Learn through the super-clean Baeldung Pro experience:
>> Membership and Baeldung Pro.
No ads, dark-mode and 6 months free of IntelliJ Idea Ultimate to start with.
Last updated: March 18, 2024
Currently, networked environments provide several services for end-users. There exist several applications running in these environments. These applications, in turn, enable users to, for example, communicate, shop, and study from a single place, just using a computer connected to the internet.
So, with numerous and different applications, it is natural that sensitive information passes through the networks. This sensitive information must be accessible only by authorized entities, keeping it secret from others.
In this context, cryptography plays an important role. Cryptography aims to secure data from being read by unauthorized entities. We can do it by executing a cryptography algorithm with plain data, which will transform the latter into a code hard to decipher without the proper key.
Particularly, when we talk about symmetric cryptography, we have to share the same key with all the authorized entities to encrypt and decrypt data. However, securely sharing a cryptographic key may be a challenge.
So, in this tutorial, we’ll study sharing methods of symmetric cryptography keys. First, we’ll briefly review cryptography, especially symmetric cryptography. Thus, we’ll investigate several strategies for sharing symmetric keys among authorized entities. Finally, we’ll compare the studied sharing strategies in a systematic summary.
As previously stated, cryptography has the main objective of securing data from being accessed by unauthorized entities. However, we have many categories of cryptography algorithms. The most known ones are asymmetric and symmetric cryptography.
The central difference between asymmetric and symmetric cryptography is the cryptographic keys. Asymmetric cryptography employs two keys: public and private. One key encrypts data, and another one decrypts data.
Symmetric cryptography, in turn, uses a unique key to both encrypt and decrypt data. In such a way, the entities that encrypt and decrypt data must access the same key to communicate.
The following figure shows the processes to encrypt and decrypt data in asymmetric and symmetric cryptography algorithms:
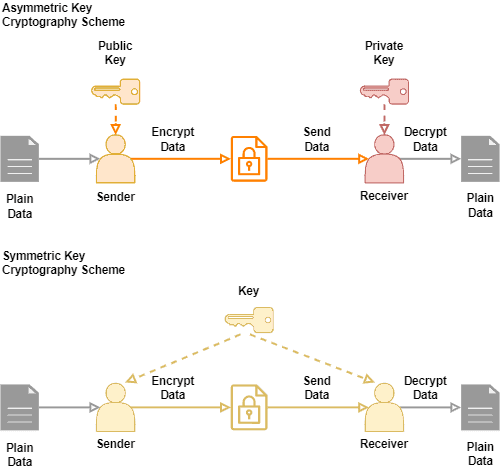
Asymmetric cryptography algorithms are very versatile, and the key distribution is easy. Symmetric algorithms, in turn, are typically faster (execution time) and simples than asymmetric algorithms.
However, a big challenge regarding symmetric algorithms is sharing a cryptographic key securely between authorized entities. In the following section, we’ll explore strategies to share symmetric keys.
First, we call key management all the processes of manipulating, storing, and sharing cryptographic keys. Moreover, the process of setting up a symmetric key for authorized entities is called cryptographic key establishment.
Currently, there exist several strategies to establish symmetric keys between authorized entities. So, let’s explore the most relevant key establishment strategies in the following subsections.
Key agreement protocols enable two unknown entities to establish a shared secret key and use it to communicate over an insecure channel. One popular key agreement protocol is Diffie-Hellman.
In the Diffie-Hellman protocol, two entities agree on using two values: the first value (p) is a prime number consisting of the modulo of a multiplicative group of integers, and the second value (g) is a primitive root modulo of the first value.
Each entity then chooses a secret value (let’s call them and
) and compute a number executing the following equation :
. Thus, each entity have as result the values we call
and
.
Finally, the entities exchange and
and derivate a common key using their own secret value and the received
value:
and
.
The image next shows the intuition of the Diffie-Hellman protocol using colors instead of numbers:
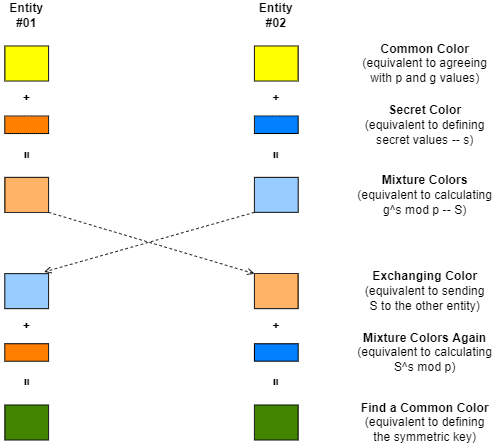
Besides the traditional Diffie-Hellman protocol, there exists the Elliptic-curve Diffie–Hellman. The first protocol employs modular arithmetic to compute the key, while the second uses algebraic curves.
The intuitive idea of key encapsulation is sending a letter to the authorized entity. However, the envelope to send the letter should be secure and verifiable.
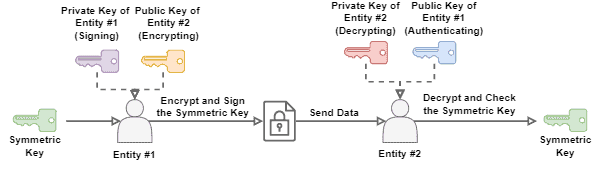
So, a key encapsulation mechanism creates this special envelope by using public and private keys of asymmetric cryptography.
In practice, one of the entities involved in communication creates the symmetric key and encrypts it using a public key provided by a second entity. Then, the first entity sends the encoded symmetric key to the second entity, which receives and decrypts it with the adequate private key.
In addition to simply encoding the symmetric key with a public key, the first entity can also sign the symmetric key with a private key. Thus, the first entity also provides a public key to the second one, enabling it to check the authenticity of the received symmetric key.
The following image exemplifies a possible process for key encapsulation:
Next, we can ask ourselves why not communicate with the public and private keys instead of using them to exchange symmetric keys. The answer to this question is that symmetric cryptography is typically more performative in encoding and decoding large messages.
In this way, for communications with intensive data exchanging, it is useful employing lightweight cryptography methods, such as the symmetric ones.
Out-of-band procedures consist of employing an alternative communication medium to the one used to exchange data for sharing a symmetric cryptographic key.
So, instead of the usual sending of cryptographic keys over the Internet, the entities involved in the process can share them through, for example, a telephone call or sending a letter in the traditional mail, or even meeting in person in real life.
We should note that it is hard to measure the security related to out-of-band procedures. In such a case, security depends on multiple aspects regarding the communication medium and how reliable the people involved in the transmission of the cryptographic key are.
Anyway, we assume that the probability of existing a malicious entity looking for cryptographic keys out the scope of networked connections is much smaller. Thus, out-of-band procedures may be appealing for use when they are practicable.
Symmetric cryptography methods present many benefits for telecommunications. For instance, these methods typically are more performative when cryptographing large messages than asymmetric cryptography methods.
However, the main challenge concerning symmetric cryptography is finding a secure way to share a cryptographic key. So, some strategies have been proposed over time to tackle this challenge.
Examples of sharing strategies are key agreement protocols, key encapsulation mechanisms, and out-of-band procedures. Each one of these strategies has particular characteristics. Some of them are summarized in the following table:
| Key Agreement Protocol | Key Encapsulation Mechanism | Out-of-Band Procedures | |
|---|---|---|---|
| Brief Definition | Each entity contributes to creating a cryptographic key by exchanging only non-compromising data | An entity uses another entity’s public key to securely share a symmetric key | Non-networked procedures to share a symmetric key |
| Uses Asymmetric Cryptography | No | Yes | No |
| Internet or Network Usage | Yes | Yes | No |
| Examples | Diffie-Hellman; Elliptic-curve Diffie–Hellman | Signing and encrypting with asymmetric keys | Meeting in real life; Traditional mail; Telephone call |
It is relevant to highlight that it is hard to define which of the presented strategies is the best. It will depend on the available resources and how the entities sharing a key relate to each other.
In this tutorial, we studied how to share symmetric keys for cryptography in a secure way. At first, we reviewed cryptography, focusing on symmetric methods. Next, we explored three strategies of symmetric key sharing: key agreement protocols, key encapsulation mechanisms, and out-of-band procedures. Finally, we briefly compared these strategies in a systematic summary.
We can conclude that sharing cryptographic keys is a real challenge in the digital world. But, with proper strategies, sharing symmetric keys and using symmetric cryptography becomes an excellent opportunity for enabling secure communications.