Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
Connection-oriented and connectionless protocols are two types of communication protocols that are used in computer networks.
In this tutorial, we’ll compare connection-oriented protocols and connectionless protocols and see their characteristics and what makes them different.
A connection-oriented protocol establishes a dedicated connection between the devices in a network before transmitting data, and this connection is maintained throughout the communication and is terminated once the communication is over.
Connection-oriented protocols are reliable protocols that transmit packets to the receiver in the same order the sender has sent them and make sure that all data packets are delivered without any errors. Moreover, they typically use a handshake process to establish the connection between the devices, and they generally perform mechanisms such as flow control, error-checking, and retransmission to make communication even more reliable.
Flow control works by enabling the receiving device to inform the sending device about its buffer capacity or the amount of data it can receive at the moment. After that, the sending device adjusts its transmission rate to match the receiving device’s capacity. As a result, the receiving device won’t be overloaded with too much data, and problems like packet loss and network congestion are avoided.
After receiving each data packet from the sender, the receiver sends an acknowledgment packet back to the sender to indicate that the data was received successfully. Retransmission happens when the sending device does not receive an acknowledgment packet from the receiver within a certain period of time after sending the data. As a result, the sending device assumes that the receiving device did not receive the data and retransmits it.
The handshake process involves sending a series of messages between the sender and the receiver that include information about the parameters of the connection, such as the type of protocol to be used, the size of packets, supported features, and so on.
For example, the TCP protocol, which is a connection-oriented protocol, uses a three-way handshake process to establish a connection between the two devices. First, the sender sends a SYN (synchronize) message to the second device, then the second device responds with a SYN-ACK (synchronize-acknowledge) message. Finally, the sender sends an ACK (acknowledge) message to the second device to confirm the connection. Now the connection is established, and data can reliably be transmitted between the devices:
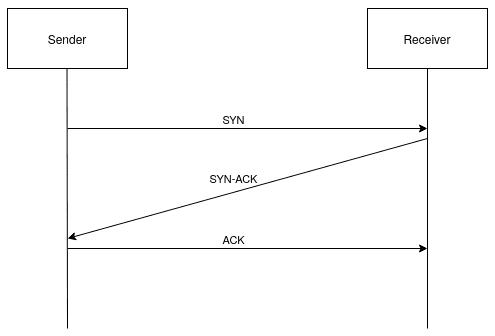
Connection-oriented protocols use techniques such as sequencing and acknowledgment to verify that the data is received reliably and in the same order the sender has sent them:
TCP (Transmission Control Protocol) is an example of a connection-oriented protocol that provides a reliable, error-checked, and ordered delivery of data packets between devices in a network. Furthermore, TCP is a transport layer protocol in the internet protocol suite. TCP is used for:
Some other examples of connection-oriented protocols are ATM (Asynchronous Transfer Mode) and SCTP (Stream Control Transmission Protocol).
A connectionless protocol doesn’t establish a dedicated connection between devices before transmitting data. A connectionless protocol sends each packet as an independent unit and transmits them separately. Unlike connection-oriented protocols, connectionless protocols don’t guarantee the delivery of all packets or to deliver them in order. In addition, they don’t perform mechanisms like flow control and error checking.
UDP (User Datagram Protocol) is an example of a connectionless protocol that is used for the fast delivery of information where a degree of packet loss is generally acceptable if it allows for faster transmission of data. Moreover, UDP is a transport layer protocol in the internet protocol suite. UDP is used in situations where speed is more important than reliability. Online gaming, real-time video and audio streaming, and VoIP (Voice over Internet Protocol) are example use cases of UDP.
Moreover, ICMP (Internet Control Message Protocol) and ARP (Address Resolution Protocol) are other examples of connectionless protocols. ICMP is a network layer protocol in the internet protocol suite used for network management and troubleshooting, and ARP is used to map IP addresses to physical MAC addresses in a local network.
Connection-oriented protocols are more reliable but have higher overhead and latency because of the handshake process, ordered delivery of data packets, and performing multiple mechanisms such as flow control and error checking. On the other hand, connectionless protocols provide faster communication but are less reliable and don’t perform flow control or error checking.
Therefore, connection-oriented protocols are used when reliability is more important than speed like file sharing and sending emails. On the other hand, connectionless protocols are used when speed is more important than reliability, and some level of packet loss and delay is generally acceptable. Real-time applications like video streaming and online gaming are example use cases of connectionless protocols.
| Connection-oriented | Connectionless |
|---|---|
| Establishes a dedicated connection before sending data | Doesn’t establish a dedicated connection before sending data |
| More reliable | Faster |
| Performs handshaking | Doesn’t perform handshaking |
| Data is delivered in the same order the sender has sent them | No guarantee that the data is delivered in order |
| Performs flow control and error checking | Doesn’t perform flow control or error checking |
In this tutorial, we learned about the differences between connection-oriented and connectionless protocols, their characteristics, and their use cases. Ultimately, the choice of protocol depends on the needs and requirements of the application.