Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: January 29, 2024
The remarkable transition to remote work and the evolving attacks in the cyber world increase hackers’ vulnerability to data and systems worldwide. To establish a thriving business in today’s digital world, it’s crucial to consider security and compliance. They represent two facets of risk management. Although they’re usually used together to secure data, they operate differently.
In this tutorial, we’ll define IT security and discuss businesses’ most common security methods. Then, we’ll define IT compliance and explain its major standards and the benefits they bring along. Last but not least, we’ll show similarities and differences between the two of them and conclude.
IT security defines a set of measures and technical tools implemented within organizations to protect their assets from cyber threats. IT security aims to develop a strong defense system that reduces the risk of cyber-attacks while maintaining the CIA triad of critical information.
Here, we can use several tools and measures to protect business data and IT infrastructure within our organization:
An organization requires a team of information security specialists to deploy the best tools and ensure consistent cyber-security awareness. We find a chief information security officer and an IT security department in this team.
The former builds and controls the company’s security architecture and manages the IT security department. The latter comprises security analysts and experts in charge of detecting, evaluating, and preventing threats in real-time. They also ensure that employees are kept updated on security measures.
Applying security measures provides a set of benefits for our business.
First, it ensures business continuity and productivity. In fact, up-to-date security controls allow companies to recover from security incidents quickly and avoid system disruptions, thus keeping their operations active. In addition, spreading cyber-security culture among employees helps them work with data efficiently.
Second, security measures enhance customer trust. When our company shows commitment to confidentiality and privacy of its customers’ personal information, it will gain a greater level of trust in the market and keep clients devoted to its brand.
Third, it prevents financial losses. We often expect data breaches to harm our business reputation, leading to losing sales and even paying penalties to customers with claims. That’s why IT security helps us save money in the long term.
To summarize, IT security concepts are depicted in the following figure:
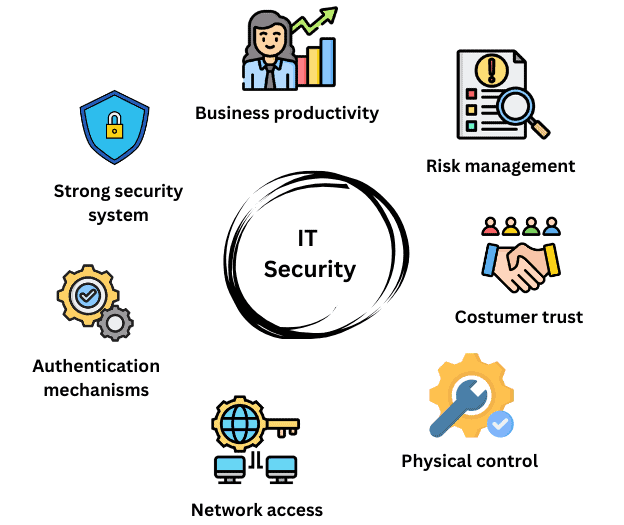
IT Compliance defines the process of fulfilling demands from third parties. It ensures a company adheres to industry norms and regulations when protecting sensitive data. IT compliance aims to reduce legal and financial risks while maintaining trust among partners and investors. Documenting procedures is essential in IT compliance and undergo regular audits by third parties.
IT compliance standards differ depending on the sector and geographical position. Let’s specify the most common among them:
Maintaining a compliance policy that conforms to laws and external standards is complex and requires a dedicated department. Typically, we need a chief compliance officer, a compliance department, and a chief technology officer.
First, the chief compliance officer directs the compliance department’s operations and keeps the organization’s executives updated on all compliance activities and issues.
Second, the compliance department consists of a team of compliance officers. They are in charge of setting and executing the compliance program, planning regular evaluations and audits, and organizing employee compliance training sessions.
Finally, the chief technology officer oversees every technical component and applied technology of used frameworks and infrastructure.
Adhering to compliance standards provides a set of benefits for businesses.
It helps avoid penalties and fines. Typically, violating laws and standards placed by a third party may result in serious fines and legal sanctions. Therefore, our company must adhere to IT compliance rules to avoid penalties.
Moreover, respecting compliance standards leads to establishing a positive brand reputation. IT compliance ensures that our organization respects ethics and handles customers’ information correctly. So, it helps us avoid public relations issues and gain customer and investor trust.
In addition, if our organization conforms to compliance standards, we can optimize our data management systems. Indeed, we can review our current data structures, rearrange our managing data process, and discard any accumulated information that’s no longer useful.
To summarize, IT compliance concepts are depicted in the following figure:
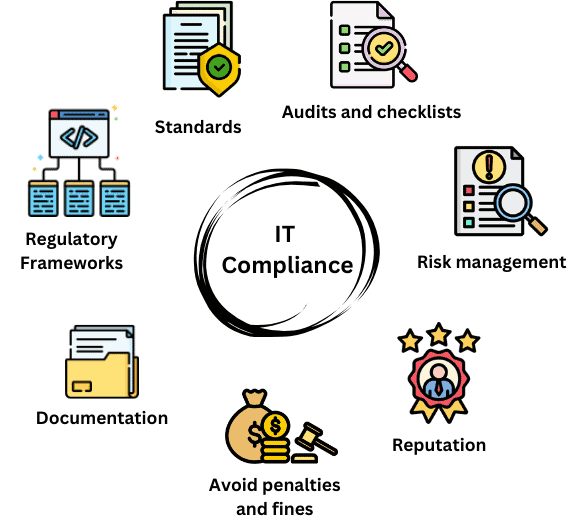
IT security and compliance are two processes that intersect in certain ways. In short, they’re both risk management tools that reduce the probability of data breaches and security incidents. Moreover, IT security and compliance are crucial to gaining customers’ trust and maintaining a positive reputation.
On the other hand, although IT security and compliance are frequently used simultaneously, they’re not the same and have different purposes and strategies. Here are the key differences between the two of them:
| IT Security | IT Compliance | |
|---|---|---|
| Defined as | implementing solid technological measures that safeguard business assets | adhering to third-party regulations that relate to information security |
| Aimed at | building a strong defense system against cyber threats | showing business conformity to standards and bypassing legal and financial sanctions |
| Driven by | technical motives | business motives |
| Requirements | are continuously changing | involve the minimum level of compliance |
| Implemented | proactively before an incident occurs to prevent it | reactively as a response to industry norms |
| Imposed by | internal initiatives and the organization’s commitment | external factors such as government laws, market standards, and contracts’ regulations |
| Focused on | processes, access, and security tools | documentation, audits, and policies |
| Causes | both financial and data losses | primarily financial losses |
In this article, we defined IT security and compliance and revealed major similarities and differences.
To conclude, IT security considers securing company assets, while IT compliance requires the satisfaction of third-party demands to avoid penalties. Although they differ in how they operate, they both aim to mitigate potential risks to information security and boost reputation in the industry.