Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 14, 2024
Device hardening ensures strong network security by protecting against unauthorized access, hacking, malware infections, and other threats. Many components can be hardened, including servers, workstations, routers, switches, firewalls, smartphones, tablets, and connected devices.
In this tutorial, we’ll discuss why device hardening is important, its basic types, advantages, and difficulties, as well as recommendations.
There are multiple forms of device hardening:
Server hardening results in safeguarding the connections, information, rights, and functionalities of the server.
Furthermore, common server hardening techniques include using strong passwords, blocking users after a given number of unsuccessful attempts to log in, adopting multi-factor authentication, and restricting USB ports.
Here are the steps of server hardening:
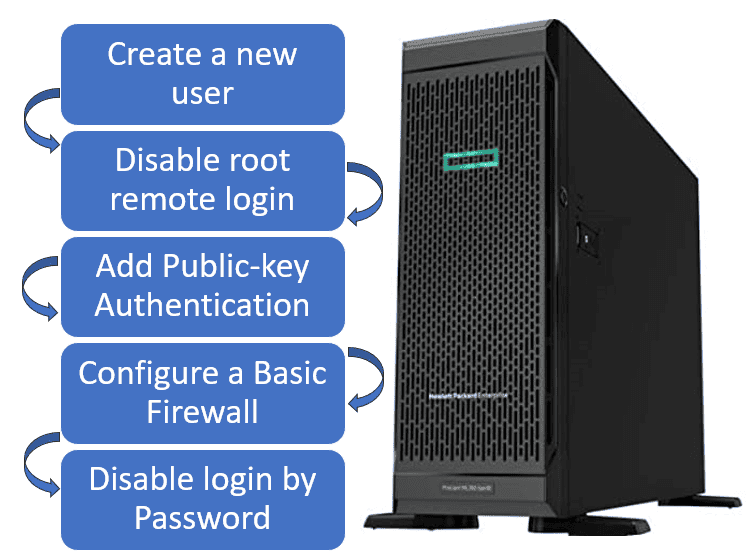
Creating a new user with root rights is to mislead a hacker. Hackers are often trying to get control via root credentials. To minimize vulnerabilities, root credentials should not be allowed for remote login.
Further, adding a public key authentication will enhance the server’s security by using a private SSH key to access it.
When a basic firewall is configured, we’ll only modify the rules for the standard ports that the interfaces use and create exclusions to the firewall for authorized applications.
Prevention of login by password is to secure the server from brute-force attacks by prohibiting login by password.
Application hardening entails safeguarding the programs installed on the device. Antivirus, adware, malware prevention solutions, and the establishment of systems to detect intrusions are all popular approaches.
The benefits of application hardening include binary-level code obfuscation and integrity validation to ensure that an application has not been tampered with.
Further, runtime application self-protection (RASP) hardening detects a compromised device and takes necessary action to protect an application.
The OS hardening supports safeguarding the OS:

Operating system hardening leads to protecting the device’s operating system. A few popular methods for safeguarding OSes involve limiting access, limiting user account creation, and removal of unused device drivers that expose a system to cyber threats.
Additionally, other methods include encrypting the storage device that hosts the OS and periodically implementing OS updates using service packs and security fixes. AppArmor and SELinux are commonly used to protect the operating system from buffer overflows and code injections.
Database hardening supports safeguarding the database:
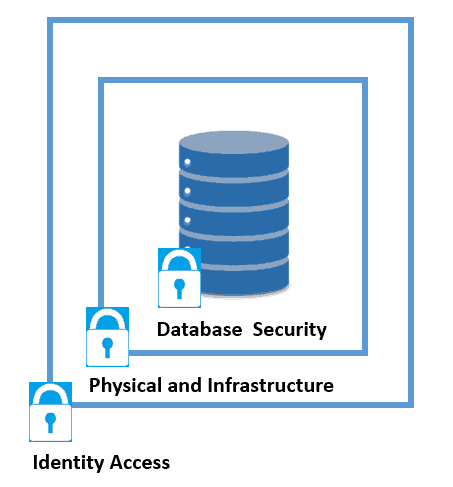
The first point of database hardening is identity access for regulating each user’s degree of access and rights. The next step is regulating access to the firewall and the server (physical and infrastructure).
Lastly, database security includes encrypting data, deleting unneeded functionalities, and auditing, and monitoring database activities.
Network hardening safeguards the connection used for interaction among endpoints. A method to create a secure network is to install a system that detects breaches in network communication.
The network is made up of elements that provide access to information and transfer. All of these elements need to be taken into account in network hardening:
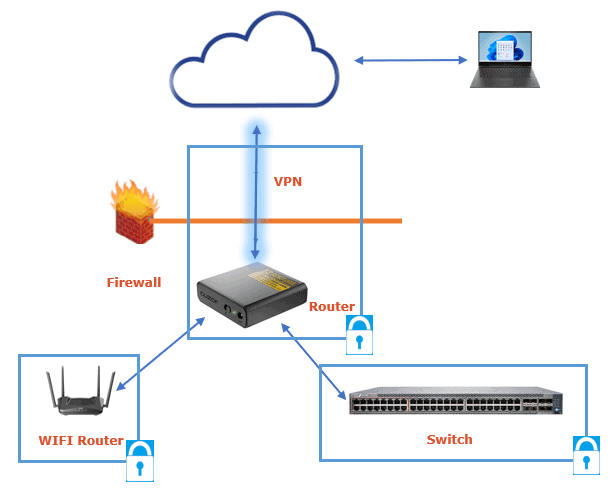
This system enables the early detection of potential attacks. Setting firewalls and securing internet traffic are ways to strengthen the network.
Network hardening tasks include implementing a role-based access control (RBAC) and setting up a router to permit only particular traffic from trusted applications.
Furthermore, this includes a VPN for remote connections, removing any insignificant permissions for remote sessions, and checking the logs for unexpected access and behavior.
To realize the benefits of device hardening, we suggest to adhere to the following process flow:
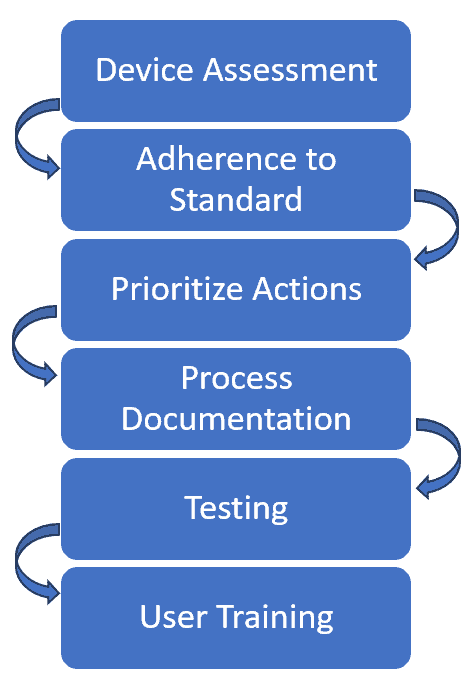
Let’s elaborate on the steps for device hardening.
When beginning the device hardening procedure, we must examine our device’s present status, setup, characteristics, capabilities, weaknesses, risks, and needs.
To conduct this evaluation, we can use a variety of tools or methodologies, including scans for vulnerabilities, penetration tests, and review audits.
We have to comply with recognized device hardening requirements and regulations which apply to a specific type of product and business.
These rules and regulations for device hardening are available from sources such as the Center for Internet Security(CIS) and ISO.
We must prioritize device activities based on the degree of seriousness and effect of the weaknesses and hazards that we have found during device assessment.
Most vital and critical problems are addressed initially, followed by those not as significant.
We must record the device’s hardening process and maintain a record of any modifications to it. Furthermore, every choice we make should be documented, including its reasons, upsides, and problems.
Proper documentation saves time and resources on employee education while also empowering them to operate optimally. Well-organized process documentation additionally makes it easier for organizations to use in the future.
However, efficient documentation requires meticulous planning to include as much information regarding the hardening method as feasible.
Correctly organized documentation not only illuminates the hardening process and its components but also provides a framework for comprehending the needed modifications for maximum efficiency. In this way, users can track, analyze, and optimize the hardening process of their devices.
We must check the device following each hardening activity to confirm that it is functioning correctly and safely. We should also test the device’s interoperability and operation with other gadgets or platforms with which it communicates.
Users may utilize various techniques or approaches to perform such testing, including performance evaluation, functionality testing, and security assessment.
We must train our users on the device hardening process, its advantages and disadvantages, and ways to use the equipment safely and productively.
We should also often contact users and seek their feedback and recommendations for improving the device’s hardening process.
Cyber threat prevention requires to safeguard a gadget’s vulnerability surface area. However, a device’s vulnerability points are its interfaces or services, protocols, and applications. Furthermore, even user accounts could pose a threat if not handled correctly.
The first step in fighting against hacking is to set a security surrounding the business systems that use physical and software techniques to deter an intruder.
The next step is to secure ports like USB from attacks by deleting or deactivating ports and restricting the number of machines’ access via external ports. Jump servers and proxy servers are ideal for this.
Lastly, by decoupling the endpoints from the company’s IT system, devices are no longer visible to the IT environment. Users can’t access the IT systems using their work systems credentials.
So, among other things, the device hardening framework establishes a robust defense to prevent intruders from conducting their attacks. It ensures that attacks are costly, time-consuming, and eventually futile.
Device hardening has numerous advantages to safeguard devices and data from cyber-attacks but also comes with some challenges:
| Benefits | Challenges |
|---|---|
| Lowers the likelihood of a cyberattack by removing the device’s weaknesses | Involves a lengthy and complicated procedure |
| Makes it easier to avoid data loss, theft, or modification by unauthorized persons | Requires technical expertise and an awareness of the numerous components of the device. |
| Increases the device’s efficiency through the elimination of superfluous or underutilized functionalities that lead to capacity waste or problems | Requires regular software upgrades and repairs to keep up with emerging dangers or modifications to the device |
| Optimizes the device’s performance, effectiveness, and dependability | May be hard to set up to work seamlessly with various other devices and system components |
| Minimizes the expenses of fixing or substituting malfunctioning devices, as well as retrieving lost data | It may also cause certain features or services to break or become unusable |
| Lowers the financial or regulatory costs that could result from data theft or infringement | Customers may be required to follow stringent rules or operations or employ extra authentication techniques, which can be difficult or annoying |
This framework keeps assets secure from unauthorized access and device flaws that could expose vulnerabilities.
It helps us update firmware and applications to the most recent versions, which include safety updates and bug fixes.
Next, it can turn off unwanted functions or services and analyze the device’s activities and records to identify or react to unusual threats.
What’s more, device hardening involves setting up safe credentials and information protection protocols, as well as installing antiviruses and firewalls to protect the device against networking and malware infections.
Lastly, device hardening helps to limit physical access to the device and its interfaces using keys, wires, or tamper-evident sealing.
However, hardening adds new technical requirements and requires expertise and resources for constant monitoring. It can also be a burden for users, who may be required to follow additional authentication steps and complex integrity protection rules.
Let’s now discuss an example. If we can connect to a server using SSH from any computer, everyone on the Internet can access it. Since the root account has full control, attempting to figure out or break the root user’s credentials is an ideal starting point for breaking into a server.
Hackers can constantly search for an open SSH connection and attempt to access the server using the root account and randomized credentials.
We can remove this by creating a user with less privileges and removing the root login:
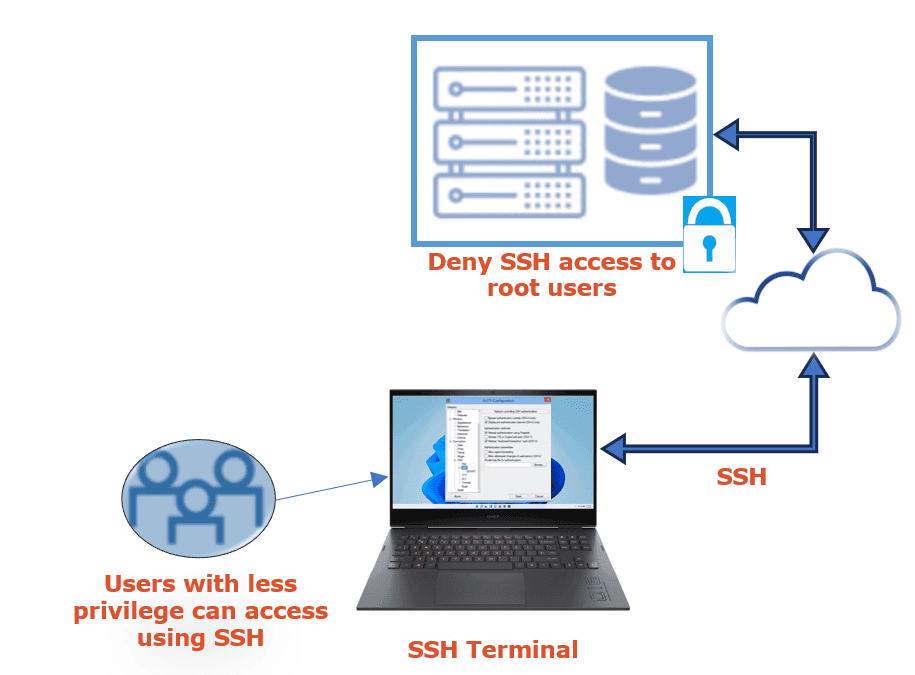
For this to work, the root username must be disabled on SSH. A common user can log in via SSH by using a less privileged user name.
Blocking SSH root login enhances safety and is a focus area whenever IT safety auditors examine safety concerns.
In this article, we discussed how to protect data and devices from cyber threats using device hardening. Further, device hardening protects many parts of the device, including connections, programs, services, operating systems, databases, and networking.
Device hardening has numerous advantages, including better safety, better efficiency, and low cost. However, it faces a few hurdles, including difficulty, reliability, and satisfaction.
We must adhere to a standard process for effective device hardening, prioritize actions, and educate device users about cyber threats.