Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
Encryption has many uses in the computing world. Several of these uses are directly related to confidentiality. For example, we can encode files or secure network communications with different encrypting protocols. But, we can employ encryption for other purposes too. For instance, we can use it to guarantee the authenticity of digital data.
A common way to guarantee the authenticity of digital data is by signing it using the keys of asymmetric encryption methods. In such a scenario, the encryption resources needed are the same as providing confidentiality to the data. However, signing data requires using these resources differently.
In this tutorial, we’ll investigate the processes of encoding and signing digital data using asymmetric encryption methods. At first, we’ll have a brief review of encryption. Following, we’ll see how to encode data with asymmetric encryption. So, we’ll understand the signing process of digital data. Finally, we conclude the article with a systematic summary.
In the most usual way, we use encryption methods to guarantee the confidentiality of digital data. It means that we transform the original data (plain) into a code that covers the true meaning of the data (cipher).
There exist two main categories of encryption methods: symmetric and asymmetric.
The following image depicts the process of encoding and decoding data with asymmetric encryption method:
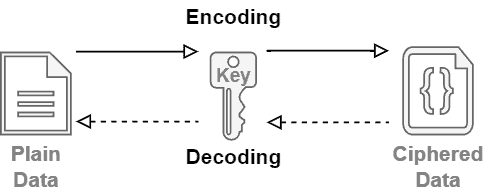
Symmetric encryption is at most simpler and lightweight compared to asymmetric encryption. However, asymmetric encryption is very versatile and has different applications, such as data encoding and signing.
In the following sections, we’ll in-depth explore, see examples, and compare asymmetric encryption applications.
In the computing world, the primary use of asymmetric encryption consists of encoding data, thus providing confidentiality. The asymmetric encryption methods employ a pair of keys: a public and private key.
When we encode data, typically, we aim that only specific entities have access to the original content. In the case of asymmetric encryption, encoding data with one key means that only the entities with the other key can decode it. In this way, we can use the open-access public key to encode data to be decoded only by the private key owners.
So, considering the described scenario, we can understand the public key as the encryption key while the private key is the decryption key.
The following image summarizes the data encoding and decoding processes with asymmetric encryption:
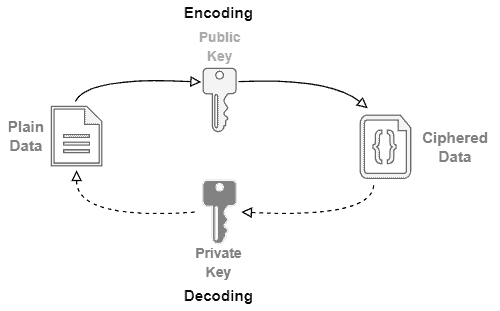
A great example of asymmetric cryptography use is the Transport Layer Security (TLS) protocol. This protocol enables clients and servers to negotiate keys to encode and decode network traffic. So, it is possible to keep the communication confidential between them.
Sealing APIs are another example. Sealing APIs provide a strategy to protect sensitive data and the private keys of a system. In short, it allows encoding data in connected environments with public keys. However, decoding data with private keys should be executed only in offline environments.
Another relevant application of asymmetric encryption is to sign digital data, providing authenticity. Similar to the encoding process, we also use public and private keys. However, in such a case, they are employed differently.
We previously studied that data encoded with a key is only decoded by the other key of the public/private pair. Thus, the public key is made available to everyone that wants to encode data, making it possible to communicate the owner of the private key confidentially.
However, the contrary is also valid. For example, if data is encrypted with the private key, only the public key will decode it.
To prove his identity, the owner of a private key encodes a signature, submitting it with the message. Thus, the receiver decodes the signature and checks if it corresponds to the expected signature for the received data. If the signature matches the expected, we can assume that the private key owner provided the received data.
The following image exemplifies the process of signing digital data with asymmetric encryption:
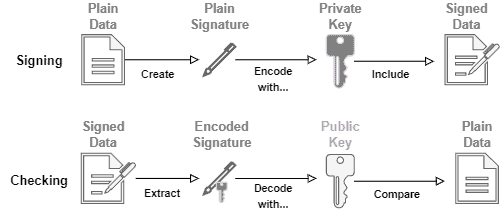
Regarding the plain signature, there are different ways to create it. However, signatures generally consist of hashing functions applied to the plain data. These functions generate hash codes posteriorly encoded with the private key.
The main benefit of using a hash code as a signature is that, besides authenticity, it is possible to guarantee certain levels of data integrity.
It means that the receiver can re-calculate the hash code with the plain data and compare it with the one received as the signature. If they do not match, two scenarios are possible: there was a spoofed signature (breach of authenticity), or there was corrupted data (breach of integrity).
In the previous sections, we studied asymmetric encryption in terms of providing confidentiality, authenticity, and integrity to digital data.
In summary, regardless of the objective for using asymmetric encryption, the same resources are necessary: a private and a public key. However, according to the objective of encryption, we must use these resources differently.
In such a way, the following table presents the main characteristics of encoding and signing digital data with asymmetric encryption.
| Encoding | Signing | |
|---|---|---|
| Encryption Target | The entire digital data | A hash code of the digital data |
| Encryption Key | Public | Private |
| Decryption Key | Private | Public |
| Main Objective | Confidentiality | Authenticity Integrity |
In this article, we learned about encoding and signing with asymmetric encryption. At first, we briefly reviewed encryption concepts in the context of computing. Thus, we in-depth studied the process of encoding digital data with asymmetric encryption. Similarly, we investigated the process of signing digital data using a pair of public and private encryption keys. Finally, we overviewed the presented concepts in a systematic summary.
Currently, we are massively adopting digital data to keep and transmit any information. However, on some occasions, digital data contains private or sensitive information. So, guaranteeing confidentiality, authenticity, and integrity became a significant concern. Thus, we can conclude that asymmetric encryption is a relevant resource in this computing world.