Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll learn about Endpoint Detection and Response (EDR). We’ll begin by defining an endpoint and an EDR. Then, we’ll explain how an EDR works and present its main aspects. Next, we’ll discuss what features we should look for in an EDR tool and give examples. After that, we’ll explain why an EDR is crucial in our computing system. Finally, we’ll clarify the differences between antivirus, EDR, and XDR as security tools.
An endpoint is a computing device where data exchange goes back and forth within a network. The most typical examples of endpoints are laptops, desktops, servers, tablets, and smartphones. So, endpoints are devices on which we deploy the operating systems and software required to connect to the internet.
An endpoint presents a great technology that facilitates service exchange, data communication, and task achievement. Thus, they have a significant deficiency. They’re the most vulnerable and easy-to-access ports for attackers.
EDR, also known as Endpoint Threat Detection and Response (ETDR), is a cybersecurity solution implemented within endpoint devices to add a layer of advanced protection against cyber-attacks. As its name indicates, an EDR monitors an endpoint device to detect and respond to threats.
More specifically, it gathers information on processes and activities on the endpoint and analyzes them to identify regular-use and attack patterns. As a result, EDR can detect fileless malware and free-signature attacks that standard antiviruses can’t find. Such attacks include Advanced Persistent Threats (APT), zero-day exploits, or ransomware.
As a response, EDR can conduct several actions, such as thwarting threats, raising alerts, and isolating the device from the network to stop the attack from spreading. Its (automatic or manual) response ensures faster remediation from incidents and reduces their damaging effects.
EDR has four steps: collecting and analyzing data, detecting and responding to threats, forensics investigation and threat hunting, and integration and reporting services.
An EDR requires an agent to be installed on each endpoint. An agent is a software program that gathers data from the device, even when not connected to the internet. It will record all the system-level activities, such as running processes, transferring file transfers, and server connections.
This data is stored in a central database and analyzed in real-time to reveal basic patterns for normal behavior.
Based on the behavioral analysis of collected data and a large dataset of archived past attacks, EDR uses artificial intelligence (AI) to identify threats before they occur.
There are two types of threats: known and unknown. If it’s the first type, EDR captures a unique fingerprint of each malware with the help of the Indicator of Compromise (IoC) and uses it to filter malicious software trying to infiltrate the network and block them. In the case of an unknown threat, which has no trace of fingerprint, such as fileless attacks, EDR uses advanced algorithms.
EDR ensures a real-time and automatic response. Once a threat is detected, it alerts the security team and applies segmentation, if necessary, to stop the malicious file from spreading into the network.
After capturing relevant security information, an EDR tool investigates the successful attacks to understand how they work. It digs into the cause of an attack’s success, whether a device or a network’s vulnerability. Investigations ensure these attacks are detected and stopped in future occurrences.
Moreover, an EDR has what we call threat hunting. It’s a proactive process that constantly checks all the endpoints in the network, looking for a new threat or evidence of malicious behavior.
Threat hunting helps detect threats that bypass standard security mechanisms and enhance the EDR intelligence to mitigate evolving cyber-attacks.
The following figure depicts how an EDR system works:
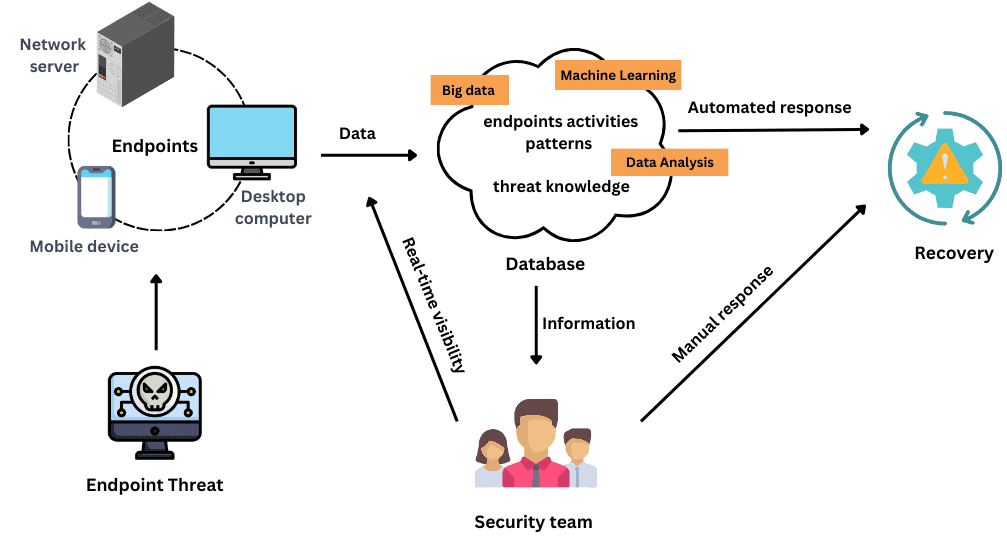
Last but not least, an EDR ensures integration. Namely, it provides all security information in one interface that facilitates the security team’s data management and decision-making. In addition, an EDR should be integrated with other security tools, such as Security Information Management (SIM) for threat detection and Security orchestration, automation, and response (SOAR) for threat response.
Furthermore, an EDR needs to report on the performance of the time spent to react to a threat and comply with regular security frameworks.
There are three main reasons why having an EDR solution is essential. First, the growing popularity of workplace mobility, where individuals can work from any place and on any device, increases the risk and vulnerability to attacks.
Second, the constantly increasing number of internet-connected devices requires a more efficient solution than the old security tools and can use historical knowledge and data from other devices to build in-depth defense mechanisms.
Finally, we can’t ignore the significant evolution of cyber-attacks. The hackers‘ tactics are becoming more complex and frequent. We need sophisticated tools and more advanced solutions to stay ahead of them.
When looking for an EDR tool, we must verify a set of features.
First, it should be resilient to attacks so that malware running on the operating system can’t perceive or access it. Second, it should use advanced AI to learn from past decisions and make future recommendations. Consequently, it will create more automated responses and alerts, easing the security team’s workload and allowing them to focus more on new and sophisticated threats.
Third, an EDR should have logging capabilities to optimize data and bandwidth usage, thus reducing the cost. Last but not least, it should provide a variety of deployment methods to increase flexibility and integration with the security infrastructure.
There are many EDR tools in the market. Examples are Cisco Advanced Malware Protection (AMP), Cynet 360, Bitdefender EDR, CrowdStrike Falcon Insight, and Cortex XDR.
An EDR provides security for devices and operating systems. However, it doesn’t replace the antivirus software.
Antivirus programs can block malware-based threats using signatures to identify them. Meanwhile, they fail to detect other types of threats that are unknown or don’t use signatures.
In contrast, an EDR is designed to detect and eliminate unknown, signature-free, and complex threats. Thus, EDR solutions complement antiviruses. Neither one of them replaces the other.
On the other hand, an Extended Detection and Response (XDR) has the same aspects and features as an EDR but supplies a larger layer of security covering an organization’s entire infrastructure. While an EDR focuses on endpoint security, an XDR includes endpoints, network security, and cloud-based systems.
In this article, we defined Endpoint Detection and Response technology and how it works. Moreover, we outlined the main aspects of an EDR and explained why it’s crucial to use this technology and what to look for when adopting it in our computing system.
To summarize, an EDR is a security solution for endpoint devices that provides detection of and recovery from attacks. It uses artificial intelligence and data analytics to give a real-time and fast response to security breaches. Its major features are threat hunting and forensics investigation that proactively search for threats before they damage the system.
Although it’s an upgraded technique for endpoint security, we should use it along with other tools, such as XDR and antiviruses, to ensure better protection against the ever-evolving cybercrimes.