Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
The POODLE attack, also known as Padding Oracle On Downgraded Legacy Encryption, is a security vulnerability that poses a significant threat to the security of web applications. This attack targets the SSLv3 protocol, an outdated version of the SSL (Secured Socket Layer) protocol with numerous vulnerabilities.
However, some servers and clients still accept SSLv3 for backward compatibility.
In this tutorial, we’ll look at whether disabling SSLv3 is a viable mitigation to the risk of a POODLE attack, and the possible drawbacks of this approach.
Let’s see how the POODLE attack works.
Firstly there’s the SSL/TLS (Transport Layer Security), which uses cipher suites that allow servers and browsers to encrypt communication and protect the confidentiality and integrity of the data. However, some cipher suites use cipher-block chaining (CBC) mode, which is vulnerable to the POODLE attack.
SSLv3 calculates the message authentication code (MAC) value to protect data from tampering and adds this MAC value at the end.
Block ciphers require padding to meet the required length of data (i.e., multiples of block size). After this, SSLv3 encrypts the whole data with the MAC value and padding.
However, during decryption, SSLv3 skips the integrity check of the padding bytes. It only checks for the length of padding bytes. As long as the last byte is between 00 and 07, SSLv3 will accept the block.
Therefore, an attacker can decrypt the messages transmitted via SSLv3 protocol by manipulating the padding bytes.
SSL/TLS are cryptographic protocols used for secure communication over the Internet. TLSv1.3 is the latest version and is considered more secure than its older versions, including TLSv1.2, TLSv1.1, TLSv1.0, SSLv3, SSLv2, and SSLv1.
The POODLE attack mostly affects SSLv3. If we don’t disable it, clients might try to establish a connection via the older version of SSL/TLS, a protocol downgrade attack. In this type of attack, even though the server supports a higher version, the attacker forces the browser to fall back to an older version.
Specifically, an attacker can force the use of SSLv3 as long as the client and the server support it:
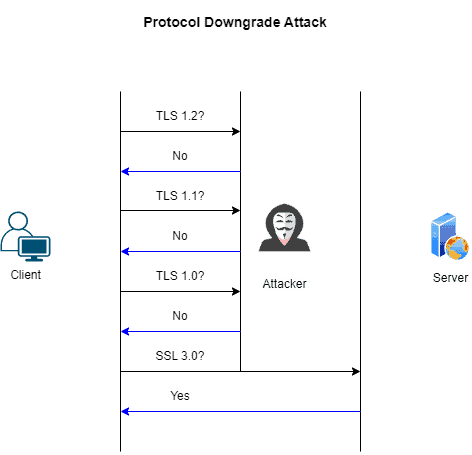
So, if we disable it, clients can’t be tricked into falling back to the vulnerable version or transmitting messages using the SSLv3 protocol. Overall, SSLv3 can prevent attackers from exploiting the design flaw in the protocol.
In this section, we’ll go over the methods needed to disable SSLv3 on two common reverse proxy servers – Apache and Nginx.
We have to edit the SSL configuration file, which is usually located in /etc/apache2/mods-available/ssl.conf. Firstly, let’s say we have this line in the configuration file:
SSLProtocol allWe need to disable vulnerable SSL/TLS versions, and change the above line:
SSLProtocol TLSv1.2This disables SSLv3 and allow a secure connection using TLSv1.2 only.
Alternatively, we can configure the server to accept connections using all other acceptable protocols except SSLv3:
SSLProtocol all -SSLv3By implementing either of these configurations, we can ensure secure connections using protocols other than SSLv3.
Similar to Apache, we must edit the /etc/nginx/nginx.conf file to disable SSLv3 in Nginx and ensure a secure connection. The configuration file may contain the following line:
ssl_protocols SSLv3 TLSv1 TLSv1.1 TLSv1.2;To disable SSLv3, let’s change the above line:
ssl_protocols TLSv1.2;Here, we can ensure the server communicates only via TLSv1.2 protocol, thereby enhancing security. But it might not be suitable in every case.
So, we can also change the line into this instead:
ssl_protocols TLSv1 TLSv1.1 TLSv1.2;The modifications in the configuration file outlined above ensure that the server communicates with acceptable protocols like TLSv1, TLSv1.1, and TLSv1.2.
Before disabling SSLv3, it is important to consider the following drawbacks:
In this article, we learned that the POODLE attack poses a significant threat to the security of web applications if it uses SSLv3 for establishing secure communication.
Although disabling SSLv3 may provide a workaround for this vulnerability, it may still cause compatibility and performance issues.
Therefore, it’s crucial to carefully assess the potential downsides of disabling SSLv3.