1. Introduction
In the world of cybersecurity, a botnet refers to a network of compromised computers, also known as bots or zombies, that are under the control of a malicious actor. These bots can be infected with malware, allowing the attacker to control them remotely.
In this tutorial, we’ll delve into the botnets, exploring their operations, impact on individuals and organizations, and the measures taken to combat them effectively.
2. Botnets: an Overview
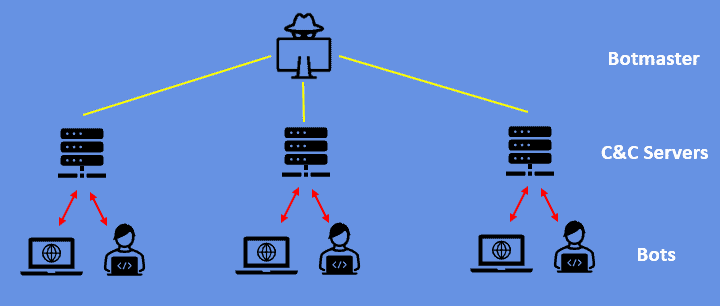
A botnet is a collection of infected computers, or bots, that are centrally controlled by an attacker known as the botmaster. Moreover, these bots can range from a few machines to thousands or even millions.
The compromised computers may include home PCs, servers, or Internet of Things (IoT) devices. In addition, the botmaster uses a Command-and-Control (C&C) infrastructure to manage and direct the bots’ activities:
2.1. Types of Botnets
We can classify botnets based on their purpose and functionality. Some common types of botnets include:
- DDoS Botnets: these botnets focus on launching distributed denial-of-service (DDoS) attacks. By coordinating a massive influx of traffic to a target system or network, they overwhelm its resources and render it inaccessible to legitimate users.
- Spam Botnets: spam botnets distribute vast volumes of unsolicited emails. Moreover, these emails typically contain advertisements, phishing attempts, or malware.
- Credential Theft Botnets: this type harvests sensitive information such as login credentials, credit card details, or personal data.
3. How Botnets Operate
3.1. Botnet Creation
Botnets can be created through various methods, including:
- Exploiting Vulnerabilities: attackers actively search for vulnerabilities in computer systems, software, or network protocols. Once they discover a vulnerability, they exploit it to gain unauthorized access and infect the compromised machine with botnet malware.
- Malicious Downloads: users can inadvertently download malware-infected files or software from malicious websites, file-sharing networks, or email attachments. Once executed, the malware takes control of the system and connects it to the botnet.
- Social Engineering: attackers often employ social engineering techniques to trick users into installing malware unknowingly.
3.2. Command and Control (C&C) Infrastructure
The C&C infrastructure consists of one or more servers under the control of the botmaster. Its server serves as the central hub for communication between the botmaster and the compromised bots.
It also issues commands to the bots, instructing them to perform specific actions, such as launching attacks, harvesting data, or downloading and executing additional malware. Furthermore, it collects information from the bots, such as stolen credentials or harvested data, for further exploitation.
3.3. Botnet Propagation
Once a botnet is created, it can propagate rapidly by infecting other vulnerable computers or bots. Botnet propagation methods include:
- Scanning for Vulnerabilities: bots scan the internet for computers with known vulnerabilities. Once identified, they exploit the vulnerabilities to gain unauthorized access and infect the target system with botnet malware.
- Exploiting Software Flaws: bots exploit vulnerabilities in software applications, operating systems, or network protocols to compromise target machines and expand the botnet
- Self-Replicating Worms: some botnets employ self-replicating worms that can autonomously spread and infect vulnerable computers without the need for direct human intervention
4. Combating Botnets
4.1. Detecting Botnet Activity
Detecting and mitigating botnet activity is crucial to minimize their impact. Various techniques and tools are employed to identify and analyze botnet-related activities. These include:
- Intrusion Detection Systems (IDS): IDS can detect and alert administrators about potential botnet traffic by analyzing network packets, identifying patterns, or recognizing known botnet signatures
- Network Traffic Analysis: by monitoring network traffic and analyzing its behaviour, anomalies and patterns indicative of botnet activity can be identified
- Behaviour-Based Anomaly Detection: Machine learning algorithms and anomaly detection techniques can analyze system behaviour to identify unusual activities associated with botnet infections
4.2. Disrupting Botnets
Law enforcement agencies, cybersecurity organizations, and industry collaborations carry out efforts to disrupt and dismantle botnets. These initiatives involve:
- Sinkholing: Sinkholing refers to redirecting the communication between the bots and the C&C server to a controlled server operated by cybersecurity experts. This technique allows researchers to gather information about the botnet’s infrastructure and potentially disable its operation.
- Botnet Takedowns: Law enforcement agencies and cybersecurity organizations work together to identify and take down C&C servers, cutting off the communication channels between the botmaster and the bots
- Collaboration with ISPs: Cooperation with internet service providers (ISPs) is essential in blocking malicious traffic associated with botnets and notifying affected customers to clean their infected systems
5. User Awareness and Best Practices
Promoting user awareness is crucial in combating botnets effectively. Some best practices include:
- Regular Software Updates: keeping operating systems, applications, and security software up to date helps protect against known vulnerabilities that botnets exploit
- Strong Passwords and Two-Factor Authentication: using strong, unique passwords and enabling two-factor authentication adds an extra layer of security to prevent unauthorized access to accounts
- Vigilance in Email and Web Browsing: users should exercise caution when opening email attachments, clicking on suspicious links, or visiting unfamiliar websites, as these can be entry points for botnet infections
6. Conclusion
In conclusion, a comprehensive understanding of botnets, robust security measures, user awareness campaigns, stakeholder collaboration, and proactive approaches are essential in mitigating botnet risks and fostering a safer digital environment.
