Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: September 10, 2025
Voice over Internet Protocol (VoIP) allows voice calls over the internet, offering flexibility and cost savings for businesses. However, this convenience comes with security risks. VoIP systems are frequent targets for hackers aiming to intercept calls, commit fraud, or disrupt services.
In this tutorial, we’ll outline the most common types of VoIP attacks and provide practical countermeasures to help protect the communications infrastructure.
VoIP transforms traditional voice communication by converting sound signals into digital data packets. When someone speaks into a VoIP device or application, their voice is digitized and organized into packets. These packets are then transmitted over the Internet or private IP networks to the recipient, where they are reassembled and converted back into audio:
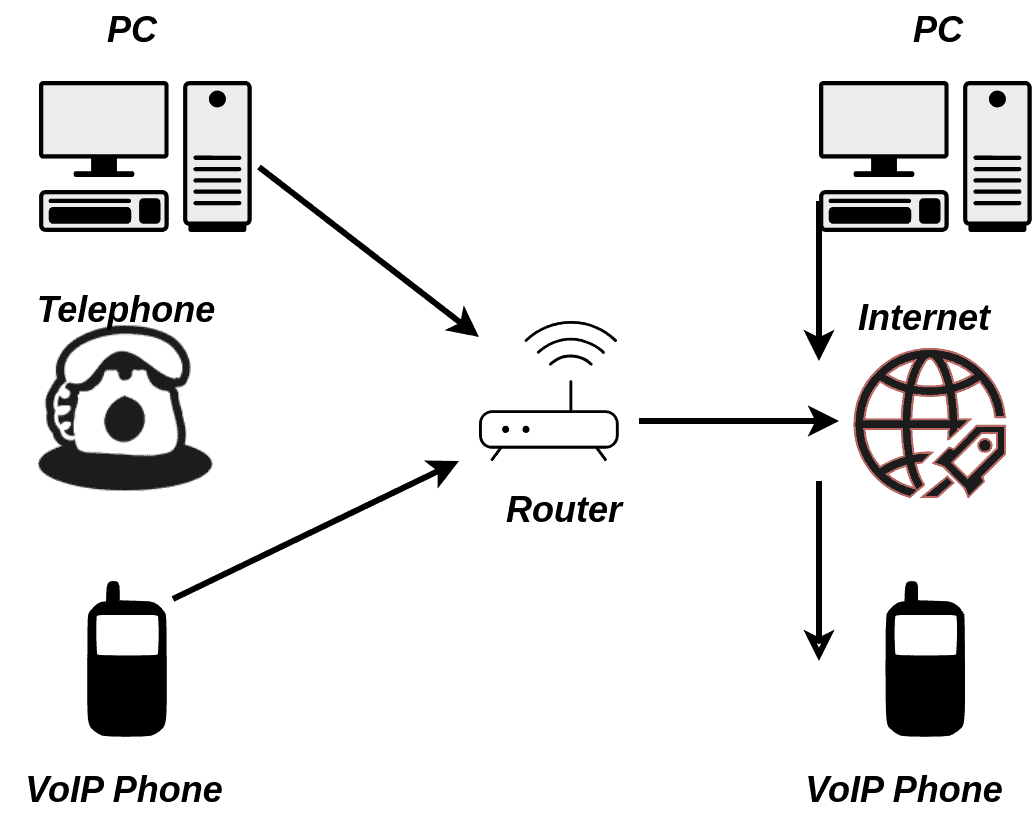
While VoIP offers cost savings and flexibility, it introduces security challenges.
Because VoIP relies on open internet protocols and often travels across public networks, it’s vulnerable to packet interception, identity spoofing, and service disruption. Without strong encryption and authentication, voice data and signaling information can be intercepted or altered. So, it’s essential to secure each component and communication channel.
VoIP systems are vulnerable to various cyberattacks due to their use of open standards and Internet-based protocols. So, below are the most prevalent attack types, including newer threats like SPIT and TDoS.
Eavesdropping occurs when attackers intercept voice packets traveling across the network. This is especially problematic on shared or public networks. If these packets are unencrypted, anyone with access to the network can capture and listen to calls using tools like Wireshark or specialized VoIP sniffers:
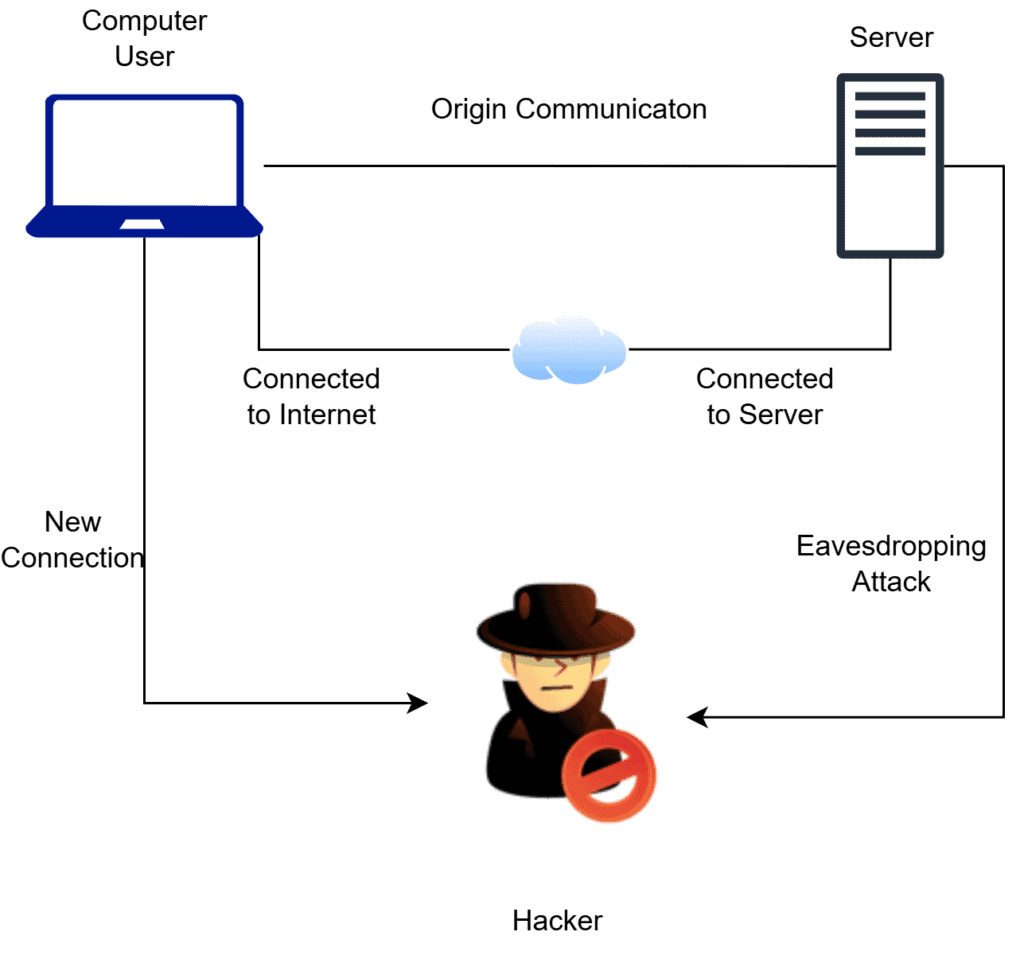
In VoIP systems, the lack of encryption for both SIP signaling and RTP audio streams leaves conversations exposed. Attackers can gather sensitive information such as login credentials, business plans, or customer data. This type of attack is typically passive, making it hard to detect without constant monitoring.
SIP (Session Initiation Protocol) handles the signaling required to establish and manage VoIP calls. Attackers can hijack SIP registration by sending a spoofed registration request to the SIP server using stolen or guessed credentials.
Once registered, the attacker can impersonate a legitimate user, receiving incoming calls and making outgoing calls on their behalf. This allows attackers to conduct fraud, intercept conversations, or manipulate call routing, potentially causing reputational and financial damage.
Call redirection exploits vulnerabilities in VoIP systems to silently reroute calls through unauthorized or malicious intermediaries. The attacker can configure the system to forward calls to a server under their control.
Attackers can record, modify, or redirect these calls to other destinations. Victims usually remain unaware of the redirection, which makes this a particularly insidious form of surveillance or fraud. Attackers often combine it with spoofing techniques to further conceal their involvement.
Toll fraud targets VoIP systems by exploiting weaknesses to make unauthorized premium-rate or international calls. Attackers often gain access through unsecured interfaces, weak credentials, or compromised voicemail systems.
After gaining access, attackers program the system to auto-dial costly numbers, often during non-business hours, to avoid detection. The financial impact can be significant, with victims discovering the breach only after receiving inflated bills.
Voicemail systems are often overlooked in security planning. Many users fail to change default PINs or use weak passwords, making voicemail accounts easy targets for attackers.
By exploiting these weaknesses, attackers can listen to sensitive messages, reset user passwords, or use voicemail to impersonate the target. Also, since voicemail systems are typically less monitored than live traffic, breaches can persist for extended periods without detection.
In caller ID spoofing, attackers manipulate the information that appears on the recipient’s caller ID display. Phishing attacks commonly use this tactic, allowing attackers to impersonate banks, companies, or trusted contacts.
Spoofing is easy in VoIP due to weak verification mechanisms in SIP headers. Attackers exploit this by launching social engineering campaigns that deceive users into revealing sensitive information or performing risky actions, such as transferring funds or clicking malicious links.
MitM attacks involve intercepting communication between two parties without their knowledge. In VoIP, this usually occurs when unencrypted traffic passes through shared or public networks.
Attackers can listen, record, or even modify conversations in real-time. By placing themselves between endpoints, they can alter call content or inject commands, causing reputational and operational harm. This is particularly dangerous in environments lacking TLS and SRTP protections.
SPIT is the VoIP equivalent of email spam. Attackers flood systems with unwanted prerecorded calls, often pushing advertising or scams. Unlike email, voice spam is more disruptive due to its real-time and attention-demanding nature.
Excessive SPIT can overwhelm voicemail boxes, tie up lines, and degrade user experience. Attackers use auto-dialers and botnets to initiate thousands of calls, exploiting the openness of SIP endpoints that lack rate limiting or CAPTCHA protections.
TDoS attacks aim to overwhelm VoIP servers or phone lines with traffic to disrupt voice services. This can render entire systems unusable, affecting customer support, emergency services, and internal communication.
Attackers typically use automated tools to flood SIP endpoints or call queues with fake traffic, consuming system resources. Sometimes, TDoS is used as a diversion for larger attacks or extortion schemes, where attackers demand ransom to stop the attack.
VoIP security requires a multi-layered approach to protect against threats like eavesdropping, spoofing, and fraud. Key areas include encryption, authentication, access control, network defenses, and ongoing monitoring.
TLS (Transport Layer Security) should be used to encrypt SIP signaling, while SRTP (Secure Real-Time Transport Protocol) secures voice streams. These protocols prevent interception and tampering of both call setup and audio data.
Encryption uses specialized algorithms to perform cryptographic operations on plaintext data, applying an encryption key to transform it into a secure format.
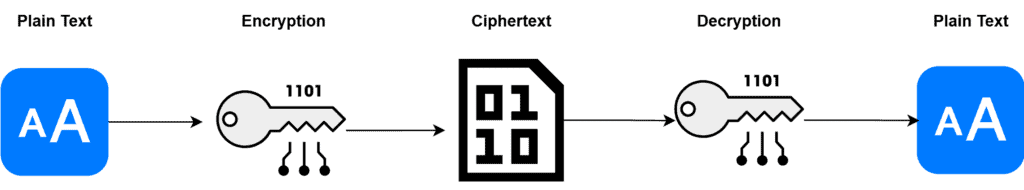
All VoIP components must support and enforce encrypted communication. Certificates and encryption settings should be properly managed to avoid configuration issues and ensure protocol integrity.
Strong, regularly updated credentials reduce the risk of SIP hijacking and unauthorized access. Moreover, multi-factor authentication adds further protection, especially for administrative interfaces and voicemail systems.
Features not required for operations, such as international dialing or call forwarding, should be disabled. Access control policies must be based on roles, with users granted only the permissions necessary for their tasks.
The STIR/SHAKEN protocol helps verify caller identity using digital certificates, mitigating caller ID spoofing and supporting trust in inbound communications.
Adoption of this framework by service providers enhances call validation. Thus, additional protections, including caller reputation databases and filtering tools, can reduce exposure to fraudulent calls.
Segmenting VoIP traffic using VLANs or dedicated subnets enhances security by isolating voice data from other services. This limits lateral movement in the event of a breach.
SIP-aware firewalls and Session Border Controllers (SBCs) provide inspection, policy enforcement, and threat filtering at the network edge. These tools also help obscure internal infrastructure from external entities.
Continuous monitoring of logs, call patterns, and access events supports early detection of suspicious activity. Alerts and analytics tools assist in identifying anomalies in real time.
Routine patching of VoIP software and firmware is essential to address known vulnerabilities. Security audits, permission reviews, and incident response testing contribute to a resilient environment.
One significant example involves toll fraud in VoIP systems, where attackers gained unauthorized access to a private branch exchange (PBX) and routed international and premium-rate calls through it. Victims were billed heavily for these calls, often only discovering the fraud after receiving exorbitant phone bills. This type of exploitation typifies how weak authentication and voicemail misconfiguration can be leveraged for financial gain.
This case highlights why enforcing strong credentials, restricting outbound calling, and monitoring call patterns are crucial. Moreover, inadequate safeguards in VoIP systems expose organizations to severe financial loss and operational disruption, particularly when attackers exploit voicemail or management interfaces to launch automated outbound dialing campaigns.
As VoIP use expands, threats also increase, ranging from traditional risks like vishing and insecure mobile apps to new dangers brought by AI. Additionally, cloud-based systems and remote work widen the attack surface, which demands updated security strategies.
AI strengthens VoIP defenses by enabling smarter detection and response. For example, machine learning models analyze call patterns, identify anomalies, and flag suspicious behavior in real time. Moreover, AI systems detect spoofed traffic, block spam calls, and adapt to evolving threats faster than static rule-based systems. Behavioral analysis adds another layer by learning how users typically communicate, which helps detect impersonation or unauthorized use more easily.
Additionally, AI improves monitoring efficiency by reducing the workload on human analysts while increasing accuracy. Consequently, these capabilities enable organizations to respond quickly to fraud attempts and system misuse.
While AI defends, it also arms attackers with powerful tools. Deepfake voice technology can clone speech patterns and tones, allowing malicious actors to impersonate executives, colleagues, or service providers with alarming realism. These synthetic voices can bypass voice authentication systems and manipulate targets during calls.
Additionally, AI-driven phishing bots can conduct large-scale phishing campaigns using lifelike speech, tailored responses, and context-aware dialogue, making scams more convincing and harder to filter. Combined with caller ID spoofing, these tactics undermine trust in voice communication.
As VoIP systems evolve, security teams must prepare for attacks that are not only technical but also psychological, driven by AI’s ability to mimic human behavior.
In this article, we explored the common types of VoIP attacks alongside practical countermeasures like encryption, strong authentication, and network segmentation.
VoIP technology revolutionizes communication by enabling voice calls over the internet, offering flexibility and cost savings. However, it also introduces security risks such as eavesdropping, toll fraud, and session hijacking.