Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
In this tutorial, we’ll learn about TLS/SSL cipher suites. Additionally, we’ll look at two different methods to obtain the list of client’s cipher suites.
Transport Layer Security (TLS) and Secure Socket Layer (SSL) are both methods for securing a socket connection between two nodes talking over the public network. The difference between these two protocols is that the SSL is mostly deprecated and has been replaced by the TLS.
For the sake of brevity, we’ll just refer to the TLS protocol as it is now the de facto standard, but the same can generally be applied to SSL unless otherwise specified.
To establish a secure channel, the client and server undergo a handshake process. During the process, they have to agree on a cipher suite. The cipher suite defines several algorithms for key exchange, encryption, message integrity checking, and authentication.
The combination of the different algorithms makes up one specific cipher suite. For example, the TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 cipher suite tells us it’s a TLS cipher suite. Then, from the name, we can also see that it uses the ECDHE as its key exchange algorithm and ECDSA as its authentication algorithm. Furthermore, the AES_128_GCM is the bulk encryption algorithm. Finally, the cipher suite uses the SHA256 algorithm to hash the message for integrity-checking purposes.
However, not all the cipher suites will have a key exchange and authentication algorithm. For example, the TLS_AES_128_GCM_SHA256 only has the encryption and message hashing algorithm. This makes it hard to accurately interpret the algorithms in the cipher suite. Fortunately, we can use the ciphersuite.info website to interpret the cipher suite name.
When the client initiates the handshake process, it provides a list of cipher suites it supports to the server. Specifically, the client sends the Client Hello packet to the server, telling the TLS version to use as well as the list of supported cipher suites. The server will then choose one from the list to be used for subsequent communication.
There are mainly two different ways to get the list of client cipher suites. We can either capture and inspect the Client Hello packet that is sent to the server, or we can use a website like www.howsmyssl.com that inspects the handshake and shows us the details. Let’s look at the different methods in detail.
On a high level, the idea is to first capture the Client Hello packet that we send to the server. Then, we extract the list of the cipher suites from the TLS payload in the captured packet. To do that, we can use the tcpdump command-line tool in Linux for capturing packets and the tshark command for inspecting the packet.
Firstly, we’ll need to install the tcpdump command-line tool in our system. We can use the package manager on our system to install the tcpdump package:
$ sudo apt-get install -y tcpdumpThen, we start a tcpdump process with a filter to ensure that we’re only capturing the Client Hello message:
$ tcpdump "tcp port 443 and (tcp[((tcp[12] & 0xf0) >>2)] = 0x16) && (tcp[((tcp[12] & 0xf0) >>2)+5] = 0x01)" -w client-hello.pcapThe command above starts the packet capture process and writes all the packets into the client-hello.pcap file. Additionally, we specify a pcap filter that matches the Client Hello packet.
The pcap filter consists of two components. The first component matches only packets that have their source or destination TCP port at 443, the HTTPS port. Then, the second part of the filter matches the packet if it contains the value 01 in the sixth data byte of the TCP packet. Together, they’ll ensure only the Client Hello packet is captured by the process. To understand how we derive the filter, check out the article Capturing SSL handshake using tcpdump.
With the packet captured, we can inspect the details using the tshark command. By default, the tshark prints the minimal information of the packet. To print the packet in its entirety, including the handshake information, we can pass the -V option on tshark:
$ tshark -r client-hello.pcap -V
Frame 1: 571 bytes on wire (4568 bits), 571 bytes captured (4568 bits)
Encapsulation type: Ethernet (1)
Arrival Time: Sep 23, 2023 03:38:49.853913000 GMT
...
Transport Layer Security
TLSv1 Record Layer: Handshake Protocol: Client Hello
Content Type: Handshake (22)
Version: TLS 1.0 (0x0301)
Length: 512
Handshake Protocol: Client Hello
Handshake Type: Client Hello (1)
Length: 508
Version: TLS 1.2 (0x0303)
...
Cipher Suites Length: 62
Cipher Suites (31 suites)
Cipher Suite: TLS_AES_256_GCM_SHA384 (0x1302)
Cipher Suite: TLS_CHACHA20_POLY1305_SHA256 (0x1303)
Cipher Suite: TLS_AES_128_GCM_SHA256 (0x1301)
...To make it more script-friendly, we can print the output in JSON format instead with the -T json option. Then, using the jq command-line tool, we can select the list of cipher suites:
$ tshark -r client-hello.pcap -T json -V --no-duplicate-keys | jq '.[]._source.layers.tls."tls.record"."tls.handshake"."tls.handshake.ciphersuites"."tls.handshake.ciphersuite"'
[
"4866",
"4867",
"4865",
...
]Note that we’ll have to specify the –no-duplicate-keys to prevent the tshark from printing JSON arrays incorrectly.
When printing to JSON, the tshark outputs the cipher suites in their decimal value. This decimal value is an enumeration value that ties to a specific cipher suite name. To convert the number into the cipher suite name, we’ll first have to convert the decimal to the hexadecimal equivalent. Then, we can look up the name that corresponds to the hexadecimal value on the IANA website.
www.howsmyssl.com is a website that checks how secure our TLS client is. Depending on the TLS version the client uses and the cipher suites offered, the website gives a rating ranging from “Probably Okay”, “Improvable”, and “Bad”.
Besides that, the site also displays the list of cipher suites that the client offers in the “Given Cipher Suites” section:
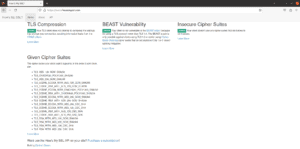
Through this section, we can get the list of our client’s cipher suites.
Furthermore, the site also offers a script-friendly API interface at www.howsmyssl.com/a/check. We can use the curl command to obtain the list of cipher suites offered by requesting the API interface:
$ curl https://www.howsmyssl.com/a/check | jq .
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 1459 100 1459 0 0 1529 0 --:--:-- --:--:-- --:--:-- 1527
{
"given_cipher_suites": [
"TLS_AES_256_GCM_SHA384",
"TLS_CHACHA20_POLY1305_SHA256",
"TLS_AES_128_GCM_SHA256",
...
],
...
"tls_version": "TLS 1.3",
"rating": "Probably Okay"
}In the command above, we use the jq command to better format the output. We can see that there’s the given_cipher_suites field that contains a list of the cipher suites our client (curl in this case) provides.
In this tutorial, we’ve learned how TLS and SSL provide a secure channel for communication between two nodes. Then, we’ve also learned that cipher suites contain a set of algorithms that are used for encryption and data message integrity validation purposes.
Subsequently, we’ve learned how we can inspect the Client Hello packet to get the list of cipher suites the client offers to the server. Specifically, we’ve learned how we can use the tcpdump and tshark to capture and inspect the packet to extract the list.
Finally, we’ve learned that the www.howsmyssl.com website offers both a graphical and API interface for obtaining the list of cipher suites our client offers.