we can analyze the networks in terms of their physical infrastructure (underlay network) or logical connections (overlay network). Still, we can categorize the underlay networks according to the use or not of physical and virtualized (NFV– and SDN-based) components.
Among the presented and many other categories we can use to evaluate networks, we have some of them to explain how expansive access to a network is. In this scenario, the most know categories of networks are the Internet, intranet, and extranet. These categories, in turn, imply different security requirements and access restrictions.
In the following sections, we’ll particularly explore the characteristics of the Intenet, intranets, and extranets.
3. The Internet
When we talk about the Internet, we talk about a global network. The Internet consists of a large number of devices (in particular, computers) exchanging data around the world. This data is steered through cables and wireless mediums to reach its destination.
Furthermore, the Internet contemplates miscellaneous content accessible to every connected person. It means, in practice, that the Internet is public, everyone with the proper equipment can access this worldwide network, and it has no specific owner.
Due to the previously presented characteristics, there are no hard policies to navigate on the Internet: the user can go anywhere, anytime. Of course, there are some restricted access areas, but they are few compared to the number of free access areas.
We can consider all this freedom on the Internet generally good. Indeed it is, but it also brings lots of challenges.
In terms of security, the Internet does not implement a general security system. In such a way, the users and providers must guarantee their own protection by employing, for example, encrypted communications, firewalls, and antiviruses.
Other potential challenges regarding the Internet are the big competition to work there and the online impersonalization phenomenon.
4. The Intranet
The intranet, like the Internet, consists of a network that connects multiple devices enabling them to communicate and exchange data. However, unlike the Internet, the intranet is much smaller and works only for a particular company or organization.
So, we can see the intranet as a private network tailored to enable a small group to communicate, such as the employees of an organization.
Since we have a predefined group of users and a delimited accessing area, the maintainers of an intranet can enforce several security policies and solutions on that. Among the most common security resources are authentication mechanisms and native firewalls. Furthermore, a DMZ architecture may be employed to secure sensitive data from unauthorized access.
There are several benefits to adopting an intranet for an organization. The most relevant ones are related to making communication easy for the employees, which naturally enhances their productivity levels. Furthermore, an intranet becomes cost-effective in the medium term and makes the organization independent from third-party communication infrastructures.
However, there are some challenges regarding the intranet too.
One major challenge of the intranet consists of its implementation, which is commonly costly (in financial terms). Moreover, maintaining an intranet may be complex, requiring a particular and specialized team to do that.
5. The Extranet
Similar to the intranet, the extranet is a private and secure network. But, it connects multiple organizations (such as partners and suppliers) and even customers instead of only working internally in a single organization.
The central purpose of the extranet is to provide secure communication and enable efficient collaboration between trusted entities. It means that the extranet has no public access. Actually, we should identify and recognize everyone accessing the network or, at least, the company or location from where the access comes.
In addition to the communication objectives, the extranet also enables providing self-served services for customers. Thus, a customer can get the desired resource or execute a particular operation fastly and on demand.
In this way, we can cite as the main benefits of the extranet the high-secured data, the ease of implementation of business processes, and the flexibility to serve customers, increasing their overall satisfaction.
But, as for the other network categories considered in this tutorial, we have some drawbacks related to the extranet.
The main challenge of an extranet is implementing and maintaining it efficiently and cost-effectively. The extranet has similar objectives to the intranet but with a much broader scope. Due to that, the extranet is hard and expensive to organize and keep working satisfactorily.
Similarly, the security management of an extranet is much more complex when compared to an intranet: the more users we have on it, the more challenging to keep credentials and sensitive data protected.
6. Systematic Summary
Modern networks can be classified into multiple categories considering different theoretical and practical aspects. A relevant categorization approaches how expansive a network is regarding its scope of work: the Internet, intranet, and extranet.
The Internet is a public network with soft access policies. In summary, everyone can access and navigate the Internet. The intranet, however, typically works for a particular company or organization, accessed only for internal communication and data exchange. Finally, the extranet is an extension of the intranet to communicate with business partners, customers, and other trusted entities by a particular organization.
In this way, we can see the intranet as the most restrictive network category among the studied ones, while the Internet is the less restrictive and more generic one. The following figure depicts the relation between the explored network categories:
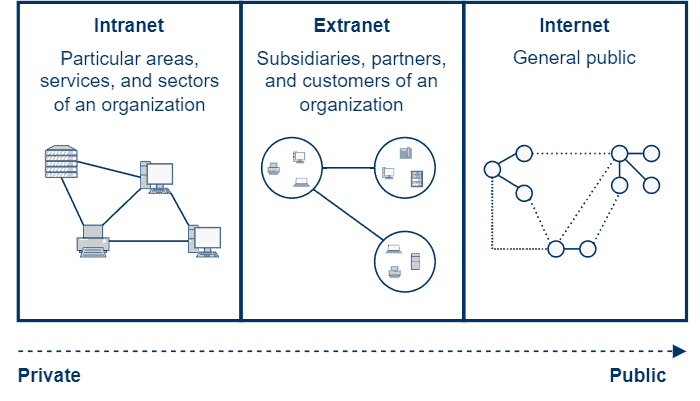
Furthermore, the table next compares some important concepts about the Internet, intranet, and extranet:
7. Conclusion
In this tutorial, we investigated the Internet, intranet, and extranet. Initially, we took a brief look into some background concepts on networking. Thus, we studied the Internet, intranet, and extranet, observing their characteristics, advantages, and disadvantages. Finally, we compared such network categories in a systematic summary.
We can conclude that working with multiple categories related to the action scope of networks is beneficial to organize the communication and data exchange between organizations and companies. Through these categories, network managers and operators can properly define policies and security mechanisms, avoiding applying too restrictive rules to public networks but securing sensitive data and limited access operations in private networks.