Yes, we're now running our Black Friday Sale. All Access and Pro are 33% off until 2nd December, 2025:
Protocols Used for PING
Last updated: March 18, 2024
1. Introduction
Ping (Packet Internet or Inter-Network Groper) is a networking utility for checking if a remote computer or node is reachable by a host on a network. A variety of protocols can be used with Ping such as AppleTalk, Connectionless Network Service (CLNS), IP, Internetwork Packet Exchange (IPX), Apollo, VIP (VINES Internetwork Protocol), and Xerox Network Systems (XNS). In this tutorial, we’ll try to explain the protocols used by ping and explore various aspects of them.
2. Internet Protocols for Ping
The default protocol used for a network is Internet Protocol (IP). Several layers in an IP stack such as Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP) are involved in the ping process. Ping comes with an operating system with network support to check if an IP address can be reached. Depending on the purpose of use, the ping uses ICMP and ARP protocols and is different from TCP and UDP. Often ping is used as a generic term to test connections for TCP and UDP ports using different tools like Telnet and Nmap. Let’s consider tcping, another console application that works over a TCP port to ping.
2.1. ARP
Address resolution refers to the process of finding an address of a computer in a network. Ping uses ARP protocol to identify the MAC address of the remote computer. Let’s assume that the ARP request with the IP address of the source computer (say Host 1) is sent to the target computer (say Host 2). In reply to the ARP request, Host 2 sends a reply with its IP and MAC address. To avoid the repetitive address resolution requests, Host 1 will cache the resolved addresses (IP and MAC) for a (short) duration: 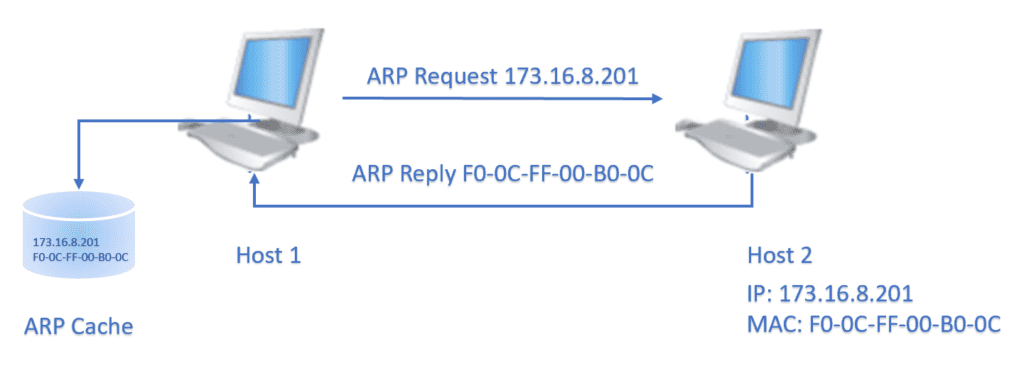
2.2. ICMP
The ICMP protocol provides the code and types with no specific port number for the ping command: The ping utility contains a client interface to ICMP protocol and uses the echo request (Type 8), and echo reply (Type 0) messages. When a ping command is issued from a source machine, an echo-request packet is sent to the IP address of the target machine: 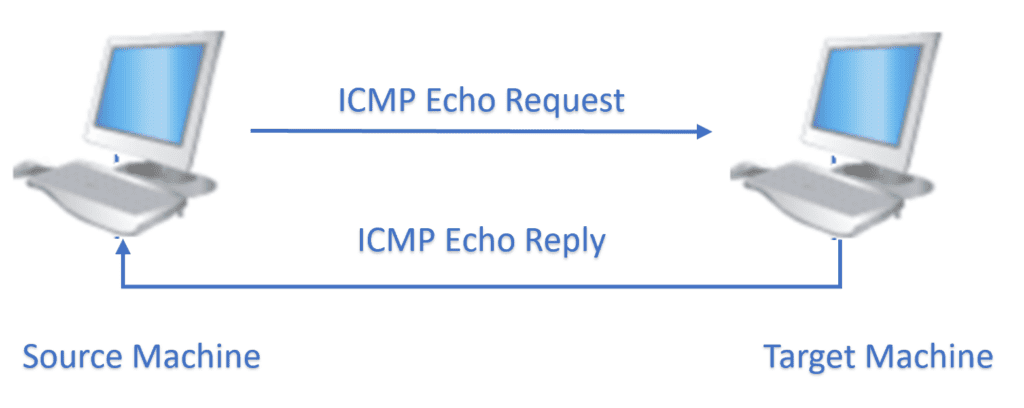 This ICMP echo request is generated to confirm whether the target machine is reachable. The target machine responds to the echo-request using an ICMP echo reply. In this reply, the ping program receives the target machine IP, and the latency information, a timestamp value indicating the transmission time. Two ICMP variants are available to support IPv4 and IPv6.
This ICMP echo request is generated to confirm whether the target machine is reachable. The target machine responds to the echo-request using an ICMP echo reply. In this reply, the ping program receives the target machine IP, and the latency information, a timestamp value indicating the transmission time. Two ICMP variants are available to support IPv4 and IPv6.
2.3. AppleTalk
Ping sends AEP (AppleTalk Echo Protocol) packets to the target AppleTalk node and waits for replies. We can see the reply text format below:
| Reply Text | Description |
|---|---|
| ! | Reply received |
| Time-out | Target machine is taking too long to reply to a request made from the source device. |
| B | Bad echo reply received |
| C | Echo with bad DDP checksum received |
| E | Error encountered during sending of the echo |
| R | No route available to send the echo packet |
2.4. CLNS
To check the status of a remote CLNS node, Ping is using a “ping clns”command and we can see the reply text format and description below:
| Reply Text | Description |
|---|---|
| ! | Reply received |
| . | Target machine is taking too long to reply to a request made from the source device. |
| x | Reply was received with an error code |
3. How Does Ping Work?
Working of ping is simple, let’s type in the command prompt “ping”:
C:\>ping
Usage: ping [-t] [-a] [-n count] [-l size] [-f] [-i TTL] [-v TOS]
[-r count] [-s count] [[-j host-list] | [-k host-list]]
[-w timeout] [-R] [-S srcaddr] [-c compartment] [-p]
[-4] [-6] target_name
Options:
-t Ping the specified host until stopped.
To see statistics and continue - type Control-Break;
To stop - type Control-C.
-a Resolve addresses to hostnames.
-n count Number of echo requests to send.
-l size Send buffer size.
-f Set Don't Fragment flag in packet (IPv4-only).
-i TTL Time To Live.
-v TOS Type Of Service (IPv4-only. This setting has been deprecated
and has no effect on the type of service field in the IP
Header).
-r count Record route for count hops (IPv4-only).
-s count Timestamp for count hops (IPv4-only).
-j host-list Loose source route along host-list (IPv4-only).
-k host-list Strict source route along host-list (IPv4-only).
-w timeout Timeout in milliseconds to wait for each reply.
-R Use routing header to test reverse route also (IPv6-only).
Per RFC 5095 the use of this routing header has been
deprecated. Some systems may drop echo requests if
this header is used.
-S srcaddr Source address to use.
-c compartment Routing compartment identifier.
-p Ping a Hyper-V Network Virtualization provider address.
-4 Force using IPv4.
-6 Force using IPv6.Ping does the following checks:
- Whether there’s a connection between the source IP and destination IP on the network.
- The speed of the connection (latency).
Most often using the ping command without any option is sufficient to verify if a machine in a network is reachable. However, for advanced troubleshooting of any connection issues, “options” are used. The options -f, -v, -r, -s, -j, -k supports IPv4, and the -R and -S only IPv6. The ping command sends several echo requests to the destination address and the result is displayed. We can see that the reply provides information such as the request status, how many bytes were received in reply, latency, packet loss, and round trip times as shown below:
C:\>ping www.baeldung.com
Pinging www.baeldung.com [2606:4700:20::681a:c4a] with 32 bytes of data:
Request timed out.
Reply from 2606:4700:20::681a:c4a: time=110ms
Reply from 2606:4700:20::681a:c4a: time=114ms
Reply from 2606:4700:20::681a:c4a: time=107ms
Ping statistics for 2606:4700:20::681a:c4a:
Packets: Sent = 4, Received = 3, Lost = 1 (25% loss),
Approximate round trip times in milli-seconds:
Minimum = 107ms, Maximum = 114ms, Average = 110ms4. How to Use Ping?
Ping can be used for several purposes such as in scripts for tracking system usage, troubleshooting to trace network access, and find devices in a network. Broadly the use of ping can be classified as the following:
- Troubleshooting – A series of ping commands can be used to resolve connection issues to find if an IP is reachable or not.
- Device discovery – Ping allows finding connected devices in the network.
- Network monitoring- Common use is to use the -t option (until stopped) of ping. If the reply is timed out or delayed for too long then there is an issue with the system access.
Let’s consider the following table with a comparison of the use of ping in Windows and Linux:
| Windows | Linux |
|---|---|
| Command uses a 32 bytes long message | Command uses a 64 bytes long message |
| Sends only four messages as per default setting | Sends continuous messages until ask to stop |
| Adds an 8-byte timestamp to echo request | Assigns a sequence number to echo request |
| Timestamp is used to calculate round-trip delays | Replies are asynchronous, that is echo replies are not in same order as echo requests |
| For IPv4 or IPv6 addresses use ping -4/ping -6 | Use ping /ping -6 |
5. Security Issue
Ping replies may yield information about the operating system, machine IP, and MAC and may cause security concerns. Sophisticated cyber attackers may utilize this information for malicious attacks on the target machines. In an identified network, attackers may use ping to get a list of the systems that are reachable and responding. To avoid a security breach, many firewalls block ping requests from untrusted networks.
6. Conclusion
In this article, we’ve gone over the concept and protocols behind the ping command. Ping is used to assessing the connections status and associated network parameters of the target machine. We can use it for the purpose of troubleshooting connection issues such as slowdown, packet loss, and network monitoring. In addition to IP protocol, ping can use several other protocols for debugging different network problems.