Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll study the Network Function Virtualization (NFV) paradigm. We probably already noted that the Internet has become relevant in everyday life, with many essential services being provided online.
The core network is the underlying infrastructure that supports the Internet. In there, several appliances work to enable connections and data exchange. These appliances, however, are typically implemented in hardware. So, the main proposal of the NFV paradigm is to migrate core network appliances from a hardware plane to a software plane.
In the following section, we’ll examine the main motivations, benefits, and challenges of migrating the networks from a hardware-based plane to a software plane. So, we’ll discuss some architectural and technical aspects of the NFV paradigm. Finally, we’ll summarize the NFV concepts and present final remarks.
Nowadays, most computer networks, from particular ones to the Internet itself, rely on appliances implemented in dedicated hardware to work. These appliances run different network functions, for instance, routing, load balancing, filtering, etc.
Of course, implementing the core network with hardware-based appliances has advantages. Most of these advantages are related to the high performance of networking traffic processing.
However, hardware-based core networks are hard to manage and update. For example, operators must do migration and placement processes physically, thus moving lots of equipment to create a new point of presence.
Furthermore, updating and upgrading the appliances might mean replacing a functional hardware piece. But, hardware-based appliances and their pieces typically have high monetary costs. Thus, it is not unusual for providers to keep deprecated network functions running in the core network.
The described scenario enables us to conclude that a hardware-based core network presents high Capital and Operational Expenditures (CAPEX/OPEX). Moreover, in addition to the costs, it also contributes to a process known as the ”Ossification of the Internet”.
The Network Function Virtualization paradigm emerges in this context proposing alternatives that solve the previously described problems. In the following subsection, we’ll see how this paradigm is willing to do that.
The primary objective of the NFV paradigm is to deploy and execute network functions commonly implemented in hardware-based appliances into a software plane.
To do that, NFV can employ several different virtualization technologies. Examples of such technologies are full virtualization, para-virtualization, containerization, and process-based virtualization.
So, multiple virtual elements can work in single commodity hardware providing network functions and other network core-related services.
Of course, migrating from a hardware-based appliances model to software-based network functions brings multiple challenges. The most prominent is dealing with performance drops caused by using general-purpose equipment with many virtualization layers.
But, the research and industry communities have been proposing several solutions to the performance challenges regarding network traffic processing. For instance, we can highlight the network processing acceleration tools (Intel DPDK, netmap, among others).
One question, however, remains: why decouple network functions from their dedicated hardware?
The NFV paradigm aims to improve the network core manageability, flexibility, and mobility.
So, we will be able to create networks from scratch by using commodity hardware. Moreover, it will be possible to update/upgrade network functions without buying new hardware or even migrating them across domains by only exchanging virtual element images.
Finally, by achieving the previously cited objectives, NFV also expects to reduce the overall CAPEX and OPEX to maintain the core network.
Currently, in addition to the research community, two entities propose guidelines and standards for NFV: the European Telecommunications Standards Institute (ETSI) and the Internet Engineering Task Force (IETF).
In specific, the ETSI is responsible for proposing the NFV standard architecture. This architecture, in turn, contains three domains and multiple operating blocks, as depicted in the following image:
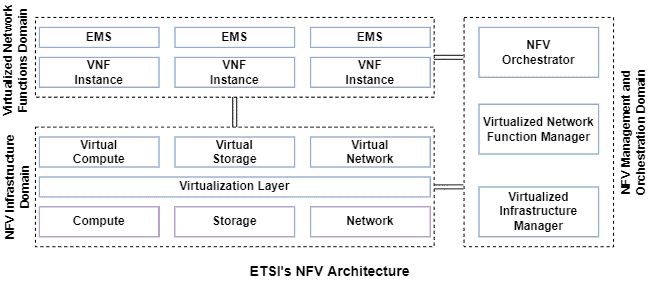
The first domain of the NFV architecture is called NFV Infrastructure (NFVI). So, this domain is responsible for managing the physical resources (such as memory, processing units, and network devices) and virtualization technologies, making them available for the other domains.
The second domain is called NFV Management and Orchestration (NFV MANO). This domain supports the virtualized infrastructure, manages network functions, as well as orchestrates network services.
Finally, the third domain is called Virtualized Network Functions (VNF). This domain handles the lifecycle and execution management of network functions.
In particular, we can highlight some relevant operational blocks of the previously stated domains:
As already shown, the ETSI’s NFV architecture has blocks dedicated to orchestrating and managing virtualized network services.
These services consist of multiple network functions logically organized in a topology, which we call a Service Function Chain (SFC). So, the network traffic goes through this topology, being processed by the network functions in a predefined order.
The following image exemplifies the topology of a simple security network service with a firewall, an IPS, and an antivirus:

It is relevant to highlight there exists an architecture to implement and execute virtualized network services. This architecture is proposed by the IETF and contains several elements.
Computer networks have become essential for modern societies. Several tasks regarding communication, commerce, and everyday living depend on computer networks to be accomplished.
However, the core network itself did not evolve as fast as the number of users using it. It happened due to a series of reasons. One important reason is the core network inflexibility and the high costs of updating and upgrading its appliances.
In such a way, the NFV paradigm emerged, proposing to decouple the network functions from their dedicated hardware, thus deploying them in a software plane enabled by virtualization technologies and commodity hardware.
Thus, in this tutorial, we studied this innovative paradigm. First, we investigated the current state of the core network and the potential problems related to it. So, we examined general concepts of the NFV paradigm. Finally, we saw the technical details of NFV, understanding how it allows the creation, execution, and management of network functions and services.
We can conclude that NFV represents a paradigm shift in telecommunications. There exist several challenges to be addressed until NFV gets popular in production networks. However, the flexibility and reduced capital and operational costs of NFV make it a promising alternative for the near future.