Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 25, 2025
In this tutorial, we’ll learn about the common name and subject alternative name attributes in the X.509 certificate. Besides that, we’ll demonstrate the method for extracting those fields using the openssl command-line tool.
X.509 certificate is a standard format for public key certificates. The certificate contains information about the public key and the entity associated with the public key. The entity can be anything, but most commonly, they’re usually associated with a person, an internet service, or a computer.
The secure socket layer (SSL) and transport layer security (TLS) are two common protocols that utilize the X.509 certificate to establish an end-to-end encrypted connection between two hosts. The main difference between the two protocols is that the TLS is a newer protocol that aims to replace the SSL protocol. These two protocols, in turn, are used by many other protocols to secure a channel before other communication takes place.
For example, HTTPS is an HTTP protocol that first establishes a secure connection using TLS before normal HTTP communication takes place. Besides that, services like PostgreSQL and Apache Kafka offer the possibility to secure the connection using TLS on top of their TCP-based protocol.HTTPS is an HTTP protocol that first establishes a secure connection using TLS before normal HTTP communication takes place.
One important aspect of the X.509 certificate is the ability of the receiver to validate the identity of the certificate presenter. This validation can be done through the value in the common name attribute and the subject alternative name extensions.
In every X.509 certificate, there’s a common name (CN) attribute. This attribute tells the certificate receiver the name of the entity that owns the public key in the certificate. Besides that, there’s an X.509 extension, subject alternative names (SAN), that stores other identifiers. In the context of HTTPS, the CN, and SAN will contain domain names or, in some cases, the IP addresses of the server.
Let’s look at a real-world example. First, we visit the baeldung.com website on our browser. Then, we press on the lock icon beside the address bar to open up the certificate viewer. This window displays the information on the certificate of the server:
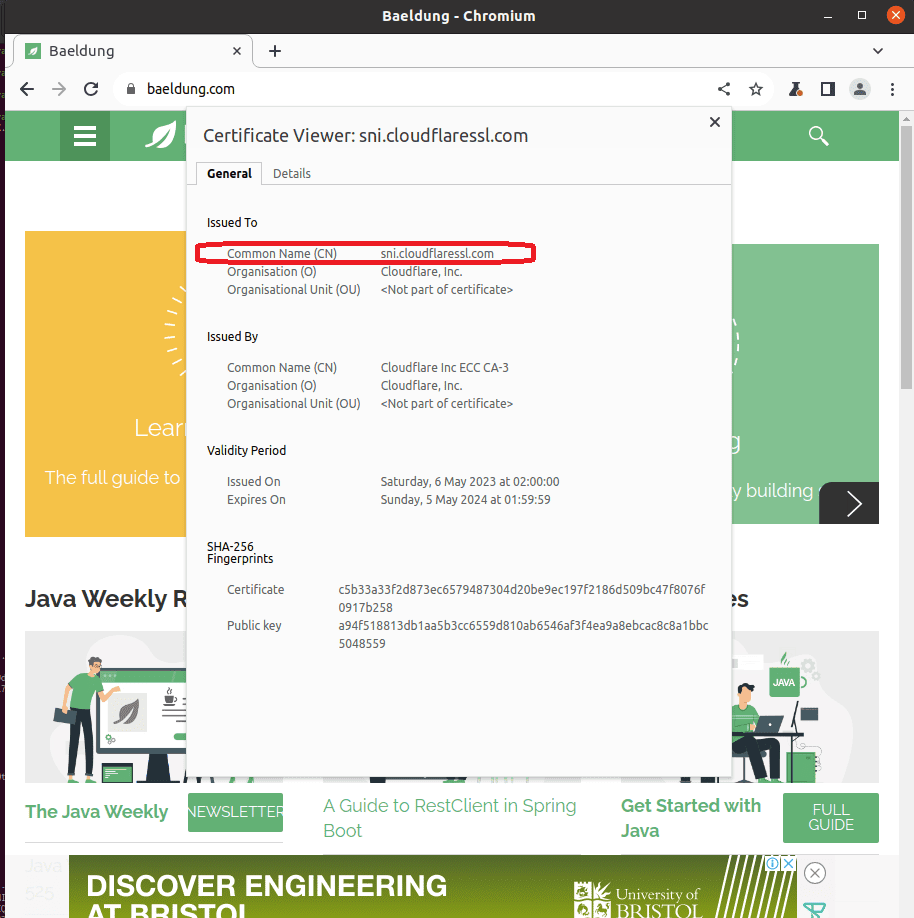
From the information, we can see that the certificate CN’s value is sni.cloudflaressl.com. Besides that, it also displays other information, such as the validity period and the public key.
We can open up the details tab to look for the SAN values:
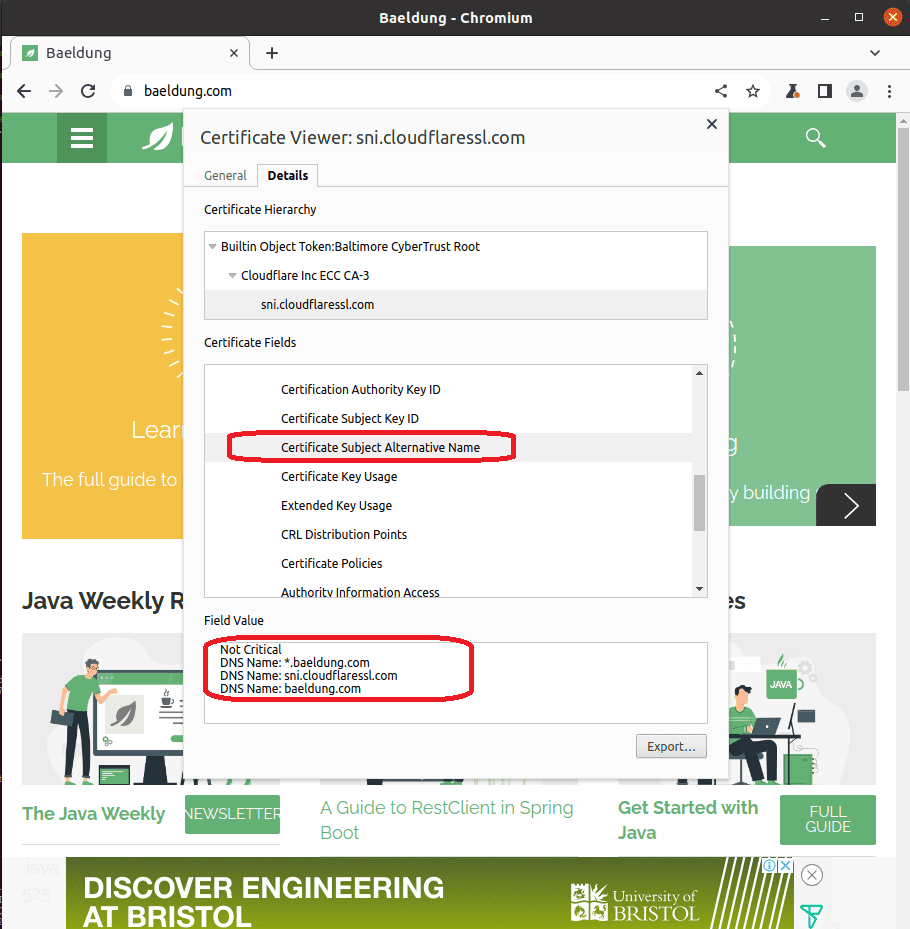
Notably, we can see that the CN of the certificate doesn’t match baeldung.com, which is the domain name we’re connecting to. This is because, since RFC 2818, SAN is preferred over CN for specifying the name of the subject in a certificate. Therefore, most of the clients prioritize the SAN values in place of the CN when it’s available.
One important security consideration of an X.509 is that we can validate the owner’s identity through the CN and SAN values in the certificate. In our previous section, we can see that the domain name baeldung.com we’re connecting with shows up in one of the SAN lists. This confirms that we’re indeed talking to the server that owns the domain name baeldung.com, and we can safely encrypt our secret using its public key.
On the other hand, malicious attackers can intercept the connection and relay their certificates that are completely legitimate to the client. If the client doesn’t perform hostname verification, it’ll happily accept the certificate and use the public key to establish a secure communication channel with the attacker.
One way we can inspect the CN and SAN of an X.509 certificate is to manually inspect the certificate on our browser. However, this method is rigid as it only makes exploring the certificate possible if the server serves HTTPS.
In the subsequent sections, we’ll learn about the openssl command that allows us to parse X.509 certificates and extract the CN and SAN fields.
To ease our demonstration, we’ll first download and save an X.509 certificate. We’ll use the openssl s_client -showcerts command to obtain the certificate:
$ openssl s_client -showcerts -connect baeldung.com:443 </dev/null |openssl x509 -outform PEM >baeldung-cert.pemThe oneliner above first uses the openssl s_client to connect to the HTTPS port of baeldung.com. Then, we send a null character to the connection to terminate the connection after obtaining the certificate. Finally, we pipe the certificate content to the openssl x509 command to convert it into the PEM format and save it as baeldung-cert.pem.
Reading the content of the certificate using the cat command, we can validate that the certificate is correctly saved:
$ cat baeldung-cert.pem
-----BEGIN CERTIFICATE-----
MIIFODCCBN6gAwIBAgIQDH4V4krgN6I1AXM6KK4EejAKBggqhkjOPQQDAjBKMQsw
CQYDVQQGEwJVUzEZMBcGA1UEChMQQ2xvdWRmbGFyZSwgSW5jLjEgMB4GA1UEAxMX
....(truncated)
-----END CERTIFICATE-----The x509 subcommand under the openssl toolkit can parse and read the X.509 certificate.
To obtain the CN attribute from the certificate file, we pass the -subject option to the openssl x509 command:
$ openssl x509 -noout -subject -in baeldung-cert.pem -nameopt multiline | grep commonName
commonName = sni.cloudflaressl.comThe one-liner above comprises two parts. The first part use the openssl x509 command to read the baeldung-cert.pem file and prints its subject. Additionally, we pass the option -nameopt multiline to print each subject information in a new line.
With each of the subject information in the new line, we can then select the line with CN using the grep command. Specifically, we’ll grep for any line that contains the word commonName.
We can also use the openssl x509 command to extract the SAN attribute of a certificate through the option -ext subjectAltName:
$ openssl x509 -noout -ext subjectAltName -in baeldung-cert.pem
X509v3 Subject Alternative Name:
DNS:*.baeldung.com, DNS:sni.cloudflaressl.com, DNS:baeldung.comThe SAN values are prefixed with DNS to indicate that it’s of the type domain name.
In this tutorial, we’ve explored the importance of the CN and SAN attributes of an X.509 certificate. Then, we demonstrated the openssl x509 command with the -subject and -ext subjectAltName to extract CN and SAN from an X.509 certificate.