Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In computer networking, a port is an unsigned integer from 0 to 65535 that identifies a connection endpoint. That number allows the data to be routed to a specific service. For instance, on the same public IP, we might have a web service on port 443 and an SSH login on port 22. These are examples of well-known ports.
Whether a port responds to a connection attempt and what it responds to can be helpful for security-audit scenarios, such as checking if our home router or corporate firewall work as intended.
In this tutorial, we’ll look at various tools to ping an IP’s port to check its status (open, closed, stealth). In this case, the concept of ping is metaphorical because, technically, ping is port-agnostic. So, more precisely, we want to probe a port.
Before introducing Linux-specific tools, we’ll glance at a long-standing free online service.
A well-configured firewall should leave open only strictly necessary ports. But things don’t always go as planned. There are, for instance, routers with built-in firewalls that are severely buggy.
Before proceeding further, however, let’s focus on the meaning of open, closed, and stealth ports.
Open ports accept Internet packets and establish socket connections between client and server. In a world without cybercriminals, nothing is wrong with this. In fact, all publicly accessible services, such as Web servers, work this way.
The problem is that open ports are exploitable by malicious parties because of bugs and other security-related issues. That’s why a port scanner like nmap is an essential security-audit tool, as it quickly finds out which ports are open on a given IP.
If we have open ports but don’t know the reason for them, we must check the cause and take steps to close them.
A closed port indicates that no application or service is listening for connections on that port or that a firewall denies our connection attempts even in the presence of an active service. For example, a firewall’s rule can make a particular port accessible only to a predetermined set of IP addresses.
The downside of a closed port is that it confirms that “someone is listening.” Otherwise, there would be no response to the connection attempts. Malicious attackers can use this information, logging our machine’s presence for later examination when a new vulnerability is discovered.
A stealth port ignores unsolicited incoming packets without telling the sender whether the port is open or closed. When a networked device has only stealth ports and doesn’t reply to pings, it’s invisible to the random scans that continually sweep through the Internet. It’s as if it’s turned off, disconnected, or no longer existing.
GRC ShieldsUP! is a free online port scanning service we used for the following screenshots. It tests only TCP ports.
We performed the following two tests against an Ubuntu Server with a public IP. The test on the left refers to a standard setup with no firewall, SSH on port 22, and no other services. On the right, we configured and firewalled the same server to provide SSH on port 22 and VPN on port 443:
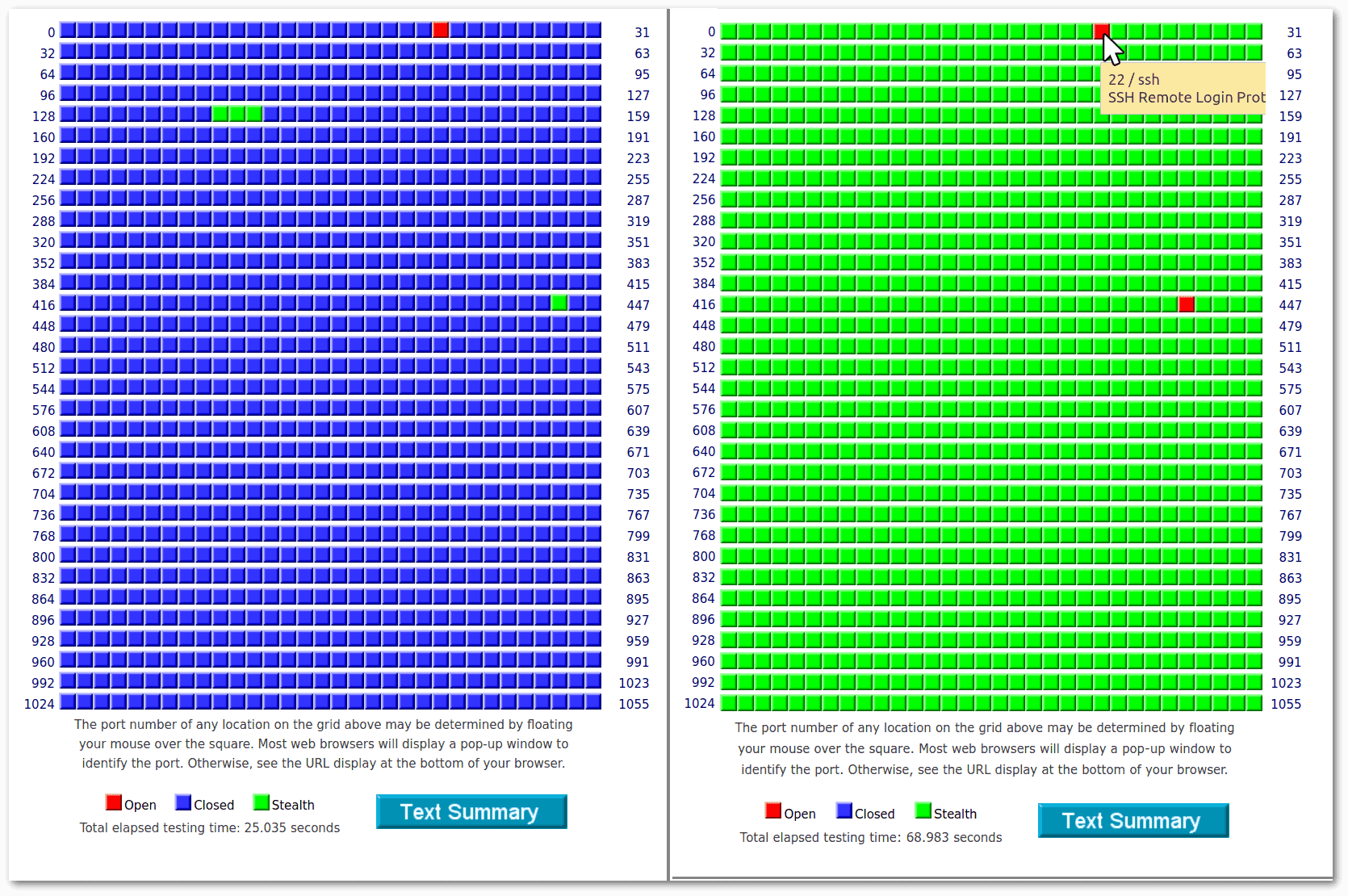 The configuration on the right is optimal because only the strictly necessary ports are open, and all others are stealth.
The configuration on the right is optimal because only the strictly necessary ports are open, and all others are stealth.
We used X11 forwarding to locally run our Ubuntu Server’s Firefox installation. In short, these three commands were enough (replacing x.x.x.x with the testing server’s IP):
$ ssh -Y -C [email protected]
[...]
root@TestGRC:~# export XAUTHORITY=$HOME/.Xauthority
root@TestGRC:~# firefox -no-remote https://www.grc.com/
[...]About ssh, -Y enables trusted X11 forwarding, and -C boosts performance by compression. The following export XAUTHORITY=$HOME/.Xauthority prevents a common authentication error in the X11 connection. Finally, although starting Firefox with -no-remote isn’t strictly necessary, it’s a good option in such cases.
We can consult the GRC’s Port Authority Database to get information about any port. Let’s suppose we are interested in port 111:
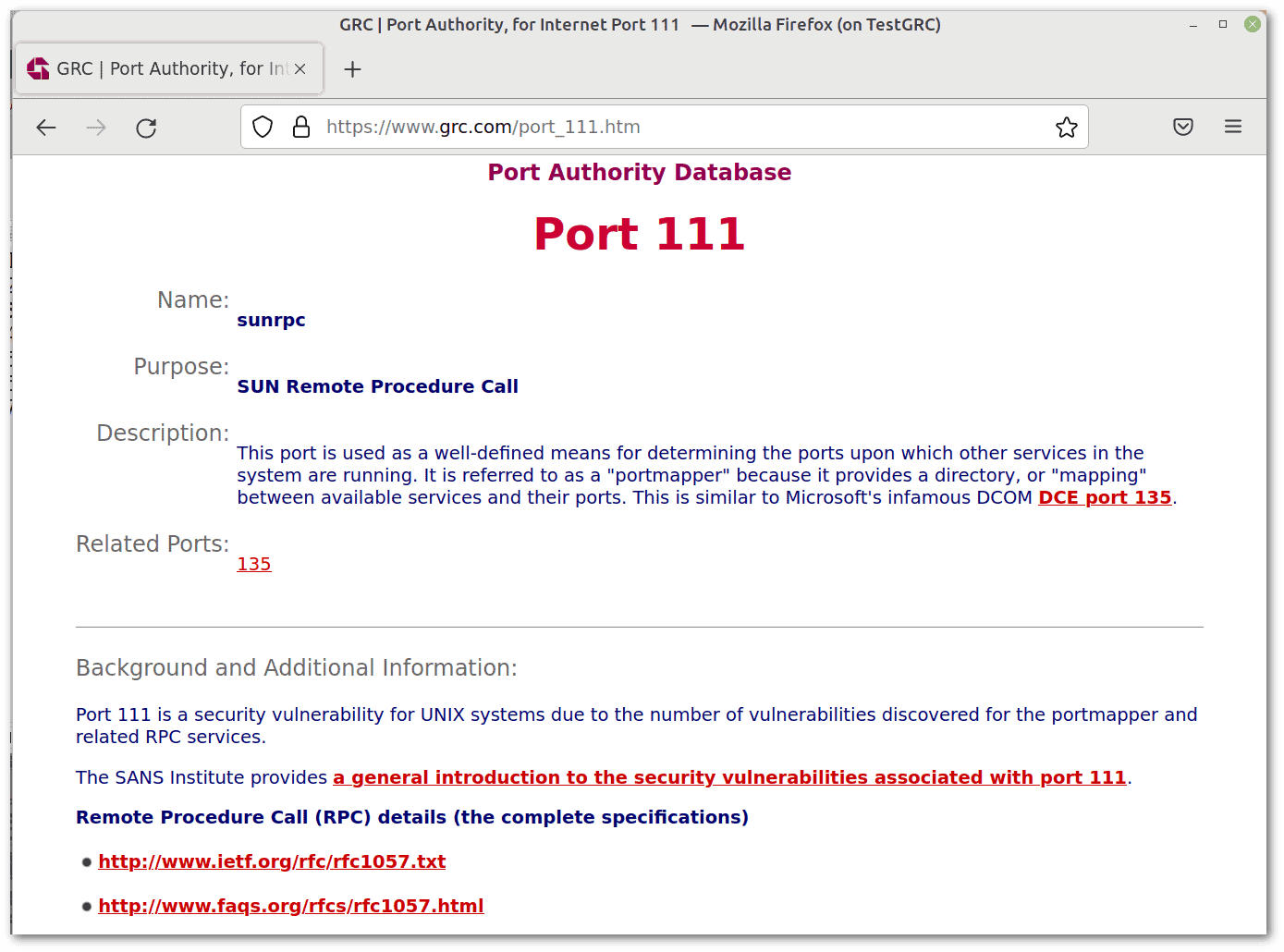 Let’s probe that port:
Let’s probe that port:
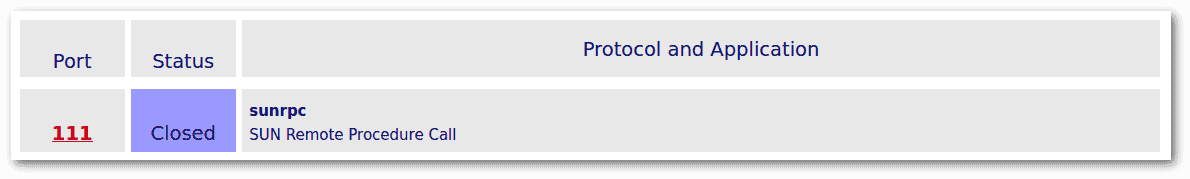 To perform this GRC’s test, we used X11 forwarding as before, with the same testing machine.
To perform this GRC’s test, we used X11 forwarding as before, with the same testing machine.
The main limitation of online services is that they can send packets only to public IPs or, as in the case of GRC, only to our own public IP. Instead, with command-line tools, we can probe even the private IPs of our LAN. So, let’s look at some Linux tools to ping a port, i.e., to probe it.
In the upcoming examples, we’ll use the following self-explanatory variables:
$ IP=78.141.212.157 # our testing machine's IP
$ PORT_OPEN=22
$ PORT_CLOSED=111
$ PORT_STEALTH=137In other words, we’ve configured our test machine so that TCP port 22 is open, 111 closed, and 137 stealth.
Pinging a port involves the transmission of TCP segments or UDP datagrams to that port. The usual strategy is to try to initiate a TCP connection. That’s why we’ll only test TCP ports, and this way is the default of most tools. Anyway, we can refer to the tools’ man pages to check if options related to UDP ports are available.
nmap is helpful for network exploration and security auditing. The -p option scans the specified ports:
$ nmap -p $PORT_OPEN,$PORT_CLOSED,$PORT_STEALTH $IP
[...]
PORT STATE SERVICE
22/tcp open ssh
111/tcp closed rpcbind
137/tcp filtered netbios-ns
[...]The outcome is the expected one for each port. nmap denotes as “filtered” the stealth port. Filtered means that a firewall, filter, or other network obstacle is blocking the port so that nmap can’t tell whether it’s open or closed. In essence, filtered and stealth are synonyms.
zenmap is an nmap frontend. Performing the same test, we can note good-looking output:
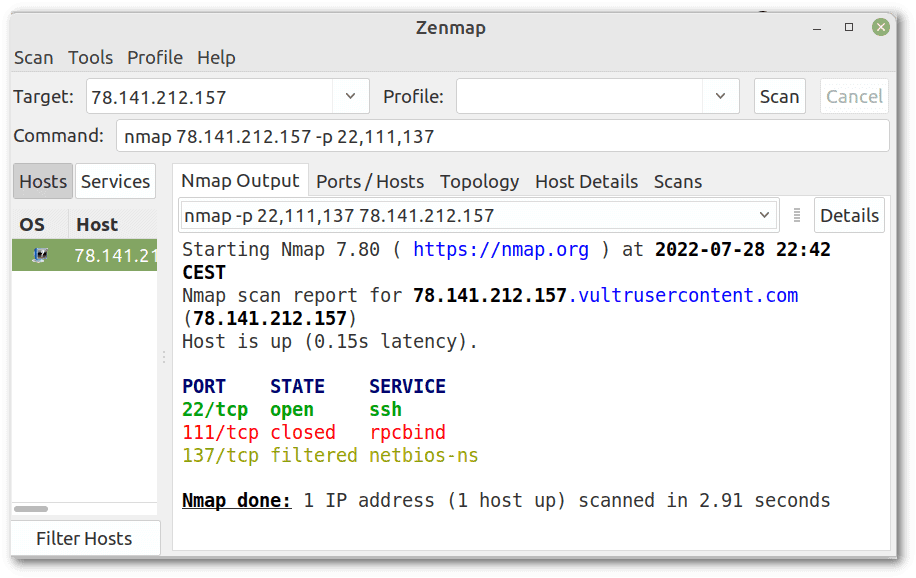 As a side note, sometimes zenmap isn’t trivial to install. Fortunately, many tutorials cover installation on the various Linux distributions.
As a side note, sometimes zenmap isn’t trivial to install. Fortunately, many tutorials cover installation on the various Linux distributions.
nping is a nmap tool for network packet generation, response analysis, and response time measurement.
Retrying the same test, we have more verbose output:
$ nping -p $PORT_OPEN,$PORT_CLOSED,$PORT_STEALTH $IP
[...]
SENT (0.0013s) Starting TCP Handshake > 78.141.212.157:22
RCVD (0.0715s) Handshake with 78.141.212.157:22 completed
SENT (1.0040s) Starting TCP Handshake > 78.141.212.157:111
RCVD (1.0767s) Possible TCP RST received from 78.141.212.157:111 --> Connection refused
SENT (2.0071s) Starting TCP Handshake > 78.141.212.157:137
[...]
TCP connection attempts: 15 | Successful connections: 5 | Failed: 10 (66.67%)
Nping done: 1 IP address pinged in 15.04 secondsAs expected, the handshake succeeded with port 22 (open), the connection was rejected with port 111 (closed), and there was no response from port 137 (stealth). By default, all tests are repeated five times. That’s why we have 15 connection attempts (5 × 3 ports).
The nc or netcat command is a command-line utility for reading and writing data between two computer networks. It has rich connection troubleshooting features and scripting usability.
Let’s repeat our test:
$ nc -vz $IP $PORT_OPEN
Connection to 78.141.212.157 22 port [tcp/ssh] succeeded!
$ nc -vz $IP $PORT_CLOSED
nc: connect to 78.141.212.157 port 111 (tcp) failed: Connection refused
$ nc -vz $IP $PORT_STEALTH
^C
Once again, the results are as expected. However, the last command doesn’t terminate because the stealth port doesn’t respond, and the netcat has no timeout as default. We, therefore, terminated it with CTRL+C.
The telnet command is a user interface to the Telnet protocol. In this case, we just want to see if we can make a connection:
$ telnet $IP $PORT_OPEN
Trying 78.141.212.157...
Connected to 78.141.212.157.
Escape character is '^]'.
SSH-2.0-OpenSSH_7.6p1 Ubuntu-4ubuntu0.7
^]
telnet> quit
Connection closed.
$ telnet $IP $PORT_CLOSED
Trying 78.141.212.157...
telnet: Unable to connect to remote host: Connection refused
$ telnet $IP $PORT_STEALTH
Trying 78.141.212.157...
^CIt works as expected. Similar to netcat, telnet remains indefinitely on hold when we attempt to contact a stealth port. We, therefore, terminate it with CTRL+C.
We also note that our SSH server gives telnet exact information about which service is listening on port 22, complete with operating system and software version. This data, of course, has security implications in case there are known exploits for this specific version.
curl is a widely used Linux tool for sending HTTP(S) requests and viewing the responses. We can still use it to ping a port:
$ curl $IP:$PORT_OPEN
curl: (1) Received HTTP/0.9 when not allowed
$ curl $IP:$PORT_CLOSED
curl: (7) Failed to connect to 78.141.212.157 port 111: Connection refused
$ curl $IP:$PORT_STEALTH
^CThe first answer doesn’t make much sense because we have sent an HTTP request to an SSH server. However, it’s a sufficient response to discover that the port is open. The closed port and the stealth port behave as in the previous cases.
Anyway, using curl makes more sense with the protocols it supports.
hping3 sends arbitrary TCP/IP packets to network hosts. Let’s try it, being careful that we need root permissions this time:
# hping3 $IP -S -V -p $PORT_OPEN -c 1
using tun0, addr: 10.8.0.2, MTU: 1500
HPING 78.141.212.157 (tun0 78.141.212.157): S set, 40 headers + 0 data bytes
len=44 ip=78.141.212.157 ttl=50 DF id=0 tos=0 iplen=44
sport=22 flags=SA seq=0 win=42340 rtt=71.6 ms
seq=1471141328 ack=1474234392 sum=6532 urp=0
--- 78.141.212.157 hping statistic ---
1 packets transmitted, 1 packets received, 0% packet loss
round-trip min/avg/max = 71.6/71.6/71.6 ms
# hping3 $IP -S -V -p $PORT_CLOSED -c 1
[...]
1 packets transmitted, 1 packets received, 0% packet loss
[...]
# hping3 $IP -S -V -p $PORT_STEALTH -c 1
[...]
1 packets transmitted, 0 packets received, 100% packet loss
[...]It’s very similar to the classic ping. However, we cannot distinguish between open and closed ports, but only between ports that respond (and thus open or closed) and ports that don’t respond (and thus stealth).
In this article, we looked at the difference between open, closed, and stealth ports and saw various ways to ping them.
It’s worth noting that port scanning and port probing can have legal consequences. The legality and ethics of these actions vary depending on the circumstances.