Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Telnet vs. SSH
Last updated: March 18, 2024
1. Overview
In this tutorial, we’ll discuss two popular network protocols: Telnet and Secure Shell Protocol (SSH). Additionally, we’ll explore the advantages and disadvantages of both protocols.
Finally, we’ll highlight the core differences between them.
2. Telnet
2.1. Introduction
We utilize the Telnet protocol to establish a connection to a remote computer over a network. Additionally, we use it to access a command-line interface (CLI) on a remote computer, allowing the user to control and administer a computer remotely.
Furthermore, Telnet operates over TCP/IP. Moreover, it allows users to communicate with the remote computer by sending text-based commands and receiving text-based responses. Moreover, it can be used for various purposes, such as accessing remote servers, routers, and other network devices.
Let’s take a look at the typical architecture where we use Telnet to connect a client with the server:
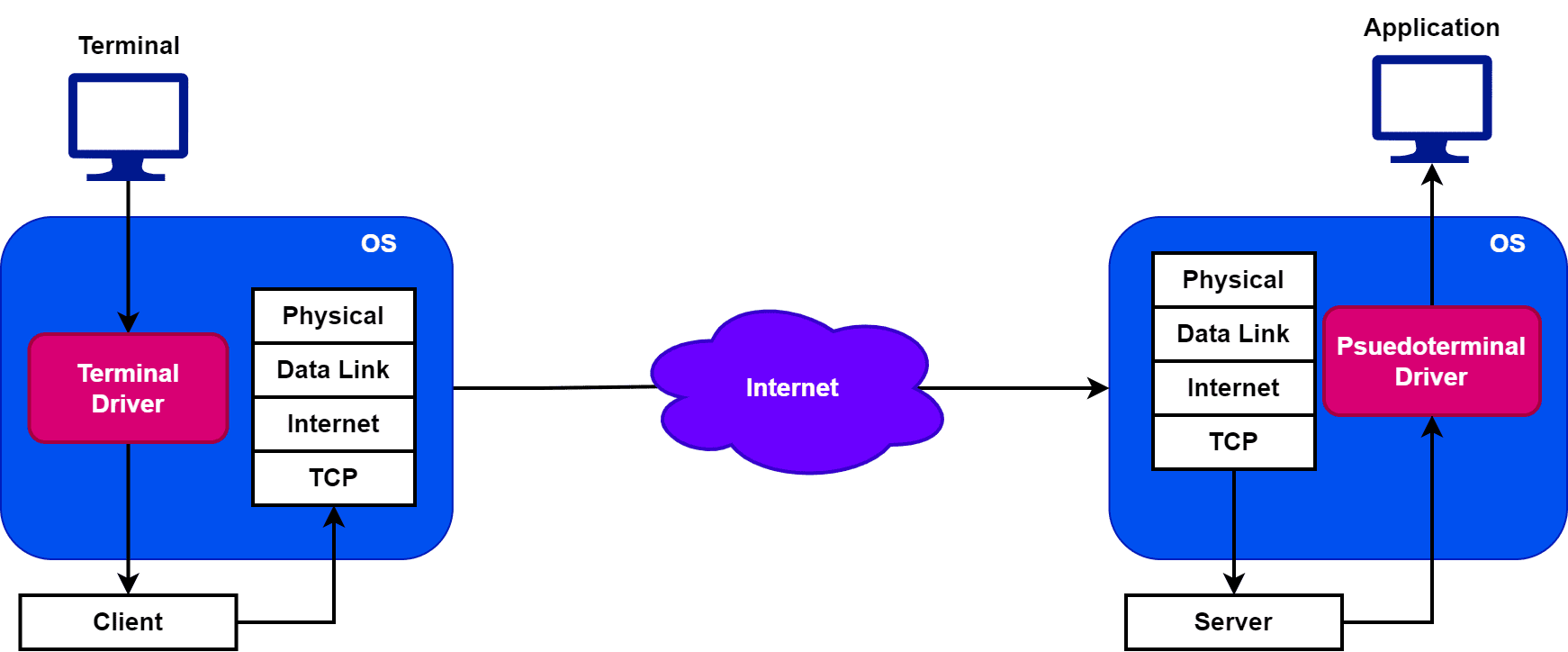
In order to use Telnet, we need two drivers: a terminal and a pseudoterminal driver. Therefore, a terminal driver is a software component that manages the input and output between a terminal and a remote computer. Furthermore, the pseudoterminal driver manages the communication between these two virtual terminals. Additionally, it allows the user to interact with the remote computer as if they’re using a local terminal.
However, Telnet has some security vulnerabilities. Moreover, it sends all information, including passwords and other sensitive data, in a cleartext format. Hence, the data we send using Telnet is susceptible to eavesdropping attacks. Due to security issues, it has largely been replaced by more secure protocols like Secure Shell (SSH) and virtual private networks (VPNs).
2.2. Application
Telnet has several applications, including remote administration and management of networking devices. Additionally, it enables users to access the command-line interface of remote computers and execute commands remotely. Therefore, it’s a valuable tool for system administrators and IT professionals.
Additionally, we can also use Telnet for remote debugging and troubleshooting. Hence, this feature is particularly useful for diagnosing and resolving issues on remote devices.
Moreover, Telnet is used for remote access to legacy applications and systems that don’t support modern network protocols. Despite its limitations in security, we still use it in some specialized applications and systems that don’t require high-level security, such as monitoring and control systems.
2.3. Advantages and Disadvantages
Let’s discuss some important advantages and disadvantages of Telnet:
| Advantages | Disadvantages |
|---|---|
| Enables remote administration and management of network devices | Can be used to bypass security measures and gain unauthorized access |
| Lightweight and easy to use | It’s vulnerable to attacks as there are no encryption or security features |
| Provides a standardized way to communicate with network devices | Limited support for graphics and multimedia |
| Supports scripting and automation of repetitive tasks | Performance can be affected by network latency and bandwidth limitations |
| Works across different operating systems and hardware platforms | Can be difficult to configure and set up in some network environments |
3. SSH
3.1. Introduction
SSH is a network protocol used to establish a secure and encrypted connection between two computers over a network. Additionally, it provides a secure and encrypted way to access and manage remote computers, similar to Telnet but with added security features.
Furthermore, SSH uses public-key cryptography to authenticate the remote computer and the users. Using authentication, we can ensure that the connection is secure and cannot be intercepted by unauthorized parties. Moreover, the encryption used in SSH makes it suitable for transmitting sensitive information such as login credentials, financial data, and other confidential information.
Let’s take a look at how an SSH client and an SSH server establish a connection:
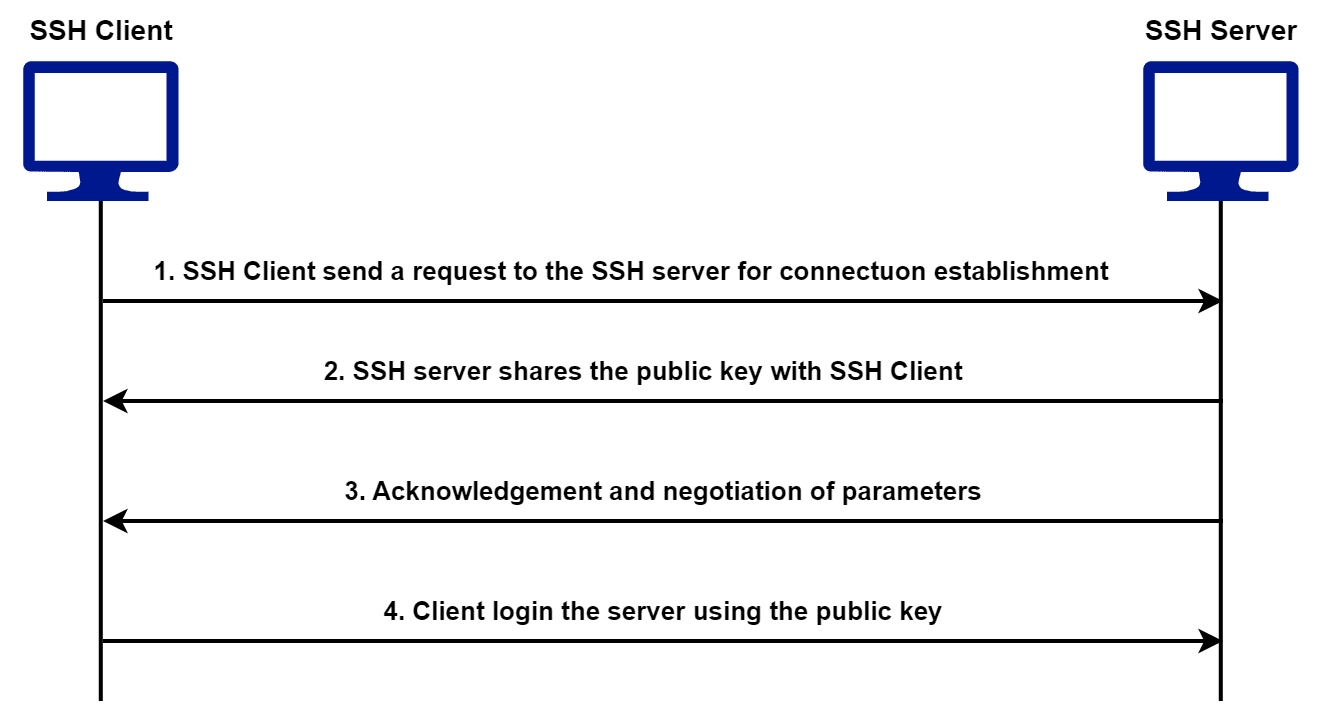
SSH is widely used in the administration and management of network devices. Furthermore, it’s considered a more secure alternative to Telnet and is commonly used in modern network environments.
3.2. Application
SSH has numerous applications in the field of computer networking and system administration. Furthermore, we primarily use it to secure remote access and manage networking devices.
Additionally, SSH provides an encrypted and secure way to access and manage remote computers. Hence, it’s essential for protecting sensitive information and preventing unauthorized access. Moreover, it’s used for secure file transfer, remote command execution, remote desktop access, and tunneling of other network protocols over an SSH connection.
Further, we can utilize it for backup of data, remote administration of databases, and secure access to cloud computing resources. Moreover, SSH can be used for remote collaboration and sharing of files between users.
3.3. Advantages and Disadvantages
Let’s discuss some important advantages and disadvantages of SSH:
| Advantages | Disadvantages |
|---|---|
| Provides secure and encrypted communication over a network | Can be more complex to configure and set up compared to Telnet |
| Suitable for transmitting sensitive information such as login credentials and financial data | Can be slower than unencrypted communication due to the overhead of encryption |
| Supports various encryption algorithms and key exchange protocols | May not be compatible with legacy systems |
| Enables remote collaboration and file sharing securely | Can be more expensive to implement than Telnet in large-scale networks |
| Offers strong authentication and access control mechanisms | Requires additional software or client to be installed on the remote computer |
4. Differences Between Telnet and SSH
Now let’s take a look at the core differences between Telnet and SSH:
| Telnet | SSH |
|---|---|
| Sends data in plain text, making it vulnerable to interception | Provides secure and encrypted communication over a network |
| Doesn’t have encryption or security features | Offers strong authentication and access control mechanisms |
| Provides remote access to a command-line interface | Provides remote access to a command-line interface, as well as remote desktop access |
| No support for user authentication or access control | Provides various encryption algorithms and key exchange protocols for secure authentication and access control |
| No support for file transfer operations | Supports secure file transfer protocols such as SFTP and SCP |
| Not widely used or supported in modern network environments | Widely used and supported in modern network environments for secure remote access and management |
5. Conclusion
In this tutorial, we discussed two popular network protocols: Telnet and Secure Shell Protocol (SSH). We explored the advantages and disadvantages of each protocol. Finally, we highlighted the core differences between them.