Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: June 10, 2023
In this tutorial, we’ll give a brief definition of encryption and why we need it in the first place. After that, we’ll compare some encryption algorithms, DES (Data Encryption Standard), 3DES (Triple DES), AES (Advanced Encryption Algorithm), and Blowfish in terms of some evaluation metrics.
Encryption is a technique for securing the information so only the authorized parties can interpret the data. What happens is that encryption provides transformations on the plaintext and transforms it into ciphertext which isn’t human-readable.
Not only in the digital era but ciphers have also been widely used throughout history. In the figure below, we present the general view of the classification of the ciphers. As we’ve seen, we categorize ciphers in terms of some characteristics that they have or according to their usage. They are mainly divided into two different types; classical and modern classes. The most common and used in digital are is modern class. It’s because of its dynamic and static cryptographic techniques that pave the way for more detailed classes, symmetric and asymmetric ciphers:
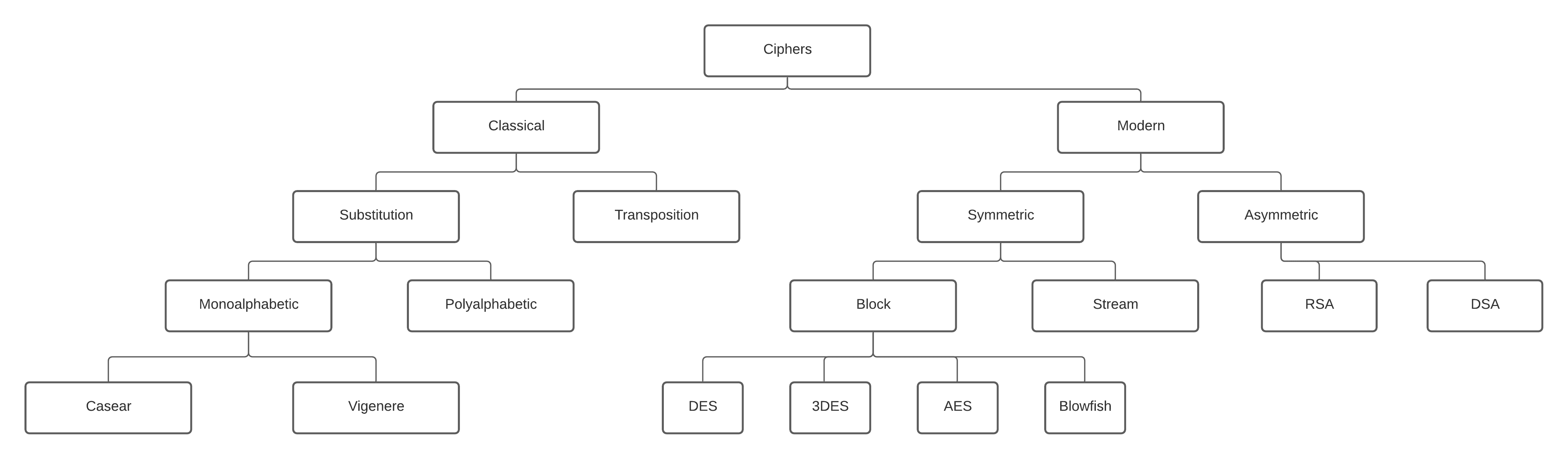
While in symmetric encryption we have only one key to encrypt and decrypt data, in asymmetric encryption, we use two different keys. We use a public key for the encryption and a private key for the decryption. Even though the public and private keys are different, they are related to each other so we call them a key pair. DES, 3DES, AES, and Blowfish are the members of the symmetric-key block cipher class and we’re going to describe them and compare them with each other throughout the article.
Let’s see each of these algorithms in detail.
DES is developed by IBM and based on a design by Horst Feistel. It was one of the widely used and publicly available cryptographic systems when it was first released. Even though its first debut is in the 70s, it was later adopted by the National Institute of Standards and Technology (NIST). It’s a symmetric-key algorithm for the encryption of digital data.
It has a block size of 64 bits and uses the Feistel network as a structure. It’s slow and not used in the software.
It had a high impact on the advancement of cryptography. However, it’s insecure for applications due to the short key length of 56 bits. In 1999, distributed.net break a DES key in 22 hours and 15 minutes. After these kinds of events, NIST withdraws this algorithm as a standard. 3DES emerged after the vulnerabilities in DES.
Triple DES, 3DES, or TDES is officially the Triple Data Encryption Algorithm. It’s a symmetric-key block cipher and it applies the DES algorithm three times to each block. It has a block size of 64 bits and a key length of 112 or 168 bits. It also uses the Feistel network since it’s based on DES.
Due to the modern cryptology techniques and supercomputing, like the DES, 3DES has also some serious vulnerabilities. That’s why the NIST has deprecated DES and 3DES for new applications in 2017 and for all applications by 2023.
As a result, AES came onto the stage and displaced these encryption algorithms.
Blowfish is another symmetric-key encryption technique designed by Bruce Schneier in 1993 as an alternative to the DES encryption algorithm. Therefore it is significantly faster than DES and provides a good encryption rate. Its key length is 446 bits, and way better than DES, and 3DES. Therefore, it’s more difficult to crack the key of Blowfish. It also has a block size of 64 bits. It can be used in software as well.
However, AES receives more attention today, and Schneier recommends Twofish as an alternative to Blowfish. It has a free license and is available for all uses.
AES is another type of cipher that protects the data from malicious parties. It’s currently one of the strongest encryption algorithms available. Since AES combines speed and security properly, it allows us to carry on with our online activities without any interruption.
As AES uses the same key to both encrypt and decrypt data, it is also a symmetric type of encryption. There are three types of lengths of AES encryption keys 128, 192, and 256 bits. Each key length has different possible key combinations. It has a different structure than other encryption algorithms, it uses the substitution-permutation network.
While the key length of the AES encryption method varies, its block size is fixed as 128-bits or 16 bytes.
As we discussed in earlier sections and as we can see in the table below, DES is not secure enough. It is because of its short key length and brute force attacks that can crack it easily. Therefore, although 3DES is another alternative, it’s not secure enough either:
| DES | 3DES | Blowfish | AES | |
|---|---|---|---|---|
| Key length | 56 bits | 112 or 168 bits | 448 bits | 128, 192, or 256 bits |
| Block Size | 64 bits | 64 bits | 64 bits | 128bits |
| Developed in | 1975 | 1978 | 1993 | 2000 |
| Speed | Slow | Slow | Fast | Fast |
| Security | Not secure enough | Not secure enough | Secure enough | Excellent security |
| Structure | Feistel | Feistel | Feistel | Substitution Permutation |
| Time required to check all possible keys at 50 billion keys per second | 400 days | 800 days | ~3200 days |
While Blowfish is one of the good alternatives, its block size is not sufficient as AES. We consider AES as the successor of DES as a symmetric key encryption algorithm for organizations. It accepts different key sizes, 128, 192, or 256 bits. It is efficient in both software and hardware.
We can see the efficiency of AES when we look at the time required to check all possible keys at 50 billion keys per second. Its results are way better than other encryption algorithms even if it uses key size as 128 bits.
In the literature, there are plenty of research studies that evaluate and compare some of the encryption algorithms. And in these studies, there are certain metrics that they usually focus on during comparison. Actually, these metrics mainly include encryption and decryption time, memory usage, and sometimes entropy, avalanche effect, and the number of bits required for encoding optimally.
It is the time it takes to convert plaintext to ciphertext. The length of the encryption process is determined by the key size, plaintext block size, and mode. In order for the system to be quick and responsive, encryption time should be less.
The time it takes to retrieve plaintext from the ciphertext. To make the system quick, it should be less like the encryption time.
Different encryption algorithms take varying amounts of RAM for implementation. Memory usage depends on the key size, type of operations, number of operations, and initialization vectors.
It is a desired characteristic of cryptographic algorithms. Block ciphers and cryptographic hash function in which if the input is slightly altered like flipping a single bit, the output changes considerably. Such a minor change in the key or plaintext must result in a significant change in ciphertext in high-quality block ciphers. While this phrase was coined by Horst Feistel, the notion stretches back to Shannon’s diffusion.
In this article, we’ve briefly given some information about DES, 3DES, Blowfish, and AES. Also, we compared and evaluated them in terms of some metrics.
Although we think that encryption algorithms protect the data both in theory and practice, keep in mind that there are various attacks such as malware, key search, brute force, phishing, side-channel, and more. These attacks aim to find a way to hack the system.
To sum up, while every encryption algorithm has weaknesses and advantages, some of them can lose their reliability over time. So, we should be careful when we select cryptographic algorithms. We should both consider our application and the specifics of the encryption algorithm.