1. Introduction
In recent years, computer networks have become one of the most relevant technologies in the world. Currently, the Internet provides multiple services for us, and accessing the World Wide Web is an everyday activity for most people.
Information and systems, including sensitive ones, are available in computer networks. So, naturally, we must use mechanisms to protect them. Among these mechanisms, we can cite antiviruses, intrusion detection systems, intrusion prevention systems, and, most importantly, firewalls.
In this tutorial, we’ll study the different types of firewalls. Initially, we’ll have a brief review of general concepts about firewalls. Thus, we’ll investigate each type of firewall specifically. Finally, we’ll compare these firewall types in a systematic summary.
2. A Brief Review on Firewalls
First of all, we can understand firewalls as networked security devices. The central purpose of a firewall device is to inspect both incoming and outgoing traffic and decide which to block according to a particular set of rules or policies.
These inspections can be from simple address checking, such as blocking packets according to their source or destination addresses, to more sophisticated routines, such as searching for signatures in packets’ payload.
Sometimes firewalls are combined with other security mechanisms, such as antiviruses, creating the next-generation firewalls.
Furthermore, firewalls can operate in a stateless or stateful manner. Stateless firewalls do not keep any information regarding the connections between clients and servers, inspecting each packet independently. Stateful firewalls, in turn, keep track of the connections, thus monitoring their stages and identifying unusual and potentially malicious behavior on them.
At last, we can implement firewalls as physical (middleboxes) or virtual devices (using Network Function Virtualization, for instance). These mechanisms may execute independently in the network or even be integrated into complex security systems and architectures, such as demilitarized zones.
3. Types of Firewalls
There are three main types of firewalls:
- packet filter firewall
- application-level firewall
- circuit-level firewall
Each one of these types presents particular properties and different execution models. Let’s see details about them in the following subsections.
3.1. Packet Filter Firewall
We can see packet filter firewalls as the most common type working in networks. These firewalls employ a set of rules applied to the incoming network traffic. If a packet does not violate any rule, the firewall forwards it to the next destination; otherwise, the firewall discards it immediately.
We can see the overall operation of packet filtering firewalls:
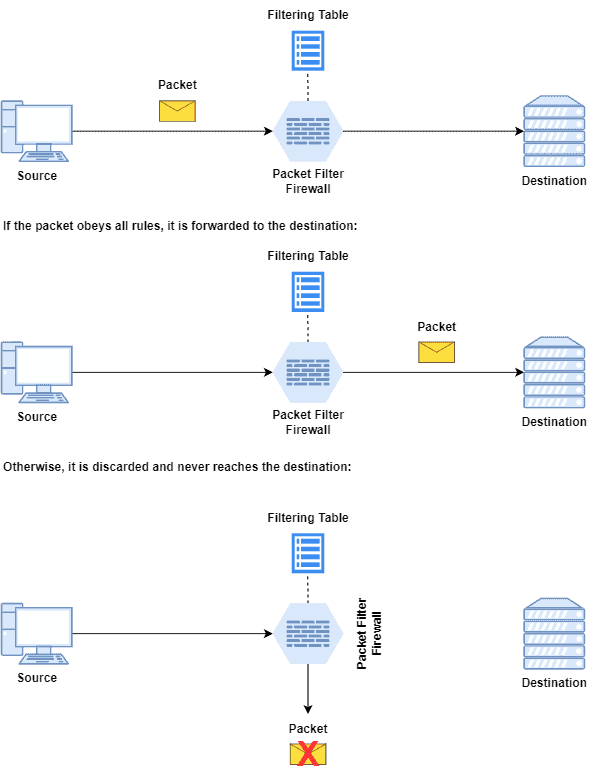
Packet filtering rules, in turn, are predefined. It means the rules do not change in the firewall lifecycle (except, of course, the network operator actively changes them).
Most of the rules are based on the protocols’ headers encapsulating the packets and on the information provided by them. For example, we can define specific rules for blocking particular IP addresses (source or destination), ports (in the transport layer), or even protocols (ICMP, IP, TCP, UDP, among others).
In this way, packet filter firewalls keep their rules in a data structure called a filtering table, which is queried to decide on packet forwarding or discarding.
Packet filter firewalls are pretty simple and fast ones. They do not deep inspect the packet nor employ any historical information during their execution: forwarding or discarding each packet is an atomic and independent operation.
Due to these characteristics, malicious entities create multiple attacks to overcome packet filter firewalls, such as faking source or destination addresses in the packets.
3.2. Application-level Firewalls
Application-level firewalls work by intermediating the data exchange between two entities, catching requests and responses. This firewall type is also known as a proxy firewall or application-level gateway.
In practice, the application-level firewalls establish connections with clients and servers, intermediating communication. To do that, these firewalls typically work with several TCP-based protocols, such as FTP, HTTP, SMTP, Telnet, etc.
Thus, clients establish connections with the application-level firewall, which check the client’s authentication and permissions. In such a way, the client sends requests for some service to the firewall. The firewall receives the requests, checks if it is valid and comes from an authorized entity, establishes a connection with the requested server, and forwards the request to it.
Then, the server catches the request and sends the processing result to the firewall, which checks the server’s authentication and forwards the results to the respective requesting client:
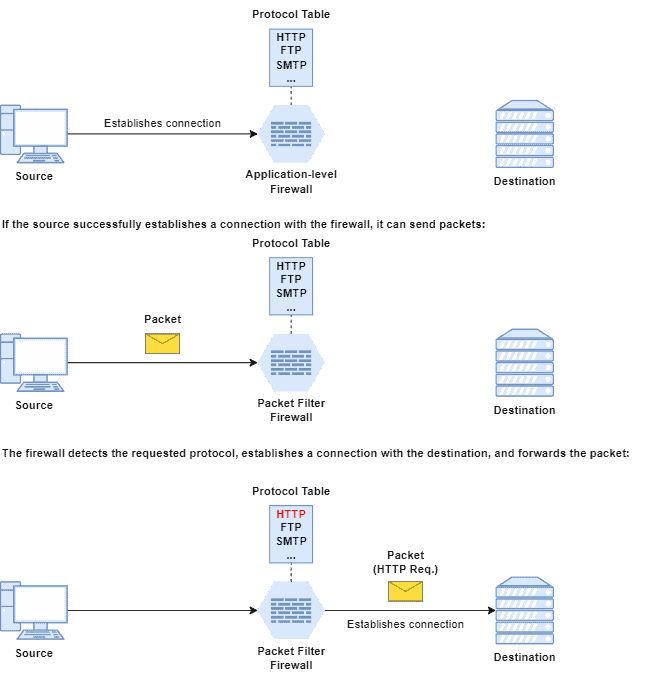
Of course, if any authentication or permission testing fails, the packets are immediately discarded by the application-level firewall.
It is relevant to highlight that although the client and server communicate through the firewall, they feel like communicating with each other directly. In other words, the firewall should be transparent to them.
Furthermore, since the application-level firewall intermediate connections, it can do a deep inspection of the received packets, which makes it typically more secure than packet filter firewalls. However, the operating mode of application-level firewalls also imposes extra overhead. So, clients and servers can experience extra latency (for example) when communicating.
3.3. Circuit-level Firewall
Circuit-level firewalls, called circuit-level gateways, also establish connections between entities trying to communicate. In this aspect, circuit-level firewalls operate similarly to application-level firewalls.
However, circuit-level gateways operate in the session layer of the OSI model, checking if a communication session is legit. So, these firewalls do not work monitoring particular applications, as the application-level firewalls do.
In such a way, a circuit-level firewall first verifies how the SYN and ACK message exchanges occur between entities trying to connect. So, the firewall aborts a connection if it notes something wrong with such messages, such as an SYN flood attack.
In other cases, if the TCP handshake occurs as expected, the firewall creates an internal circuit between the entities to exchange data.
The following image depicts the connection establishment between two entities in a circuit-level firewall:
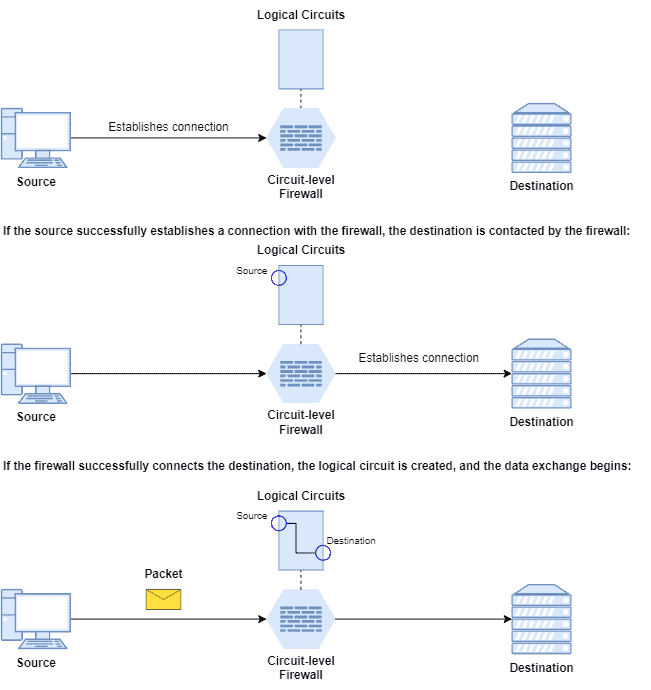
It is relevant to note that once a circuit-level firewall establishes a connection between two entities, any application can execute through this connection since it does not inspect the application layer data.
So, in short, a circuit-level firewall tackles potential threats during the connection establishment but does not deal with threats regarding individual packets in an existing connection. Otherwise, we can use packet filters and application-level firewalls to inspect individual packets.
4. Systematic Summary
Firewalls are security devices for inspecting network traffic and deciding which packets or connections to block according to particular rules.
There are three different types of firewalls, each working with a particular aspect of a networked connection and in a specific network layer. We call these types packet filters, application-level, and circuit-level firewalls.
Packet filter firewalls manage the network traffic by analyzing packet header information. Application-level firewalls focus on the application layer, working as gateways between source and destination entities in networked communications. Finally, circuit-level firewalls work on the session layer, intermediating the connections between entities aiming to communicate with each other.
The following table summarizes and compares some characteristics of the presented firewall types:
5. Conclusion
In this tutorial, we investigated the types of firewalls. Initially, we recalled relevant concepts regarding firewalls. So, we studied each firewall type, observing its characteristics and operating modes. Finally, we compared the firewall types in a systematic summary.
We can conclude that firewalls are great solutions for securing networked entities and systems. But, we should choose the most suitable type of firewall considering our specific security purposes to achieve the best result possible.