1. Introduction
Cryptography is the basis of security in our connected world. For example, we can hide some secret information or prove our identity with a satisfying confidence level with cryptography.
In specific, asymmetric cryptography methods are widely employed to protect or authenticate data on the Internet. These methods use pairs of keys (public and private) to encrypt and decrypt data.
However, getting the right public key to communicate with an exact private key is also a challenge. So, the certificates system arose with authorities linking a particular certificate (with a public key) to a specific source.
In this tutorial, we’ll study the frontiers between asymmetric cryptography and certificate systems. In this way, we’ll see how they relate to each other, besides the specific purposes of each one. First, we’ll have a very brief review of asymmetric cryptography and certificates. Thus, we’ll link both the concepts evidencing how they work with each other.
2. A Brief Review on Background Concepts
In this section, we’ll see basic concepts regarding asymmetric cryptography and certificate systems. So, the interpretation of these concepts will enable us to understand how they relate to each other in the next section.
2.1. Asymmetric Cryptography
In general, cryptography consists of strategies and methods to encrypt data, making it available only to authorized parties.
We can divide the cryptography methods into two families: symmetric and asymmetric. Summarily, symmetric methods use a single key to encrypt and decrypt data. Asymmetric methods, in turn, use a pair of keys: one to encrypt and another to decrypt data. Our focus is on asymmetric encryption.
As stated, in asymmetric encryption methods, we have a pair of keys. One of these keys we call public key, while another is the private key.
These keys have a strong relation: everything encrypted with the public key is decrypted only with the private key. Similarly, only the public key decrypts data encrypted with the private key.
As the name suggests, we open the public key to everyone. So, we can encrypt data with a public key making it readable only by the private key owner (secrecy). Furthermore, the owner of a private key can encrypt messages to prove its identity (authenticity).
The following image depicts the previously presented processes:
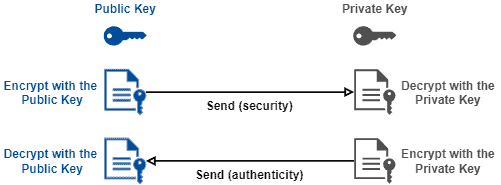
Asymmetric cryptography creates a solid base of security and authentication on the Internet. Currently, we have several protocols, such as SSL/TLS, SSH, and PGP, and encryption algorithms, such as RSA and ECC, that employ asymmetric encryption as the core for security and authentication.
2.2. Certificates
A certificate is a trusted document that contains a public key and other data of the respective private key owner. Examples of such data are the private key owner identification and the possible connections established with the private key owner.
The most relevant regarding certificates is that they are provided by a certificate authority. So, this authority is in charge of confirming the authenticity of a certificate owner. Thus, the authority must check if the pair of public/private keys belong to a particular person or company.
For sure, the certificate authority must be a trusted entity. So, we can take certificates and use them with no problems if we trust the authority that provides them. Otherwise, we will need to check the authenticity of the certificates with their owner before using them.
A usual file format used to create and provide certificates is CRT. CRT files contain ASCII data that follows the X.509 certification standard.
Other file formats also deal with certificates, such as PEM and PFX. However, these formats have specific purposes, besides carrying multiple different data together with certificates.
3. Relating Asymmetric Cryptography and Certificates
As we previously saw, certificates do not compete with asymmetric cryptography. Actually, they work together.
Asymmetric cryptography seems to be the most relevant technology nowadays to enable network users to communicate with security and guarantee the authenticity of the messages.
This relevance of asymmetric cryptography arises because we do not need to find a secure way to share the encryption key, as we have to for symmetric cryptography. It means that we can freely disclose the public key, keeping only the private key in secrecy.
However, disclosing the public key to anyone does not mean doing it anyway. We have to consider two relevant points:
- First, guarantee that we got the right public key to communicate with a particular entity
- Second, having the same file format with a standard set of data to provide public keys
And it is here where certificates emerge! In summary, certificates are files with a public key and a set of information of its respective private key owner. So, to guarantee correctness and authenticity, certificates are checked and made available by certificate authorities.
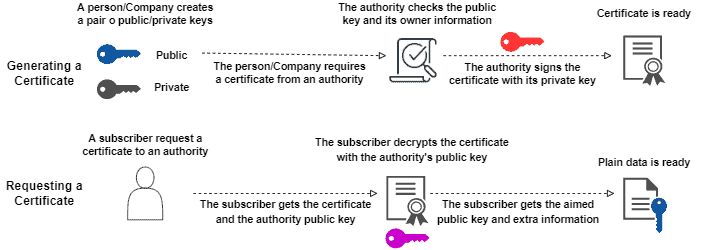
Of course, we need to trust the certificate authority that homologates a certificate. So, the trajectory of a certificate authority verifying certificates and homologating them with success to different people and organizations (called subscribers) typically enforces this trust.
To homologate a certificate, the certificate authority checks both the public key and the identity of a certificate owner. If the informed data matches reality, the certificate authority encrypts (signs) the certificate with its private key.
In this way, when a subscriber requests a certificate from the authority, he will get a signed certificate and the certificate authority public key. Thus, once the authority public key decrypts the file, the user will have the plain certificate of a person or organization.
The entire process described in this section is summarized in the following image:
4. Conclusion
In this tutorial, we learned about the relation between asymmetric cryptography and certificates. First, we had a brief review of asymmetric encoding and certificates. So, we in-depth explored how these concepts relate, highlighting every step of the creation and releasing process of certificates.
We can conclude that current certificates only exist due to the previous existence of asymmetric cryptography. The possibility of having a pair of keys to encrypt and decrypt data brings the necessity of proving that a given public key belongs to a particular person or company.
So, the certificates emerged to meet this demand, employing an effective process based on the trust of certificate authorities and in digital signing (also) with asymmetric cryptography.