Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
Obscurity consists of hiding some resource to reduce the probability of being attacked or stoled. It is a frequent alternative to improve some security systems.
An example of obscurity in real life is camouflage. Armies use different types of camouflage to hide their soldiers in the environment, avoiding dangerous situations. Another example is transporting a VIP in a particular vehicle hidden among several identical vehicles.
In this tutorial, we’ll explore security by obscurity in the context of computing. First, we’ll have a brief introduction to different digital security systems. So, we’ll understand why using obscurity alone may be a bad idea. Finally, we’ll present some scenarios and benefits of applying obscurity with other security methods.
Digital security is a complex theme in Computer Science. We can identify several security layers employable to our systems and data. Furthermore, these security layers can vary according to the available technologies and objectives.
It is relevant to highlight that modern society relies on multiple digital equipment and systems. Some systems execute critical tasks, such as hospital programs, electric grids, and traffic lights. So, we must have robust and resilient security measures to avoid catastrophic scenarios and data leaks resulting from attacks.
In this way, let’s see some relevant examples of security categories:
We can note that, regardless of category, cryptography plays a crucial role in digital security. It is useful, for example, to keep sensitive data protected from being read by unauthorized entities and create passwords or signatures.
The concept of security by obscurity, in turn, comes from cryptography. Actually, it is typically seen as a bad practice in this field: it is not a good idea to base the security of a cryptography system on the secrecy of its algorithm.
However, can we benefit from security by obscurity in different contexts of security and computer science? So, let’s analyze security by obscurity in the following section, thus defining its strong and weak aspects and use scenarios.
Let’s think about security in a naive way first. Analogously, encrypting a digital file corresponds to keeping a concrete file in a safe box, locked with a key. Furthermore, an antivirus executing in the system with the encrypted file acts similarly to a policeman watching the place where the safe box is.
We can go even deeper with the comparisons: configuring a firewall in the digital system represents having another policeman checking IDs to grant people access to the place where the safe box is.
The previously assumed methods do not consider security by obscurity. In our case, employing security by obscurity consists of hiding the safe box with the file in a non-visible place of the local where it exists.
The following image depicts the scenario of our analogy:
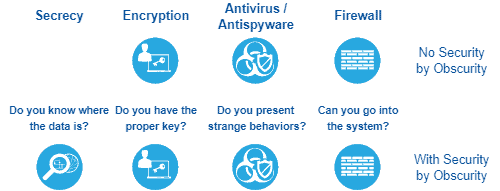
So, basically, we can define security by obscurity as the processes and methods to hide some data or system. In such a way, by design, the systems do not openly disclose some information. Only those who know where to search will find it.
An ordinary example of security by obscurity is using non-indexed links to share data on the Internet. Several storage cloud services, online text editors, and other web services enable the users to activate a shareable link.
Besides being non-indexed, a large random string usually forms a shareable link. This characteristic makes it hard to brute force attacks discover obscured links.
Believing only in secrecy to protect your data may be a dangerous decision. It means that if the secret gets out, you simply do not have any security.
Security by obscurity depends on the difficulty of discovering how to request access to the data. However, once it is known, accessing the obscured data is trivial.
Let’s consider the example of shareable links. If we can discover the patterns of defining a link, we can execute a brute force attack to get several obscured links.
Secrecy is an improvement to any security method. However, alone, it is equivalent to burying a treasure: anyone who can read the red “X” in the map can also get the coins.
Cybersecurity professionals criticize security by obscurity in some scenarios because of one principal reason: systems use it as the only security method.
However, we can use security by obscurity as an extra security layer that works with other security methods. So, security by obscurity becomes a powerful method to reduce the chances of an attack on a system being successful.
We can divide security methods into two main classes: the ones that reduce the probability of being attacked and the ones that reduce the impact of an attack. Security by obscurity works by reducing the probabilities of being attacked.
The probability of attacks occurring gets smaller as we compose methods to make the attacker’s life harder. But, even with a small attack probability, it still exists. So, system engineers should plan to adopt other security methods to reduce the system damage if an attack occurs.
Thus, we have the most efficient way to employ security by obscurity: including it in a system with multiple probability reduction security methods and at least a few impact reduction methods.
In this tutorial, we learned about security by obscurity. First, we had outlined particular concepts of security methods, showing some relevant categories of them in the current digital world. So, we in-depth explored security by obscurity, presenting how it works, inadequate use scenarios, and good use scenarios.
We can conclude that security by obscurity is a powerful security method if well used. This method acts on reducing the probability of executing successful attacks on systems. However, it does not prevent damages when attacks occur, thus requiring the coexistence of impact reduction security methods in our systems.