Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll study firewalls. In particular, we focus on understanding the similarities and differences between stateless and stateful firewalls.
At first, we’ll have a brief review of firewalls, explaining their objectives and general operations. So, we’ll study stateless and stateful firewalls, paying attention to their specific features and operation capabilities. Finally, we’ll review and compare both firewall categories in a systematic summary.
As time passes and the Internet becomes popular everywhere, the greater the number of operations and services provided through a digital environment.
This scenario, in turn, imposes an increase in the number of value-added operations and sensitive data executed and exchanged through the networks. It naturally brings the attention of cybercriminals that aims to access these operations and data for illegal purposes.
So, protecting business and personal networks is an efficient way to keep private systems safe. One manner to control the network traffic incoming and outgoing our systems is by employing firewalls.
In short, firewalls are network functions tailored to inspect network traffic, deciding to forward or block it according to some criteria. In such a way, we can see firewalls as security network entities.
For example, some firewalls inspect packet headers, blocking the traffic of a particular set of IPs. Another example consists of firewalls that inspect packets’ payloads, looking for certain signatures to block traffic from a specific application.
With different forms to work, we consequently have several types of firewalls. Some of these firewall types are presented below.
Besides the previously presented firewall types, we have two relevant categories for them: stateless and stateful. In the following sections, we’ll see the characteristics of firewalls in these categories.
The principal characteristic of a stateless firewall is processing each received packet independently. It means that the firewall does not consider the results of previous processing of packets or connection details to act over a particular incoming or outgoing packet.
In summary, stateless firewalls process packets according to predefined rules commonly chosen by the network administrator. These rules never change due to the context of network traffic and connections. So, stateless firewalls apply them equally for all packets crossing the system.
It is relevant to highlight that since stateless firewalls are not connection-oriented, they have many more rules defined than stateful firewalls in general cases.
It occurs because stateless firewalls must define rules both for incoming and outgoing packets in a system, different from stateful firewalls (discussed in the next section), which can specify rules for connections.
The following image exemplifies the operation of a stateless firewall:
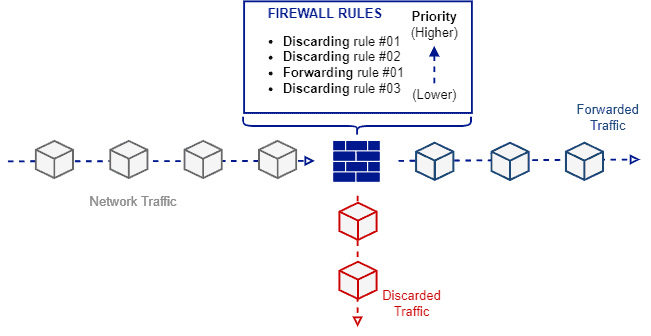
As shown in the previous image, the operation of a stateless firewall is quite simple. When a packet arrives at the firewall, it checks blocking and forwarding rules in a priority descend order. Thus, the firewall executes the corresponding action of the first rule matching the packet, ignoring any other lower priority rule.
Although simple network security solutions, stateless firewalls are still very relevant nowadays. For example, it is common to have stateless firewalls controlling the network traffic forwarded to other network functions, thus composing a network service chain.
Finally, as stateless firewalls only aim to match predefined patterns and rules for the incoming and outgoing packets, they typically are more performative (concerning throughput, for example) than stateful firewalls. So, when suitable, using them can avoid bottlenecks in the networks.
In several aspects, we can consider stateful firewalls as an evolution of the stateless firewalls since the last ones could not efficiently deal with modern threats, such as spoofed messages.
In such a way, stateful firewalls can monitor the multiple stages of a connection and its network traffic stream. So, a stateful firewall knows to which stream belongs a given packet incoming to the system and which is the state of the respective connection of this stream.
With the previously cited capability, stateful firewalls keep logical information of data exchanged in a stream and can avoid non-logical network traffic forwarding. Let’s see two common scenarios of non-logical traffic forwarding:
Since stateless firewalls do not keep information about the streams, connections, and their requests and responses, they are not able to deal with the scenarios described above.
For stateless firewalls, matching a forwarding or blocking rule is everything. Thus, if the malicious traffic matches a forwarding rule, it is forwarded regardless of being logically valid or not.
In stateful firewalls, in turn, logical forwarding is relevant. Thus, a stateful firewall keeps information to track connections. In such a way, it can identify if a given response corresponds to a previous valid request. Similarly, it can detect if a request comes from a logically-valid source.
The following image depicts the operation of stateful firewalls:
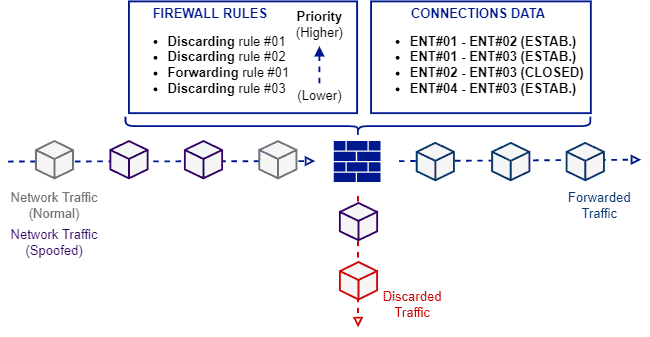
Securing a networked environment is an enormous challenge due to the diversity and complexity of existing attacks. So, using security solutions to avoid cyber threats has become a modern necessity.
Among these security solutions are firewalls. We have multiple types and categories of firewalls. A pretty relevant category of firewalls concerns how much information they keep about the incoming and outgoing network traffic and the established connections in a system.
In this context, we can categorize a firewall as stateless and stateful.
A stateless firewall does not keep data about the data streams and connections in the system. So, it evaluates each packet incoming/outgoing the system as a particular and independent element.
A stateful firewall, however, keeps the information about streams and connections, employing it to evaluate each packet. Thus, besides matching rules, stateful firewalls verify if the network traffic is logically consistent.
The following table compares some characteristics of stateless and stateful firewalls.
| Stateless Firewall | Stateful Firewall | |
|---|---|---|
| Rule-based Forward/Discard | Yes | Yes |
| Connection-based Forward/Discard | No | Yes |
| Robustness Against Spoofing Attacks | Low | High |
| Processing Performance | Typically, outperforms stateful firewalls in heavy traffic scenarios | Can become a bottleneck faster than a stateless firewall in heavy traffic scenarios |
| Purchase Price | Typically cheaper than stateful firewalls | Typically more expensive than stateless firewalls |
In this tutorial, we studied stateless and stateful firewalls. Initially, we reviewed firewalls, observing some relevant concepts and categorizations. Thus, we focused on understanding stateless and stateful firewalls. Finally, we compared these categories of firewalls in a systematic summary.
We can conclude that firewalls play a crucial role in cybersecurity. So, choosing the best firewall type and category is essential to get the best benefits from it in specific scenarios.