Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
With the continuous popularization of computing and networking, several services have migrated to the digital world. As a natural consequence, the processes executed and the data being transferred got value added. In this context, cybercriminals and malicious entities have been moving efforts to access these processes and data to get some benefit, typically financial ones.
However, attacks from these malicious entities typically present patterns that enable system managers and operators to prevent, identify and mitigate them.
In this tutorial, we’ll study the cyber kill chain framework to understand these patterns. First, we’ll investigate the origin of the kill chains. So, we’ll analyze each stage of this chain. Thus, we will explore how defensive tools can use the cyber kill chain to avoid and mitigate attacks. Finally, we’ll have some discussions and check the final remarks.
By origin, the term “kill chain” does not refer to the behavior pattern of any digital attack or threat. Actually, the kill chains were forged in the context of the US military. The main idea here is to define a standard series of stages to launch a military attack successfully. In such a case, the kill chain considers four particular stages, as depicted in the following figure:

The first stage is detection. In the military scenario, detection means identifying the target of an attack. For this purpose, we can employ different devices and techniques, such as radar scanning, satellite mapping, etc.
Delivering is the second stage. Deliver consists of preparing the area where the target locates with all the necessary resources. It usually includes sending men, weapons, and food to a strategic place.
The third stage is deciding. In this stage, the central action consists of choosing the best moment to actually order the attack. It involves evaluating the area and potential new events after the delivery stage.
Finally, we call the last stage killing. This stage is the execution of an attack aiming to suppress or eliminate the selected target.
The presented military kill chain was posteriorly adapted to consider cyber attacks, bringing the same planning logic to the digital world: the cyber kill chain.
The cyber kill chain is an adaption of the military kill chain that fits in a computing and networking context. Thus, different technological aspects are considered in each chain’s stages, aiming to provide a profile and design a standard model to identify, prevent, and mitigate cyber-attacks. So, we can consider the cyber kill chain a framework for cyber defense.
The cyber kill chain has seven stages: reconnaissance, weaponization, delivery, exploitation, installation, command and control, and actions on objectives. Each stage represents a particular goal of the attackers, and their execution follows a predefined order (the next stage in the chain relies on the success of the previous one).
The following image depicts the previously cited seven stages:
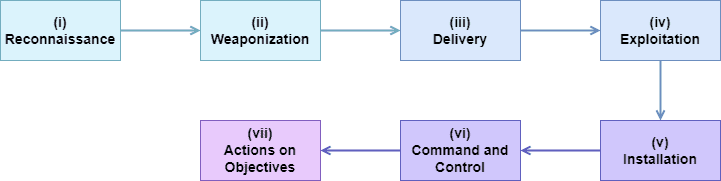
Let’s investigate the stages of the cyber kill chain.
The reconnaissance stage is the very starting point of any attack. At this point, the attacker chooses a specific victim or, broadly, a profile of the victims. The victim, in turn, could be from a person to a system.
So, during the reconnaissance stage, the attacker moves efforts to find potential vulnerabilities and weaknesses regarding its targets. These weaknesses may be in the victim’s hardware and software and other correlated systems employed by them (such as network functions and defense mechanisms — such as antiviruses and traffic analyzers).
In the weaponization stage, the attackers prepare the tools they will use during all the other stages. This stage considers the vulnerabilities and weaknesses found in the reconnaissance stage.
Examples of malicious tools typically used by attackers are viruses, worms, trojans, and ransomware.
After defining the malicious tools, the attacker must transmit them to the target victim. We call this process delivery.
So, in the delivering stage, the attacker must find the most prominent method to infect the victim. Some techniques to do that are phishing attacks, social engineering, and compromised web pages, among others.
With the malicious tools already in the target systems, the attacker may opt for one of two alternatives: activate or keep it idle.
So, the exploitation stage means the exact moment the attackers activate the malicious tools on the victims’ system, thus making them work on the previously detected vulnerabilities.
Thus, after getting access to the target system through its vulnerabilities, the malicious tools can work on modifying configurations, registers, and permission files. This stage calls installation.
The installation stage is broad in the sense that the modifications done in the system depend on the attackers’ purposes. In this scenario, we have as an example the setting up of a cryptographic algorithm for ransomware or the set up of a time bomb for triggering malicious actions in a predefined moment.
With all the required malicious software set up, the attacker can now take control of the target system. The concept behind the stage called command and control is actually executing processes to achieve the attacker’s objectives.
Sometimes, the attacker does not directly involve in the command and control stage since the installed malicious tools work automatically. Other times, however, the attacker directly accesses and manipulates the victims’ system through the previously installed tools.
The last stage of the cyber kill chain is called actions on objectives. This stage consists of the moment that the attacker achieves its objectives.
Again, the meaning of “achieving the objectives” will vary depending on the attacker’s purposes. Particular and usual objective examples are stealing, destroying, and encrypting data or making a service unavailable for legit users.
As we already commented, the seven stages of the cyber kill chain create a codependent sequence of events and operations that finally result in a successful malicious attack. So, each stage (except the first) requires the execution of the previous ones.
In this scenario, security protocols and systems have a strategic advantage. While a successful attack depends on accomplishing seven stages, a successful avoidance or mitigation depends on frustrating only one of these stages!
However, the earlier in the kill chain we stop the attack, the better. In short, we can say that the less access an attacker has to the target system, the smaller the damaging effects are.
So, at first, we should do the best project possible for our system, thus avoiding making it exploitable through some unseen vulnerability. In addition, we should also integrate security tools, such as firewalls and antiviruses, into our systems. Finally, we should protect sensitive data as much as possible, for example, by encrypting it.
In this tutorial, we studied the cyber kill chain. First, we analyzed the origin of the term kill chain. So, we investigated how this term was applied in the context of computing and networking attacks. At last, we examined how to break the cyber kill chain and avoid or mitigate a malicious attack.
We can conclude that executing an attack is complex and require the accomplishment of several tasks in multiple stages. Due to that, attackers get really prepared to get success in their efforts. In this way, the operators and administrators of benign systems must also take proactive actions to protect their systems and keep their services running as expected.